Logging WireGuard tunnel setup using packet filter rules
New article: 02.2025
This article refers to a Beta version
-
Introduction
Unfortunately, the WireGuard protocol itself does not offer any logging options. However, it is still possible to track which IP addresses have connected or attempted to connect via WireGuard on the UTM. This can be achieved using a packet filter rule. The implicit rules for WireGuard are deactivated and a packet filter rule is created instead, which can then be logged.
In addition, the WireGuard widget can be used to monitor when clients last successfully logged in using the "Last Handshake" column. However, this column is only visible if the widget is at least 2 columns wide.
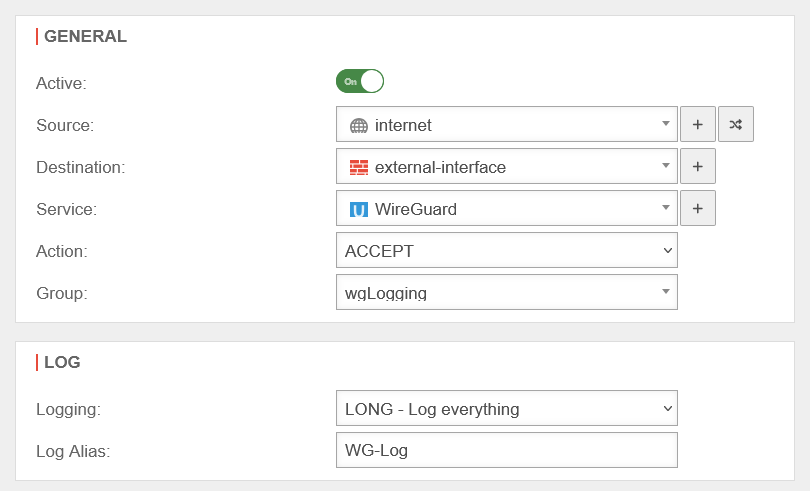
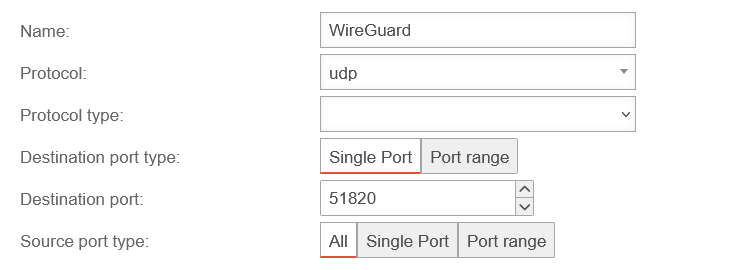
Replace implicit rules with packet filter rules
Disable implicit rules
UTMuser@firewall.name.fqdnVPN  WireGuard Disable implicit rules
WireGuard Disable implicit rules
The rules are disabled when the status indicator is gray ().
Create packet filter rule
Read log
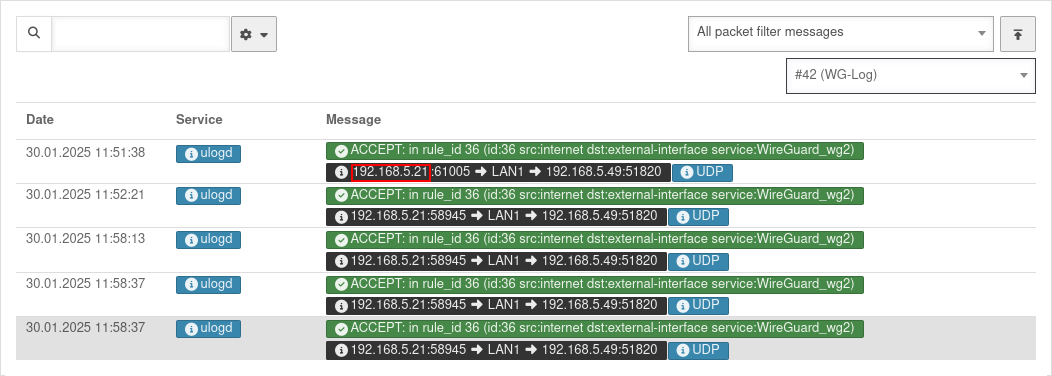
under in the newly created package filter rule