Implied rules of the UTM
Last adaptation to the version: 14.0.8.2 (08.2025)
New:
- Einstellungen für GeoIP Sperrungen verschoben zu IDS/IPS
This article refers to a Beta version
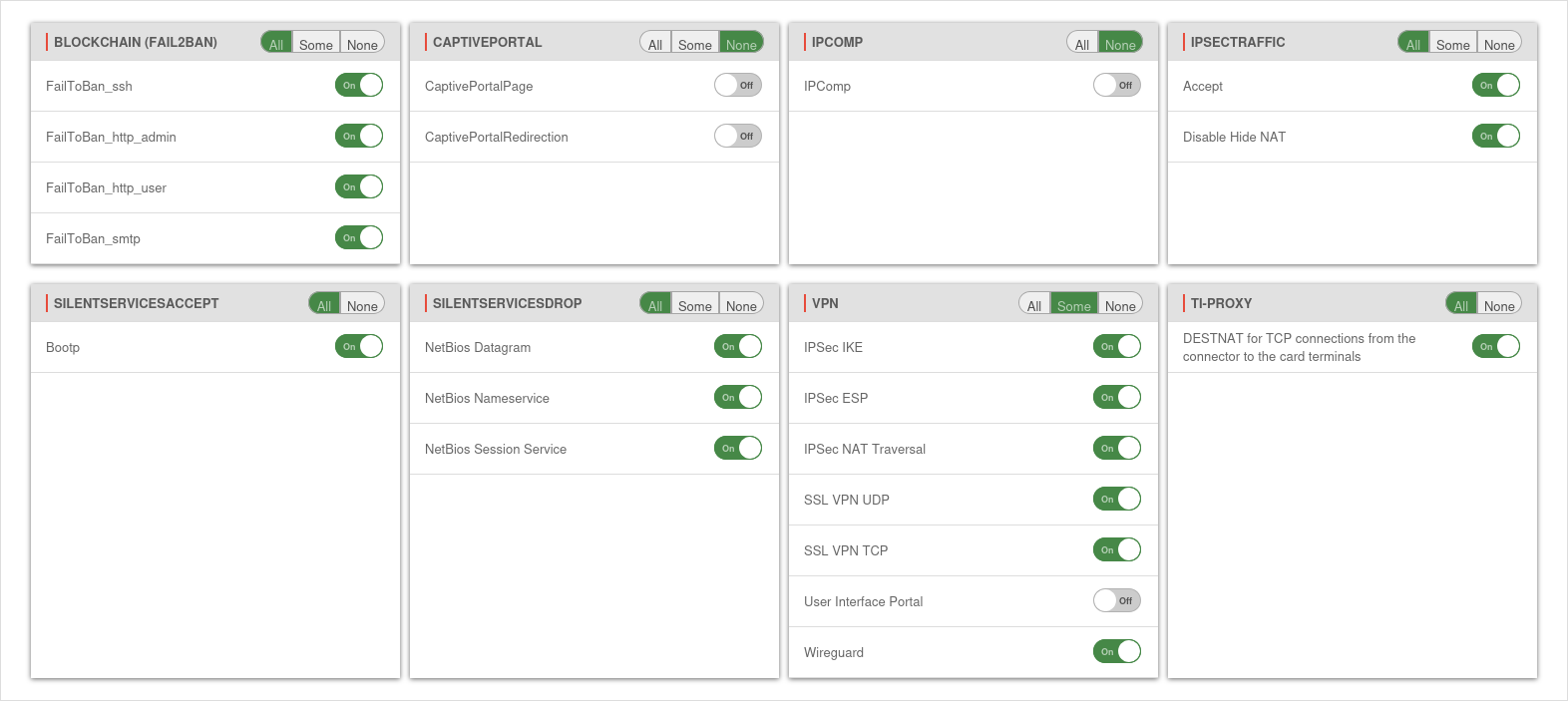
Implied rules
Settings in menu .
Implied rules have been added for certain use cases. These rules can be easily activated or deactivated by the user as needed. Some of these rules are already active by default.
The access zones are not relevant for these rules.
| Group / Rule | Description | Protocol | Port | Active (Default) |
|---|---|---|---|---|
| BlockChain | Activates / deactivates the entire group | |||
| FailToBan_ssh | Access via ssh.Monitoring with Fail2Ban rules. Configuration at |
TCP | 22 | On |
| FailToBan_http_admin | Access via the Admin Interface. Monitoring with Fail2Ban rules. Configuration at Port changes possible at |
TCP | 11115* | On |
| FailToBan_http_user | Access via the User interface. Monitoring with Fail2Ban rules. Configuration at Port changes possible at |
TCP | 443* | On |
| FailToBan_smtp | Access via the Mailgateway. Monitoring with Fail2Ban rules. Configuration at Port changes possible at Area Smarthost |
TCP | 25* | On |
| CaptivePortal | Enable redirection of traffic to a landingpage | |||
| CaptivePortalPage | Opens an incoming port on the corresponding interface of the firewall that is intended for the captive portal to display the landingpage. Port changes possible at Area Advanced |
TCP | 8085* | Off |
| CaptivePortalRedirection | Redirection of traffic to the above mentioned port. | Off | ||
| IPComp | ||||
| IPComp | Accepts connections with IPComp protocol (compression of data packets, IP protocol number 108) | IPComp | Off | |
| IpsecTraffic | Activates / deactivates the entire group | |||
| Accept | Accepts incoming and outgoing traffic of an IPSec connection. | On | ||
| No NAT for IPSec connections | Takes all IPSec connections from the NAT |
Off | ||
| Silent Services Accept | ||||
| Bootp | Accepts
|
UDP | 67 | On |
| 68 | ||||
| Silent Services Drop | ||||
| NetBios Datagram | Discards these packages without log message | UDP | 138 | On |
| NetBios Nameservice | Discards these packages without log message | UDP | 137 | On |
| NetBios Session Service | Discards these packages without log message | UDP | 139 | On |
| VPN | ||||
| IPSec IKE | Accepts connections on port 500/UDP | UDP | 500 | On |
| IPSec ESP | Accepts connections with the ESP protocol (50) | ESP | On | |
| IPSec NAT Traversal | Accepts connections on port 4500/UDP | UDP | 4500 | On |
| SSL VPN UDP | Accepts connections on ports for which an SSL VPN instance has been configured with the UDP protocol | UDP | 1194 | On |
| SSL VPN TCP | Accepts connections on ports for which an SSL VPN instance has been configured with the TCP protocol | TCP | 1194 | On |
| User Interface Portal | Accepts connections on port 443/TCP. Required for the user interface. | TCP | 443 | On |
| Wireguard | Enables connections with the Wireguard protocol. Port changes possible at button edit connection |
UDP | 51280* | On |
| TI-Proxy notempty New as of v14.0.7.2 |
||||
| DESTNAT for TCP connections from the connector to the card terminals | Erstellt und erlaubt eine Portweiterleitung von den IP-Adressen und Ports wie im TI-Proxy hinterlegt vom Konnektor per destnat zu den Kartenterminals (default: 60000→4742) | TCP | 60000 | On |