Configuration of Telematik Infrastruktur as a Service
New article with version: 14.0.0 (11.2024)
This article refers to a Beta version
-
RISE as TIaas-Provider
WireGuard Configuration
Configure TI-Proxy
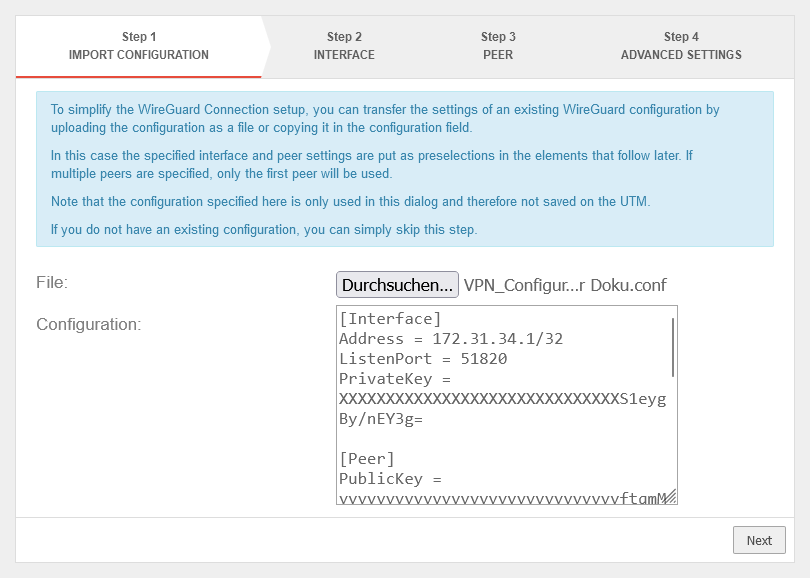
RISE provides a Connection.conf file, which contains the IP address of the connector.
Example Connection.conf:
tiaas:
wireguard:
ip: 172.31.34.1
client:
konnektor:
url: 10.180.96.90
# This is a template to be filled by the customer. Please consult the manual how to perform the configuration
#card-terminal:
The IP address of the connector is the value under tiaas → client → konnektor → url, i.e. here 10.180.96.90.
This IP address is then used to configure the TI proxy.
Best Practice
Dieser section zeigt eine Umsetzung, die sich in der Praxis bewährt hat. Die Konfiguration erhebt keinen Anspruch auf Vollständigkeit und Korrektheit.
Wir übernehmen keine Gewähr für etwaige Probleme oder Schäden, die direkt oder indirekt durch diese Konfiguration entstehen.
- Connect the card terminal: Via Assign a fixed lease to network topology
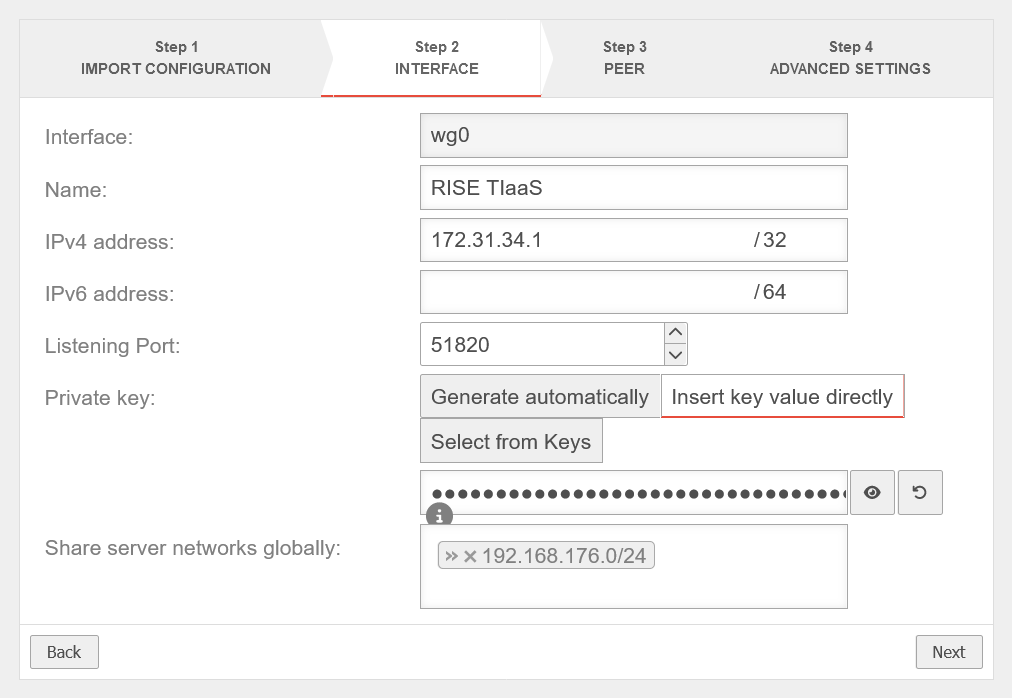
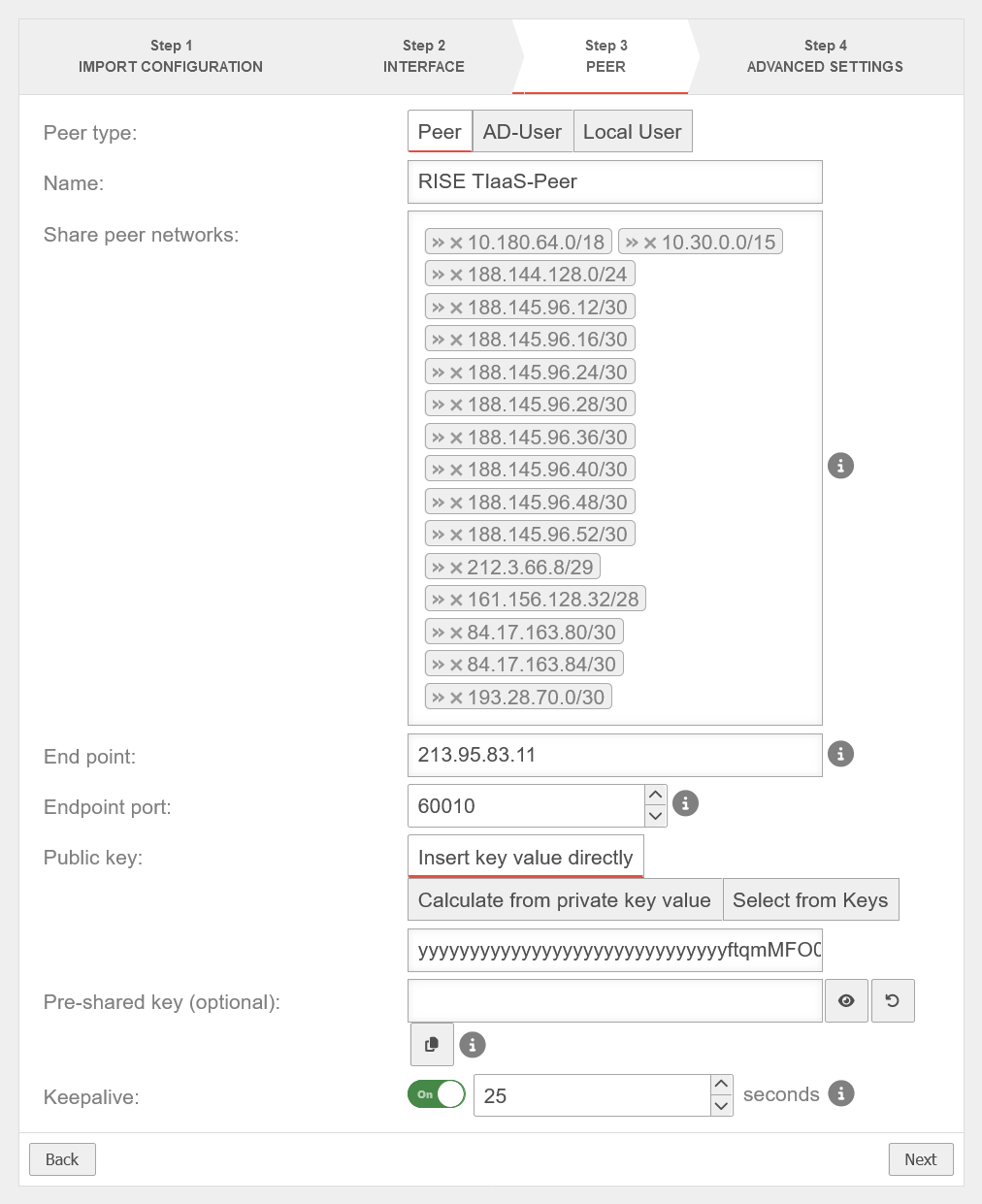
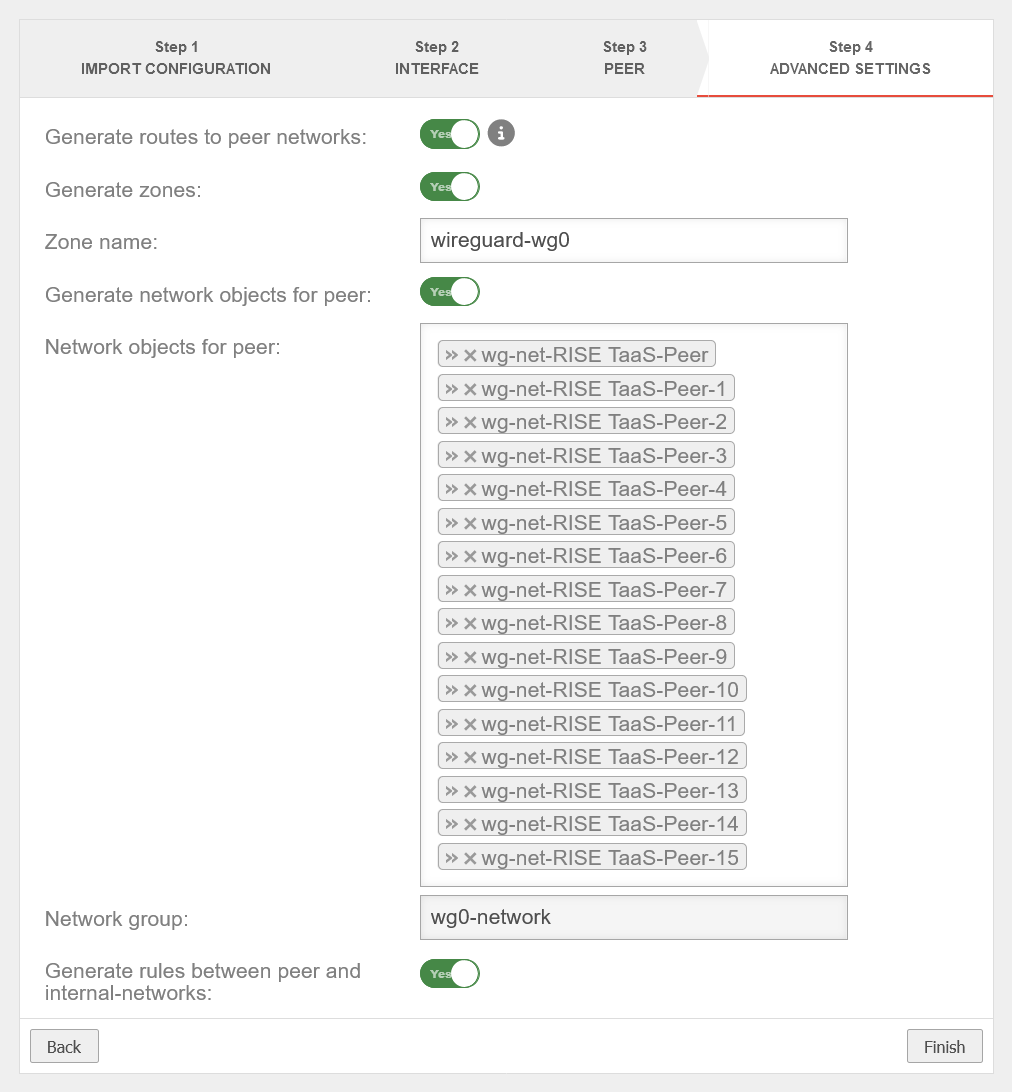
- Start the Wireguard Wizard and store the configuration from the provider on the UTM. Select all options in the last step of the wizard
- [UTM/RULE/Paketfilter#Netzwerkobjekte_erstellen_/_bearbeiten
- Create three services:
- Name: TI-Proxy-60000, Protocol: udp, Destination port: 60000
- Name: TI-Proxy-4742, protocol: udp, destination port: 4742
- Name: TI-Proxy-60000-TCP, protocol: tcp, destination port: 60000
- In Package filter, open the automatically created rule with the source internal-networks and the destination wg0-networks and add a HIDENAT to the wg0-interface
- In the packet filter, delete the rule that was also created automatically in the internal network.
Instead, create the following three rules:- source: internal-interface, destination: wg0-networks, service: TI-Proxy-4742, type: HIDENAT, network object: wg0-Interface
- source: wg0-networks, destination: wg1-interface, service: TI-Proxy-60000
- Source: wg0-networks, destination: wg1-interface, service: TI-Proxy-60000-TCP
- Enter data in the proxy
- Enter the virtual connector IP - in the example 10.180.96.90
- Enter the IP of the local wireguard interface (in this example 172.31.34.1)
- Enter the IP of the internal interface to which the card terminals are connected (here in the example 192.168.200.1)
- Create terminal on the connector (connector access in the example https://10.180.96.90:8443)
- The IP address is the wireguard address of the UTM: in the example 172.31.34.1
- Note
- The default port is 60000
- The Mac address is not required
- On the terminal, the trusted room may have to be set to RU in the admin menu under TSL list
- On the terminal, all trust blocks may have to be deleted in the Admin menu under Pairing
- Click on Pair in the connector
- Confirm on the terminal pair