In dieser Seite werden die Variablen für unterschiedliche Sprachen definiert.
Diese Seite wird auf folgenden Seiten eingebunden
 Network sketch Initial position
Network sketch Initial position
Using an SSL VPN Roadwarrior to Access a Network Behind an IPSec Site-to-Site Connection
Last adaptation to the version: 12.6.0
New:
- Updated to Redesign of the webinterface
Last updated:
02.2025
- Example adapted to Best Practice (graphic, locations, IP addresses)
This article refers to a Beta version
Initial position
- A network at location A is connected to a network at location B via an IPSec site-to-site connection
- There is an SSL VPN connection from a Roadwarrior to the network at location B
Goal:
- The internal network at location A should be accessible for the roadwarrior via the SSL VPN connection to location B
Configuration:
- Location A:
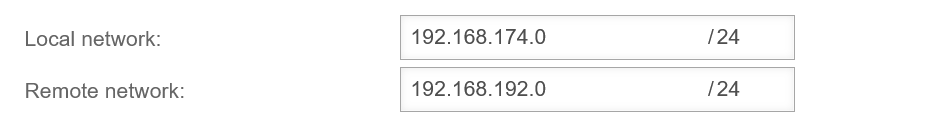
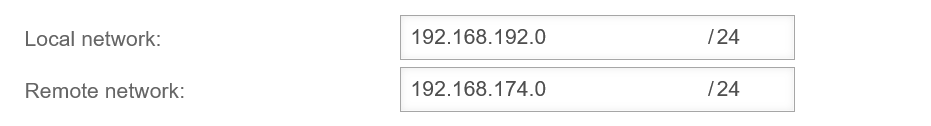
Internal network: 192.168.174.0/24
- location B:
Internal network: 192.168.175.0/24
- Roadwarrior:
SSL VPN connection to location B
Transfer network IP: 192.168.192.0/24
Set up IPSec site-to-site connection
A guide to configure an IPSec site-to-site connection is available in this wiki.
Set up SSL-VPN connection
A guide to configure an SSL VPN connection for roadwarriors can be found in this wiki.
Adjust the configuration
Edit SSL-VPN connection
Location B
Customize the SSL VPN Roadwarrior connection under button of the used connection, General tab.
| Caption |
Value |
Description
|
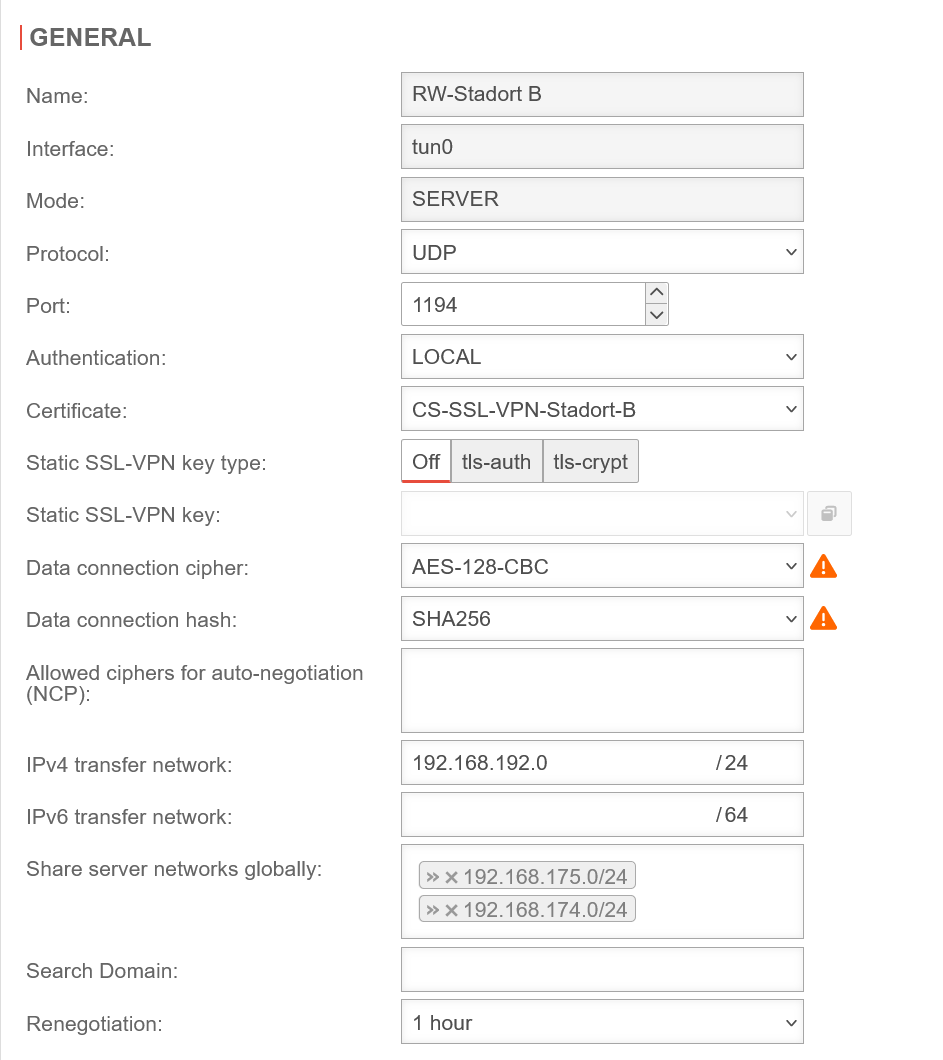 Add server networks Add server networks
|
| Share server networks: |
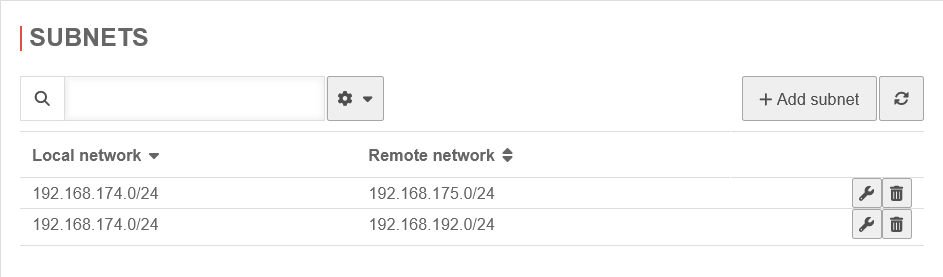
»192.168.175.0/24»192.168.174.0/24 |
In this example, the internal network of location B (192.168.175.0/24) has already been released by the SSL VPN connection.
Additionally', the internal target network at location A, which is to be accessed by the Roadwarrior, must now be released.
|
| Save and close |
Accept specifications with the Save button
|
| Restart SSL VPN connection with the Restart button.The SSL VPN connection on the Roadwarrior must be terminated and reestablished once to push the new server network
|
|
|
Configuration with adjustment of the IPSec connection
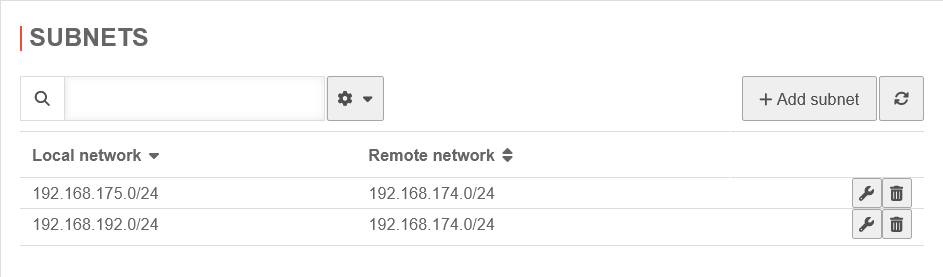
The Roadwarrior's transfer network must be entered on both UTMs' in phase 2 of the IPSec connection.
Configuration under Button Phase 2 of the connection used, tab Subnets, button AddIPSec Connection
Adjusting the IPSec connection
Internal target network that the Roadwarrior should be able to access
Location A
This rule is not required if the IPSec connection was allowed via implicit rules.
However, this is usually not recommended, since implicit rules allow the ports used for IPSec connections to all interfaces.
Create packet filter rule in button Add object tab.
| Caption |
Value |
Description
|
|
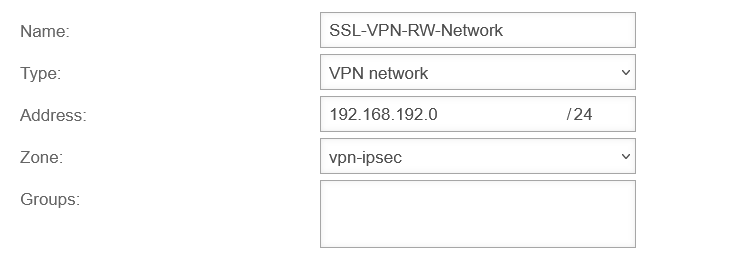
| Name |
SSL-VPN-RW-Network |
name freely selectable
|
| Type: |
VPN-network |
Even if it is only a single roadwarrior, a tunnel net IP is used for the connection. Therefore, the type Network must be selected here.
|
| Address: |
192.168.192.0/24 |
The net IP of the SSL-VPN Transfer network from location B
|
| Zone: |
vpn-ipsec |
The zone corresponds to the IPSec connection
|
| Groups: |
|
If necessary, the network object can be added to a group
|
| Save and close |
Save and add network object with this button
|
|
|
| Caption |
Value |
Description
|
|
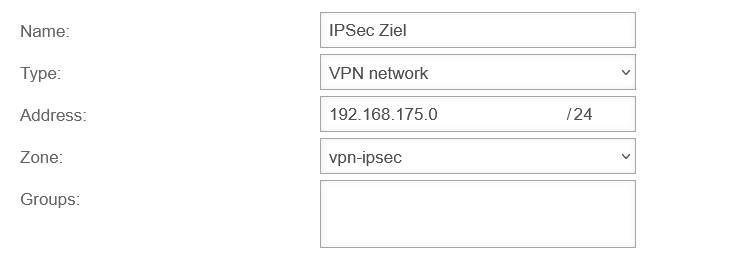
| Name: |
IPSec target |
name freely selectable
|
| Type: |
VPN network |
|
| Address: |
192.168.175.0/24 |
The net IP of the internal target network to be accessed
|
| Zone: |
vpn-ipsec |
The zone corresponds to the IPSec connection
|
| Groups: |
|
If necessary, the network object can be added to a group
|
| Save and close |
Save and add network object with this button
|
|
|
Packet filter rule location A
| Quelle |
 SSL-VPN-RW-Network SSL-VPN-RW-Network |
Network object of the Roadwarrior network
|
| Target |
 internal-network internal-network |
Internal target network that the Roadwarrior should be able to access
|
| Service |
 xyz xyz |
Desired service or service group
|
|
|
Display of the packet filter rule in the overview
The rule is not applied until the Update rules button is pressed!
Create a network object at location B
Location B
Create a network object for the target network under button Add Object
| Caption |
Value |
Description
|
|
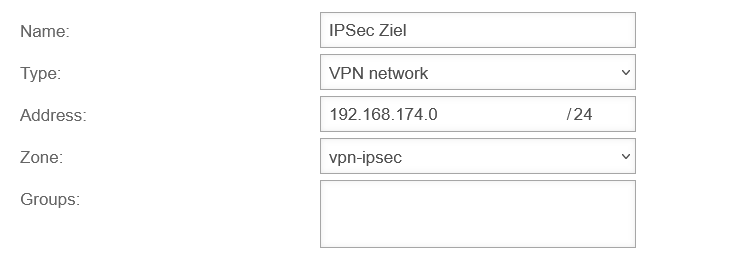
| Name: |
IPSec target |
name freely selectable
|
| Type: |
VPN network |
|
| Address: |
192.168.174.0/24 |
The net IP of the internal target network to be accessed
|
| Zone: |
vpn-ipsec |
The zone corresponds to the IPSec connection
|
| Groups: |
|
If necessary, the network object can be added to a group
|
| Save and close |
Save and add network object with this button
|
|
|
Packet filter rule location B
| Quelle |
 SSL-VPN-RW-Network SSL-VPN-RW-Network |
Network object of the Roadwarrior network
|
| Target |
 IPSec target IPSec target |
Network that should be accessed
|
| Service |
 xyz xyz |
Desired service or service group
|
Save the rule with the Save and close button.
Display of the packet filter rule in the overview
The rule is not applied until the Update rules button is pressed!
Configuration with HideNat rule
If there is no access to the configuration at location A, a rule with HideNat can also be applied. This then replaces the transfer of the network IP of the SSL VPN remote network in phase 2 of the IPSec connection.
notemptySince IP addresses are exchanged in this process, this can lead to problems with VoIP or FTP, for example.
Create a network object at location B
Location B
Create a network object for the target network under button Add Object
| Caption |
Value |
Description
|
|
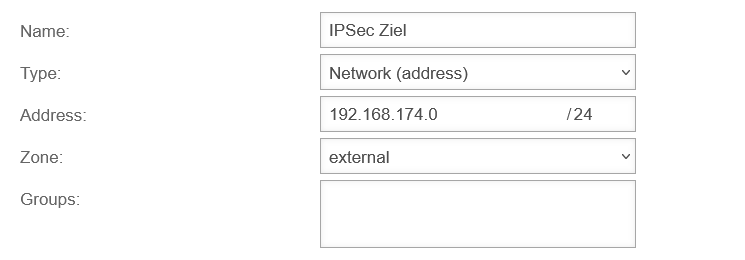
| Name: |
IPSec target |
name freely selectable
|
| Type: |
Network (address) |
Important: The SSL VPN connection does not realize that this is another VPN connection.
Therefore, no VPN network should be selected here!
|
| Address: |
192.168.174.0/24 |
The net IP of the internal target network to be accessed
|
| Zone: |
external |
external
|
| Groups: |
|
If necessary, the network object can be added to a group
|
| Save and close |
Save and add network object with this button
|
|
|
Packet filter rule location B