New article: 11.2024
Preliminary Note
This article aims to describe a simple, concise, and practical method for setting up a WireGurad connection, regardless of whether the peers are S2S (Site-to-Site) or E2S (End-to-Site).
In this Example, an S2S connection will be created between two UTMs (hereafter referred to as Location A and Location B). Additionally, a device from a home office will connect to Location A (referred to as Roadwarrior in the following).
Additionally, the following example configuration will be used:
| Location A | Location B | Roadwarrior | Transfer network | |
|---|---|---|---|---|
| FQDN | a.vpn.anyideas.de | b.vpn.anyideas.de | – | – |
| Local network IPv4 | 10.1.0.0/16 | 10.2.0.0/16 | – | 10.0.1.0/24 |
| Local tunnel IPv4 | 10.0.1.1/24 | 10.0.1.2/24 | 10.0.1.201/24 | – |
| Local network IPv6 | fd00:a:0:0::0/64 | fd00:b:0:0::0/64 | – | fd00:0:0:0::0/64 |
| Local tunnel IPv6 | fd00:0:0:0::1/64 | fd00:0:0:0::2/64 | fa00:0:0:0::C9/64 | – |
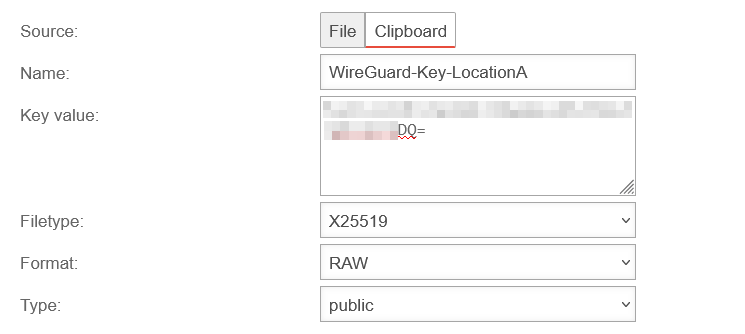
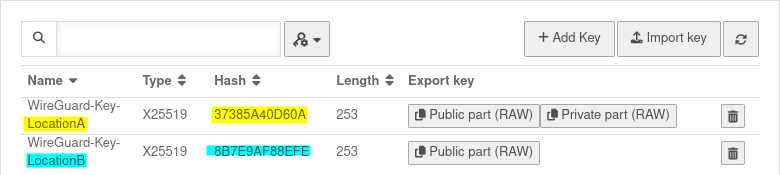
Key generation
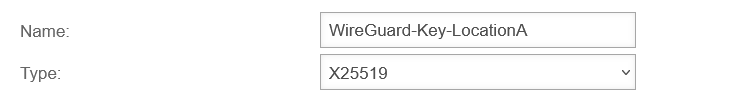
Location A Create WireGuard connections
Import Configuration | |||
|
UTMuser@firewall.name.fqdnVPNWireGuard 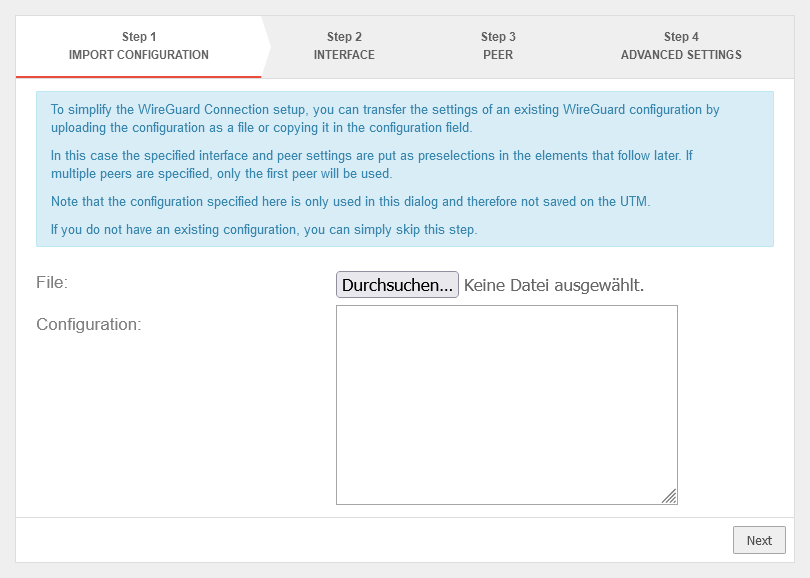 Location A If necessary, import configuration Location A If necessary, import configuration
| ||
Interface | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnVPNWireGuard 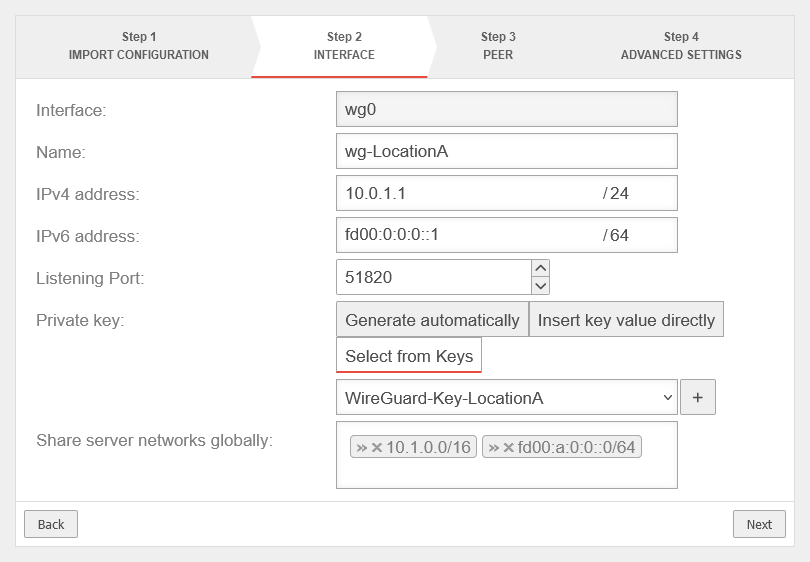 Location A Interface Configuration Location A Interface Configuration
|
|---|---|---|---|
| Name: | wg-LocationA | Connection Name | |
| IPv4 Address: | IPv4 address for the network interface of the transfer network at Location A This determines the Network IP on the transfer network (here: 10.0.1.0/24) | ||
| IPv6 Address: | IPv6 address for the network interface of the transfer network at Location A (optional) This determines the network IP of the transfer network (here: fd00:0:0:0::0/64) | ||
| Listening Port: | 51820 | Default port for WireGuard connections Each additional connection requires a different available port | |
| Private key: | Option: | ||
| Select the previously created key Only keys with a private key component are available for selection | |||
| Enable global access to server networks: | »10.1.0.0/16»fd00:a:0:0::/64 | Networks on the (local) server side that WireGuard tunnels of peer can generally access. | |
Peer | |||
| Name: | wg-PeerB | Name of Peer/ Remote Endpoint | UTMuser@firewall.name.fqdnVPNWireGuard 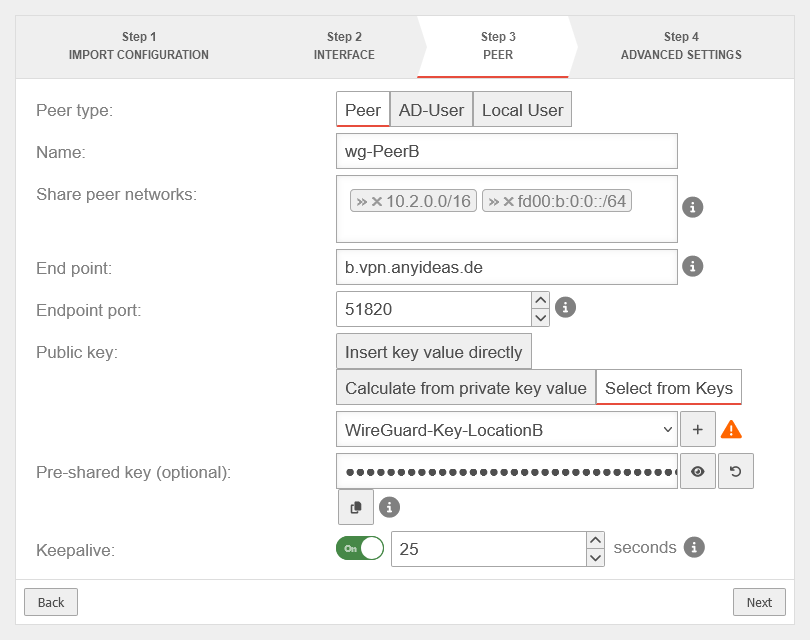 Location A Peer Configuration Location A Peer Configuration
|
| Share peer networks: | »10.2.0.0/16»fd00:b:0:0::/64 | Local network IPs of the remote endpoint that can access the WireGuad tunnel. | |
| Endpoint: | b.vpn.anyideas.de | Public IP or or FQDN of the remote endpoint that can be resolved via public DNS (here: Location B) | |
| Endpoint Port: | 51820 | Listening Port of the Remote Endpoint (here: Location B) | |
| Public key: | Select the public key of the remote connection (here: Location B) | ||
| Pre-Shared Key: | ●●●●●●●●●●●●●●●●● | Pre-Shared Key for additional connection security | |
| Keepalive: | On 25 Seconds | Sends a regular signal (here every 25 seconds) to keep connections open on NAT routers | |
Advanced Settings | |||
| Create routes to the peer's networks: | Yes | Routes will be created to the networks/hosts entered in step 3 under share peer networks, using the interface shown in step 2 as the gateway | UTMuser@firewall.name.fqdnVPNWireGuard 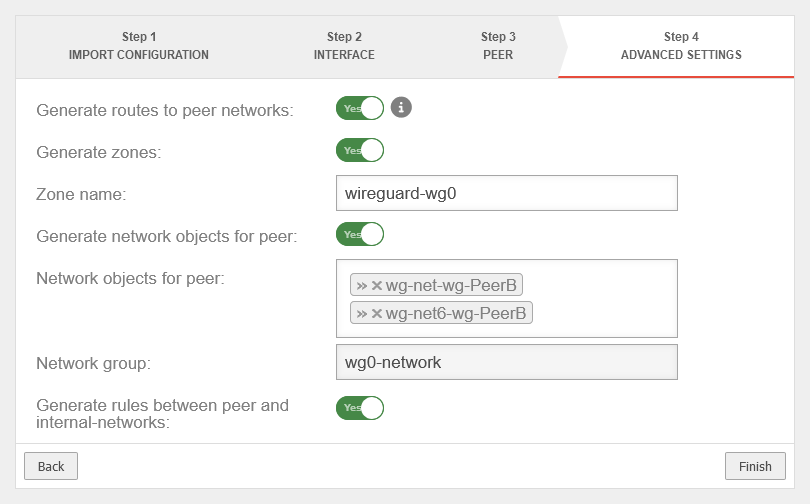 Location A Advanced Settings Location A Advanced Settings
|
| Create zones: | Yes | Creates a new zone for the WireGuard interface | |
| Zone name: | wireguard-wg0 | Name of the zone of the WireGuard connection | |
| Create Network Objects for the Peer: | Yes | Creates network objects (IPv4 and, if applicable, IPv6) for the remote endpoint. The automatic suggestion can also be modified. | |
| Network objects for the peer: | »wg-net-wg-PeerB»wg-net6-wg-PeerB | ||
| Network group: | wg0-network | The networkgroup of the connection is displayed | |
| Create rules between the peer and internal networks: | Yes | Generates auto-created rules to simplify initial setup. | |
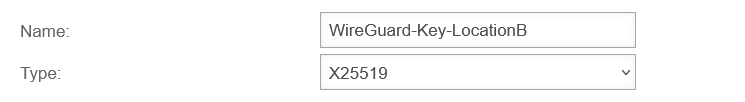
Location B Create WireGuard connections
Import Configuration | |||
|
UTMuser@firewall.name.fqdnVPNWireGuard  Location B If necessary, import configuration Location B If necessary, import configuration
| ||
Interface | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnVPNWireGuard 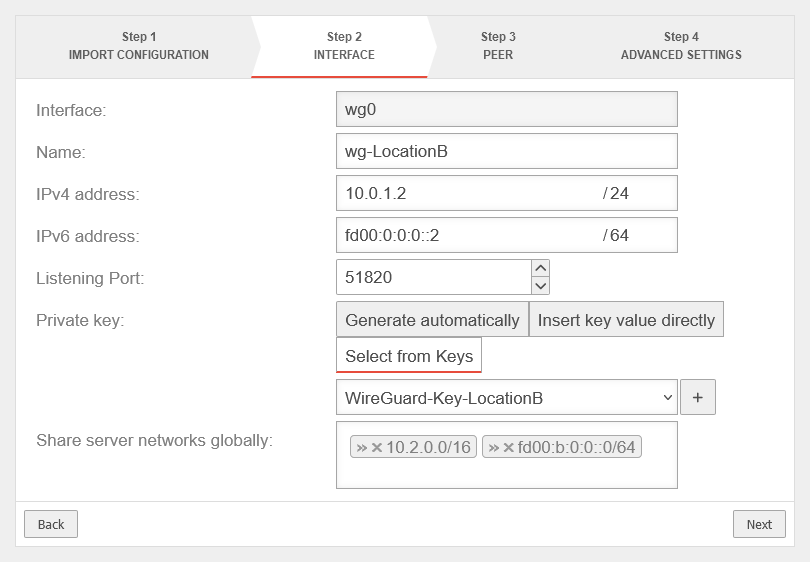 Location B Interface Configuration Location B Interface Configuration
|
|---|---|---|---|
| Name: | wg-LocationB | Connection Name | |
| IPv4 Address: | IPv4 address for the network interface of the transfer network at Location A This determines the Network IP on the transfer network (here: 10.0.1.0/24) | ||
| IPv6 Address: | IPv6 address for the network interface of the transfer network at Location A (optional) This determines the network IP of the transfer network (here: fd00:0:0:0::0/64) | ||
| Listening Port: | 51820 | Default port for WireGuard connections Each additional connection requires a different available port | |
| Private key: | Option: | ||
| Enable global access to server networks: | »10.2.0.0/16»fd00:b:0:0::0/64 | Networks on the (local) server side that WireGuard tunnels of peer can generally access. | |
Peer | |||
| Name: | wg-PeerA | Name of Peer/ Remote Endpoint | UTMuser@firewall.name.fqdnVPNWireGuard 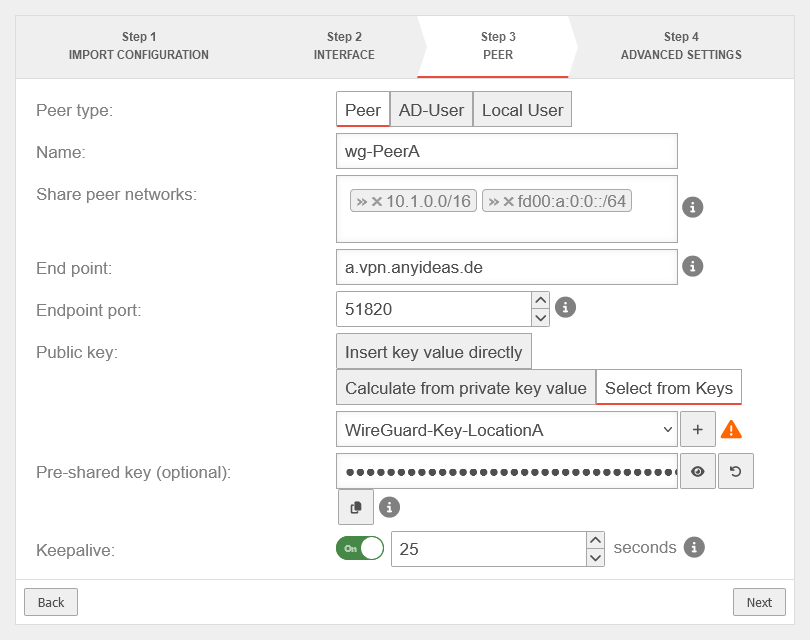 Location B Peer Configuration Location B Peer Configuration
|
| Share peer networks: | »10.1.0.0/16»fd00:a:0:0::/64 | Local network IPs of the remote endpoint that can access the WireGuad tunnel. | |
| Endpoint: | a.vpn.anyideas.de | Public IP or or FQDN of the remote endpoint that can be resolved via public DNS (here: Location A) | |
| Endpoint Port: | 51820 | Listening Port of the Remote Endpoint (here: Location A) | |
| Public key: | Select the public key on the remote connection (here: Location A) | ||
| Pre-Shared Key: | ●●●●●●●●●●●●●●●●● | Pre-Shared Key for additional connection security | |
| Keepalive: | On 25 Seconds | Sends a regular signal (here every 25 seconds) to keep connections open on NAT routers | |
Advanced Settings | |||
| Create routes to the peer's networks: | Yes | Routes will be created to the networks/hosts entered in step 3 under share peer networks, using the interface shown in step 2 as the gateway | UTMuser@firewall.name.fqdnVPNWireGuard 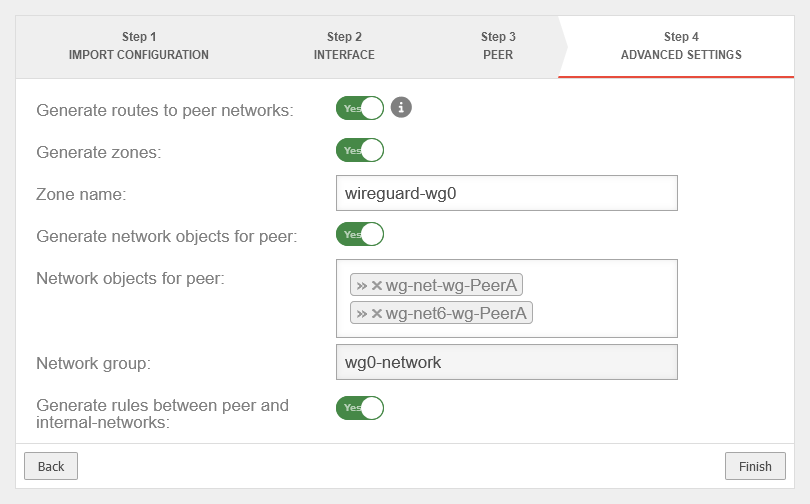 Location B Advanced Settings Location B Advanced Settings
|
| Create zones: | Yes | Creates a new zone for the WireGuard interface | |
| Zone name: | wireguard-wg0 | Name of the zone of the WireGuard connection | |
| Create Network Objects for the Peer: | Yes | Creates network objects (IPv4 and, if applicable, IPv6) for the remote endpoint. The automatic suggestion can also be modified. | |
| Network objects for the peer: | »wg-net-wg-PeerA»wg-net6-wg-PeerA | ||
| Network group: | wg0-network | The networkgroup of the connection is displayed | |
| Create rules between the peer and internal networks: | Yes | Generates auto-created rules to simplify initial setup. | |
| notempty The auto-generated rules allow all services (Any-rules). These rules are intended to simplify the setup of the WireGuard tunnels. For better security, these rules should be customized individually to allow only the services that are actually required. | |||
Set up E2S peer
Add peer on UTM
| Under a peer can be added to the respective connection using the Button | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnVPNWireGuard 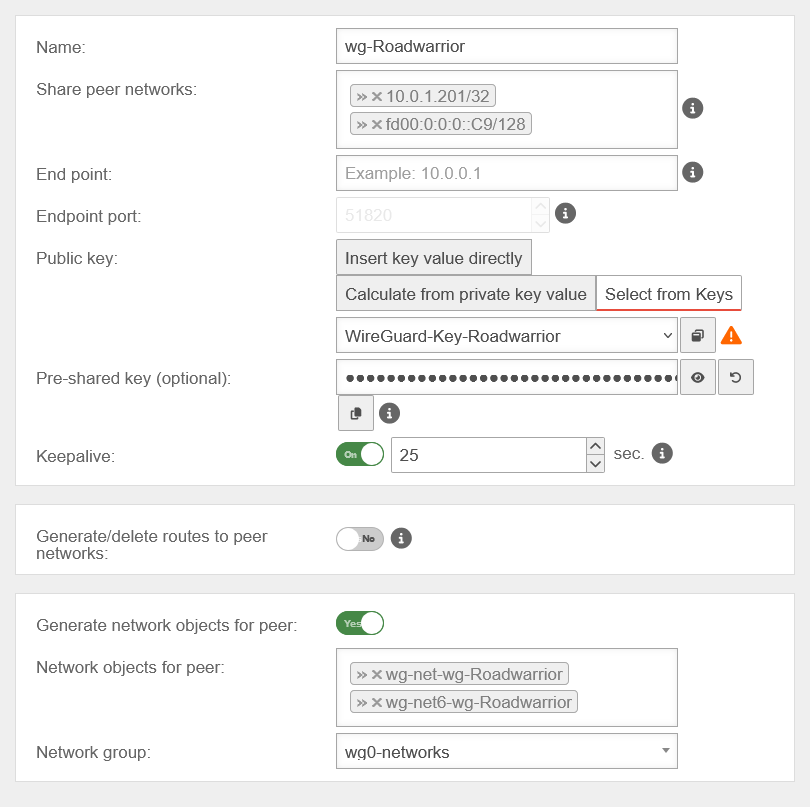
|
|---|---|---|---|
| Name: | wg-Roadwarrior | Peer name | |
| Share peer networks: | »10.0.1.201/32»fd00:0:0:0::C9/128 | IP from the transfer network | |
| Endpoint: | Public IP or DNS-resolvable FQDN of the peer (here, the Roadwarrior). This field can also be left blank if no connection is to be initiated from the UTM | ||
| Endpoint Port: | 51820 | Listening Port of the Peer (here, the Roadwarrior) | |
| Public key: | Select the public key of the peer (here, the Roadwarrior) | ||
| Pre-Shared Key: | ●●●●●●●●●●●●●●●●● | Pre-Shared Key for additional connection security | |
| Keepalive: | On 25 Seconds | Sends a regular signal (here every 25 seconds) to keep connections open on NAT routers | |
| Create/remove route to the peer's network: | No | Creates routes to the networks of the peers when enabled | |
| Create Network Objects for the Peer: | Yes | Creates networkobjects (IPv4 and, if applicable, IPv6) for the peer. The automatic suggestion can also be modified. | |
| Network objects for the peer: | »wg-net-wg-Roadwarrior»wg-net6-wg-Roadwarrior | ||
| Network group: | wg0-networks | The networkgroup of the connection is displayed | |
Creates a WireGuard configuration file WireGuard Client Creates a WireGuard configuration file
Manually create a configuration file In any case the values for PrivateKey, PublicKey, and PresharedKey must be customized. | |||
| [Interface] | |||
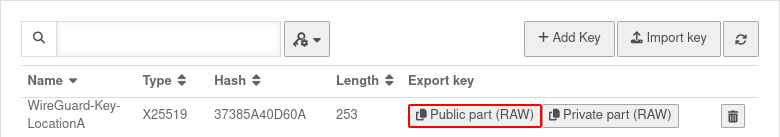
| PrivateKey = | qOPTkQMco1TPd....hsFI= | PrivateKey of the Roadwarrior from the UTM key management. As created at the beginning in the section Key Generation. Found under line WireGuard-Key-Roadwarrior with the button to copy to the clipboard. |
[Interface]
PrivateKey = # PrivateKey of the RW
Address = # Tunnel IP for the Roadwarrior
DNS = # IP of the DNSServer (optional), # Search Domain (optional)
MTU = 1420 # (optional)
ListenPort = 51820 # (optional) |
| Address = | 10.0.1.201/32 | Tunnel IP for the Roadwarrior | |
| DNS = | 10.1.0.33 | Optional: Server that the client should use for name resolution during an active connection. Additionally, a search domain can be entered here, allowing devices to be found by hostname without specifiying the FQDN. Entries are seperated by a comma and a space. If the DNS resolution is to be managed by the UTM, an additional rule will be required! | |
| MTU = | 1420 | :Optional Defines the size of a data packet. Must be between 1300 and 1500. The default value is 1420. | |
| ListenPort = | 51820 | Optional: The port on which the client can be reached. This is assigned dynamically by the client. The same port can be used on both the server and client side (even for multiple clients). | |
[Peer] |
|||
| PublicKey = | beN9ikz… …Do= | ||
| PresharedKey = | 29… …/Wipaxs= | PresharedKey of the WireGuard connection on the UTM located under line (for the example above) wg-Roadwarrior option Pre-Shared Key (optional): Use the Button copy to the clipboardn. | |
| AllowedIPs = | 10.1.0.0/16 | Local network IPs behind the UTM | |
| Endpoint = | a.vpn.anyideas.de:51820 | IP address or hostname of the UTM of the WG instance | |
| persistentkeepalive = | 25 | Keepalive | |
| Save as a file with the extension .conf and import it into a client on the peer (e.g.Securepoint VPN Client) | |||