notempty
Last adaptation to the version: 12.3.6
- DNS Relay for a WireGuard site-to-site tunnel
- Correction of the port filter rule for OpenVPN site-to-site tunnels
- Korrektur der Portfilterregel (Quelle und Ziel waren falsch)
- 02.2024
Introduction
In this scenario, the UTM and clients of a remote site are to be connected to the domain at the main site.
- All DNS requests for the domain to the DNS server, through the VPN tunnel, are forwarded to the main site.
- The UTM shall provide DNS for the clients in the remote site.
- Requests for the domain network shall be forwarded in the VPN tunnel to the DNS server in the main site.
Creating the DNS Relay Zone
Set the nameserver of the firewall
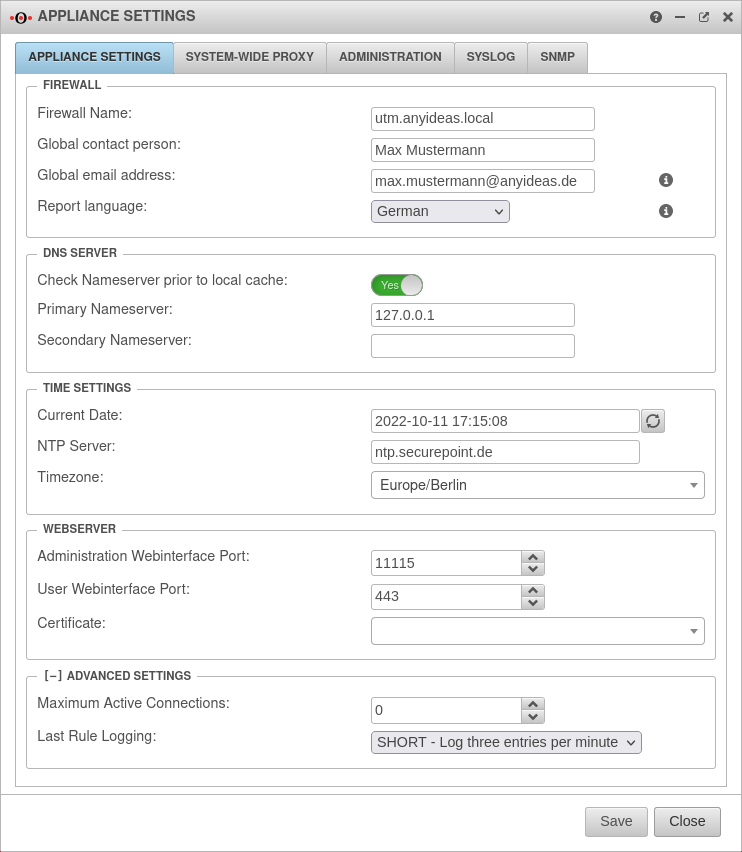
The first step is to set the nameserver of the firewall.
In the Primary nameserver field, enter 127.0.0.1 as the IP (localhost). Click on the button.
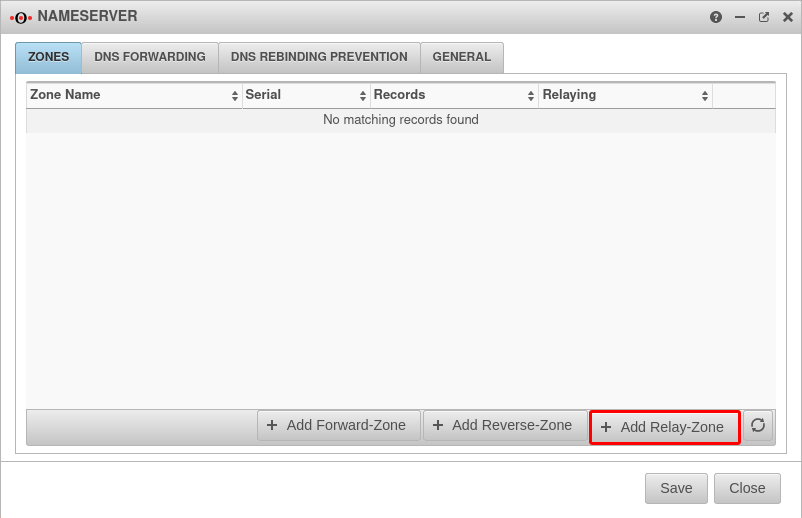
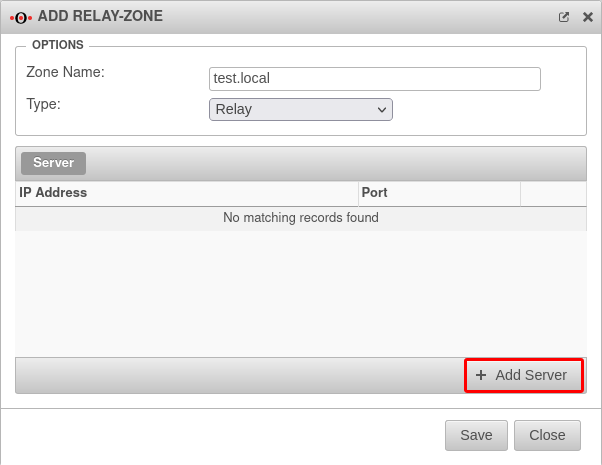
Create DNS Relay
Tab Zones
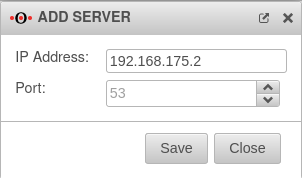
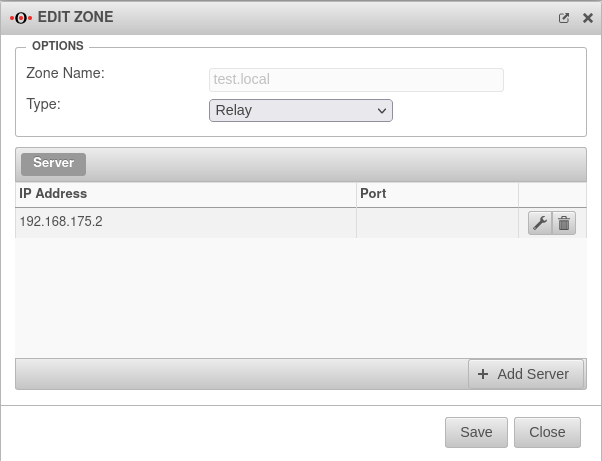
The next step is to create a relay zone.
After creating the relay zone, the firewall forwards all requests to the DNS server at the main site on the domain network.
DNS Relay for an IPSec Site-to-Site Tunnel
In order to forward internal domain requests to a remote nameserver that is on an IPSec network, note that by default, all direct requests addressed to external nameservers are sent from the firewall with the external IP. However, a public IP is not routed into an IPSec tunnel.
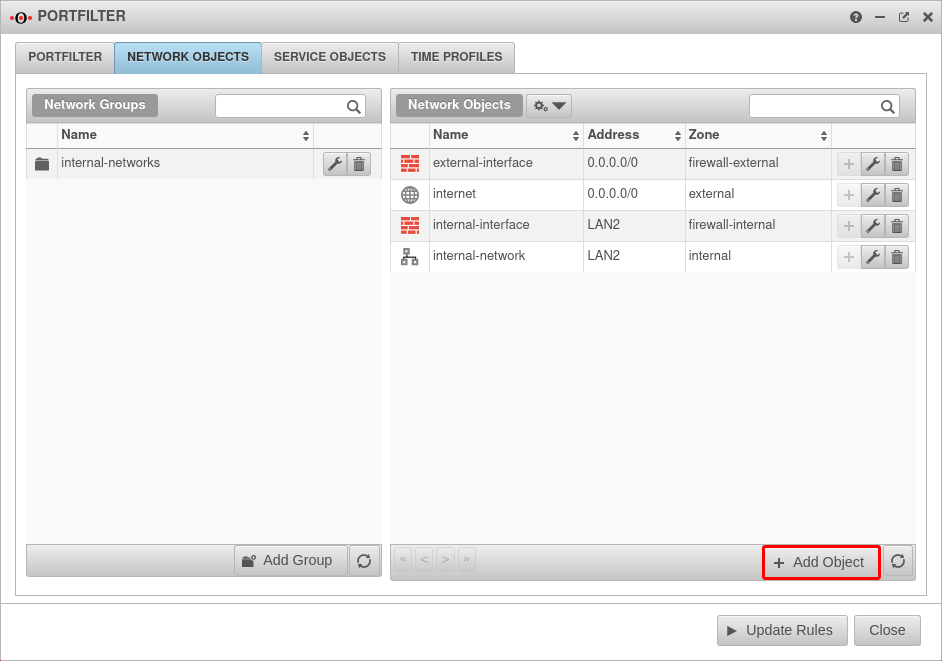
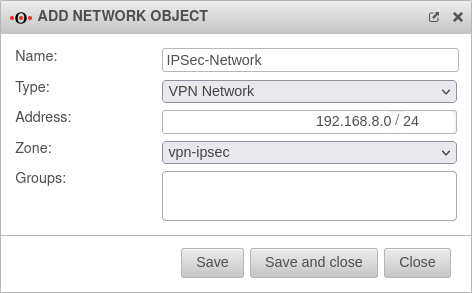
Create network object
Tab Network objects
The port filter rules in the Implied rules are automatically activated. This means that no network object is yet available for the IPSec network.
Click , or to save this network object.
After the network object is created, is clicked.
Create a rule
Tab Add rule Button
The last step is to create a firewall rule with a Hide NAT.
This causes DNS forwarding to also go to the tunnel and not directly to the Internet.
| Labeling | Value | 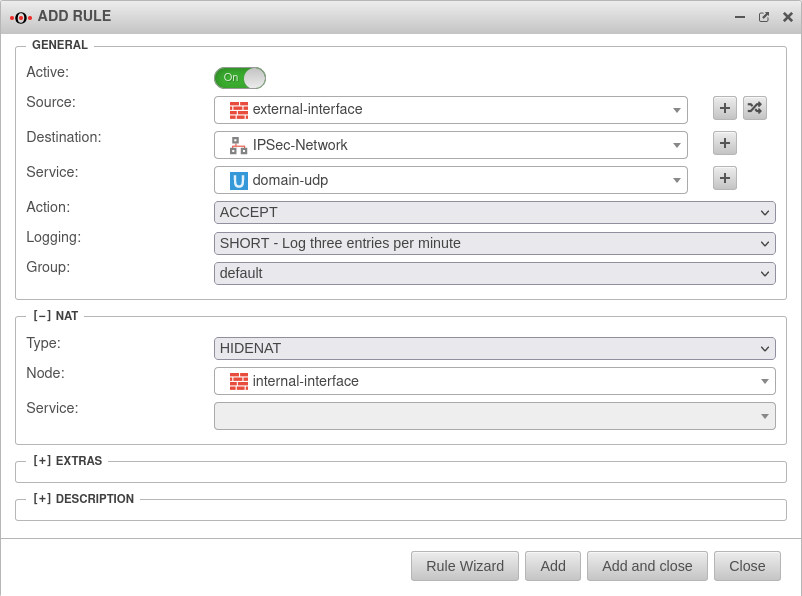 |
|---|---|---|
| Active: | On | |
| Source: | ||
| Destination: | ||
| Service: | ||
| Action: | ||
[-] NAT
| ||
| Type: | ||
| Network object: | ||
Click or to save this rule.
With this rule, all domain UDP requests made through the firewall to the remote nameserver are natted over the IP of the internal interface and can thus be routed into the IPSec tunnel.
DNS Relay for an OpenVPN Site-to-Site Tunnel
In order to forward internal domain requests to a remote nameserver located in an OpenVPN network, note that by default all direct requests directed to external nameservers are send from the firewall with the external IP. However, a public IP is not routed into an OpenVPN tunnel.
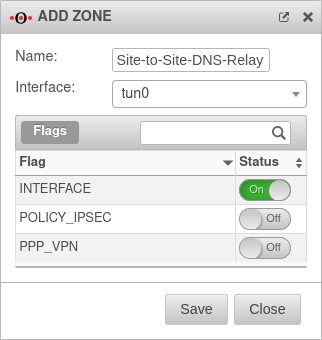
Create zone
In order to route the DNS requests into the OpenVPN tunnel, a new interface zone must be created on the UTM.
A new zone is created with the button.
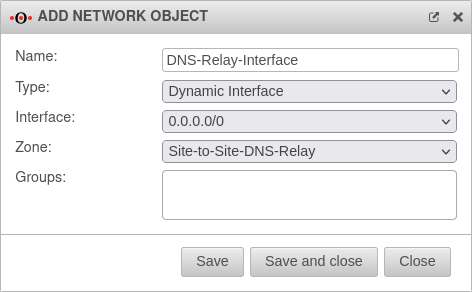
Create Open-VPN network objects
Tab Network objects
The port filter rules in the Implied rules are automatically activated. This means that no network object is yet available for the Open-VPN network.
Click , or to save this network object.
After the network object is created, is clicked.
Create rule
Tab Add rule Button
The last step is to create a firewall rule with a Hide NAT.
This causes DNS forwarding to also go to the tunnel and not directly to the Internet.
| Labeling | Value | Datei:UTM v12.3.6 Firewall Portfilterregel DNS Relay -en.png |
|---|---|---|
| Active: | On | |
| Source: | ||
| Destination: | ||
| Service: | ||
| Action: | ||
[-] NAT
| ||
| Type: | Optional if domain controller does not want to respond to requests from the transfer network | |
| Network object: | ||
Click or to save this rule.
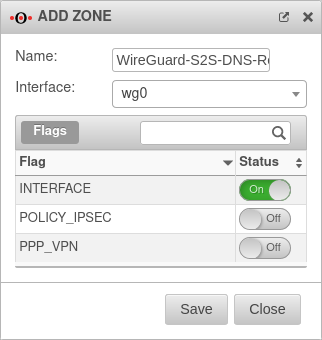
DNS Relay for a WireGuard Site-to-Site Tunnel
The internal domain requests can also be forwarded to a remote nameserver located in a WireGuard network. The configuration of such a scenario requires an existing WireGuard site-to-site VPN (S2S) connection.
Create zone
Button
In order to route the DNS requests into the WireGuard tunnel, a new interface zone must be created on the UTM.
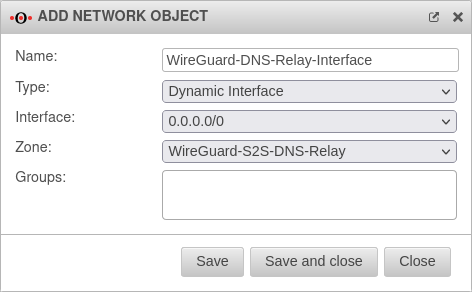
Create WireGuard network objects
Tab Network objects
The port filter rules in the Implied rules are automatically activated. This means that no network object is yet available for the WireGuard network.
Click , or to save this network object.
After the network object is created, is clicked.
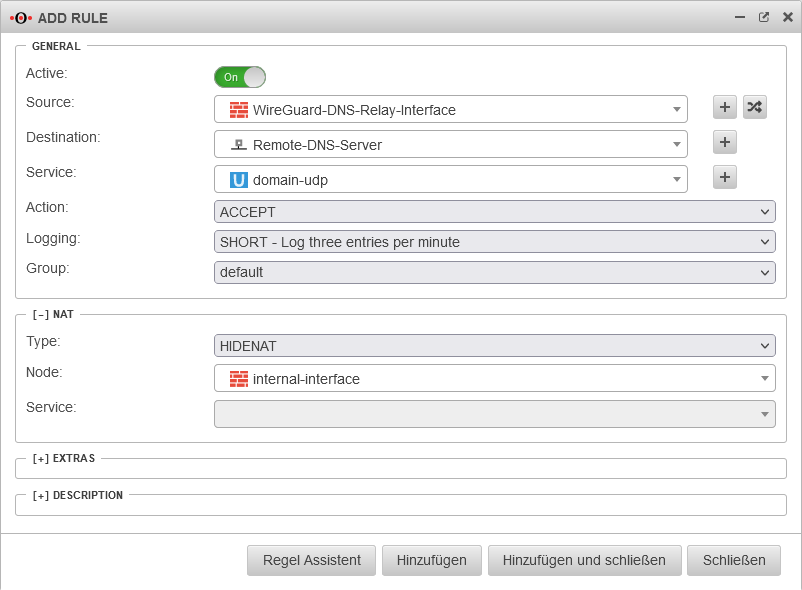
Create rule
Tab Add rule Button
The last step is to create a firewall rule with a Hide NAT.
This causes DNS forwarding to also go to the tunnel and not directly to the Internet.
Click or to save this rule.