notempty
- Description for multiple VPN servers as targets for one connection
- Description to use multiple VPN profiles
Introduction
A roadwarrior connection links individual hosts to the local network.
This allows, for example, a field worker to connect to the headquarters network.
SSL VPN uses the TLS/SSL standard to encrypt the connection.
Multiple clients can be connected with a SSL VPN Roadwarrior connection on the UTM.
Preparations
These certificates can also be created during setup if necessary.
Transmit DNS/WINS
Allows internal DNS addresses to be resolved via a DNS server that can be reached in the tunnel.
This makes internal servers reachable not only via IP addresses, but also via DNS names.
The setting is made in the menu.
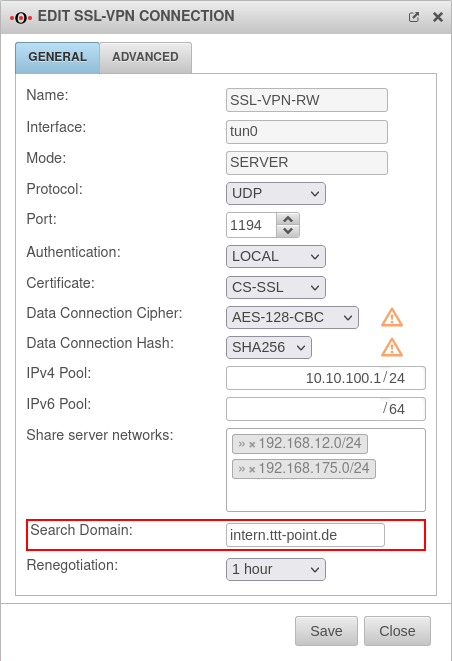
Search Domain
Adds a search domain to internal names: tk-Server1 → tk-Server1.intern.ttt-point.de
This setting can be made in the settings of the VPN connection in the General tab.
Roadwarrior configuration
Setup Wizard
After the login on the firewall's administration interface (by default: https://192.168.175.1:11115), the setup wizard can be called up with Button .
Step 1 |
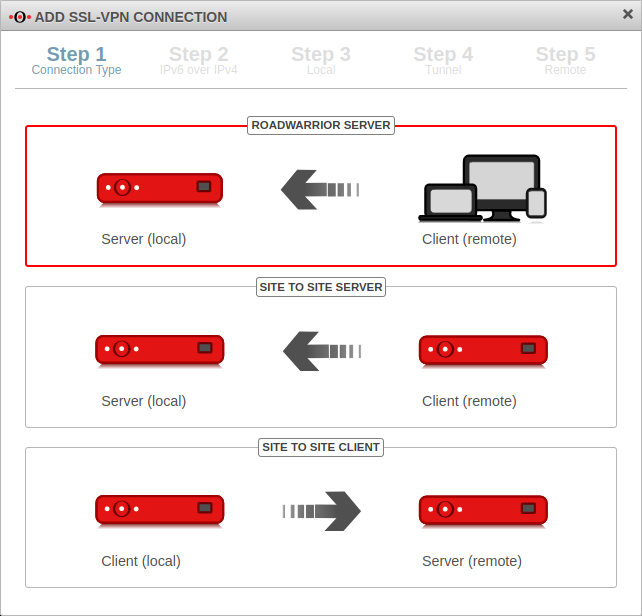 | ||||||||||||||||||
| In installation step 1, the connection type is selected. The following connections are available.
For the configuration of the Roadwarrior Server this one is selected. | |||||||||||||||||||
Step 2 |
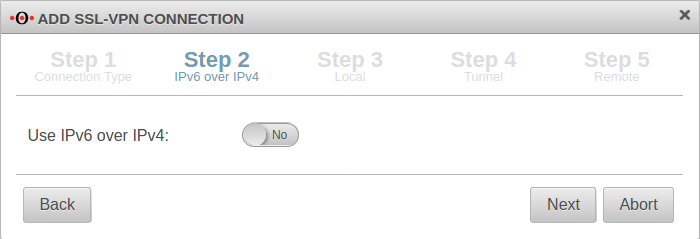 | ||||||||||||||||||
| If IPv6 is to be used in the source and destination network, this must be enabled here. | |||||||||||||||||||
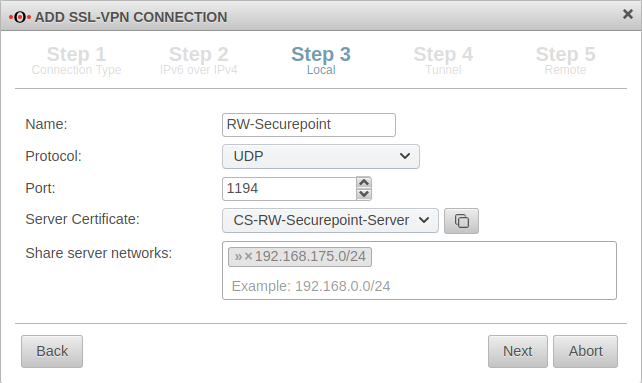
Step 3Local settings for the Roadwarrior server can be made in step 3. | |||||||||||||||||||
|
 | ||||||||||||||||||
Step 4 |
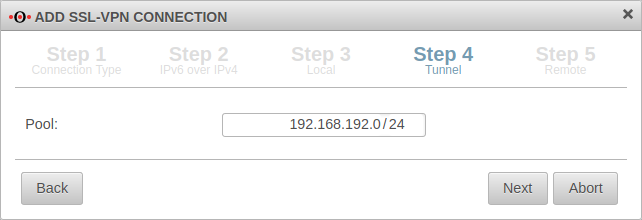 | ||||||||||||||||||
| In installation step 4, the transfer network for the Roadwarrior is entered. The transfer network can be freely selected, but must be otherwise unused on the UTM. | |||||||||||||||||||
Step 5 |
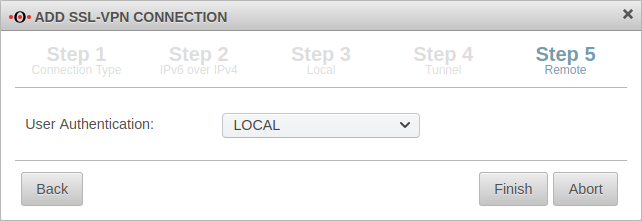 | ||||||||||||||||||
| The user authentication is selected in the last step. After that, the setup wizard can be completed.
| |||||||||||||||||||
Completion |
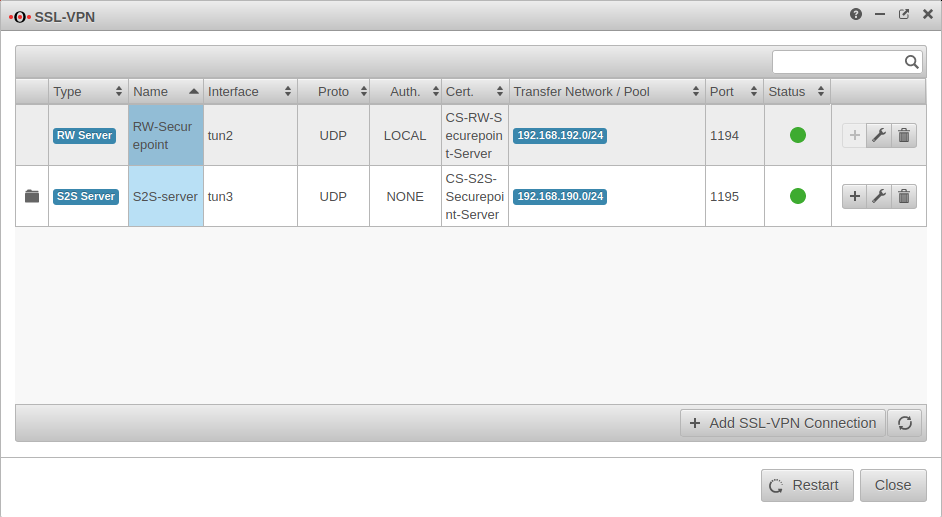 | ||||||||||||||||||
In the SSL VPN overview all configured connections are displayed. In order for the connection to become active, the SSL VPN service must be restarted: | |||||||||||||||||||
Policy
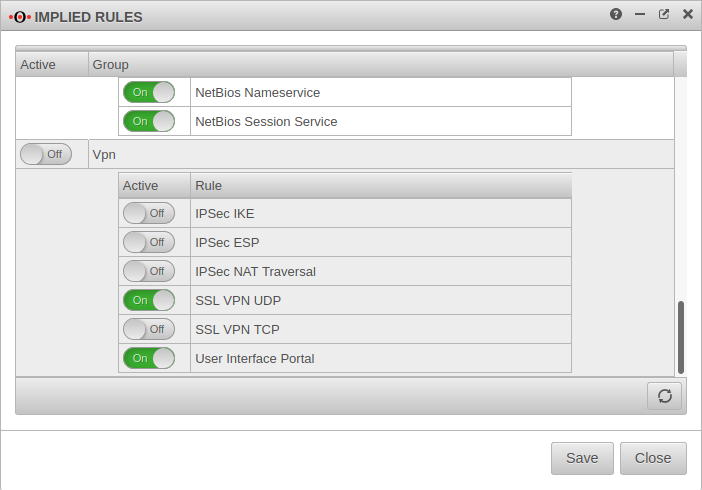
Implied rules
Under Section VPN the protocol used for the connection can be enabled.
In the example On SSL VPN UDP
This Implicit rule frees the ports used for SSL VPN connections on the WAN interface.
If the user is to download the client from the user interface, this must be additionally enabled here:
{#var:ein
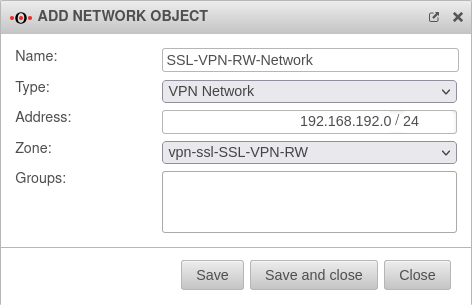
Network objects
A TUN interface was created when the connection was set up. It automatically receives the first IP from the transfer network configured in the connection and a zone "vpn-ssl-<servername>".
The Roadwarrior clients will receive an IP from this network and will be located in this zone.
To grant the roadwarriors access to your own network, a network object must be created.
| Caption | Value | Description |
|---|---|---|
| Name: | SSL-VPN-RW-Network | Distinctive label, freely selectable |
| Type | ||
| Adress: | 192.168.192.0/24 | The network IP that was specified as the tunnel pool in step 4. |
| Zone | the zone over which the tunnel network is addressed. | |
| Groups: | The user must be assigned the previously created group. |
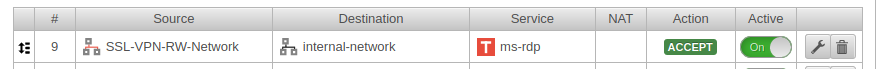
Port filter rule
Menu Tab Port Filter Button
A rule allows RW clients to access the local network:
| Caption | Value | Description |
|---|---|---|
| Source | SSL-VPN-RW-Network | Inbound rule |
| Ziel | internal-network | |
| Service | required service |
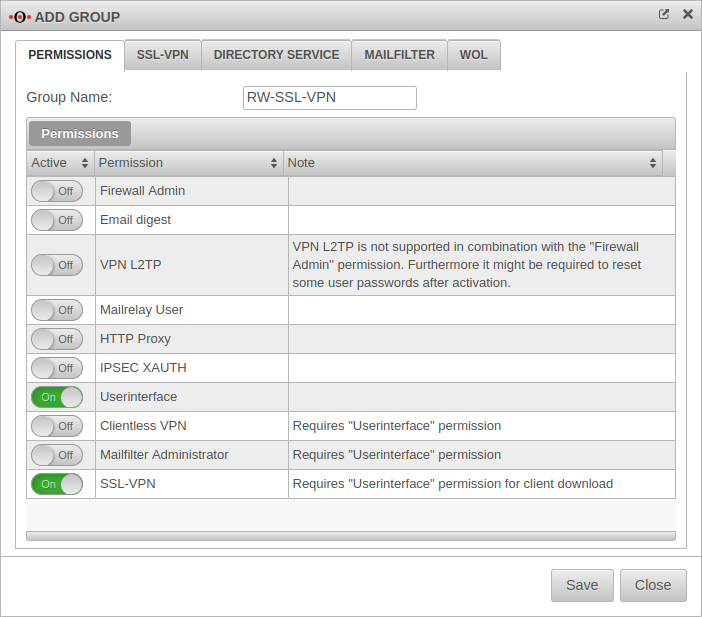
Creating users and groups
Group
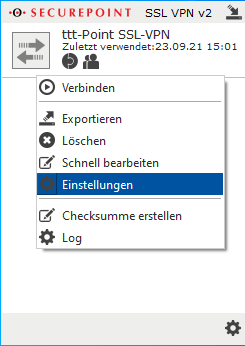
Under , you must first create a for the users that will access the Roadwarrior server.
Settings in the Permissions tab.
Group Name: RW-SSL-VPN
The following authorisations must be given:
- On SSL-VPN
- On Userinterface
| Settings in SSL VPN tab | ||
|---|---|---|
| Client downloadable in the user interface: | On | Per default over the port 443, so e.g. under https://192.168.75.1 accessible |
| SSL VPN connection: | RW-Securepoint | Select just created connection |
| Client certificate: | Client certificate: | Selection of the client certificate described in Step 3 of the setup wizard.
|
| Remote Gateway: | 192.0.2.192 | The remote gateway is the address of the external interface. This address must be accessible external. |
| Redirect Gateway: | Off | When activated, requests from roadwarrior clients to the Internet or networks outside the VPN are also redirected via the local gateway. As a result, these connections also benefit from the protection of the UTM |
| Available in the port filter: | On | Enables Identity-Based Firewall (IBF) for SSL VPN |
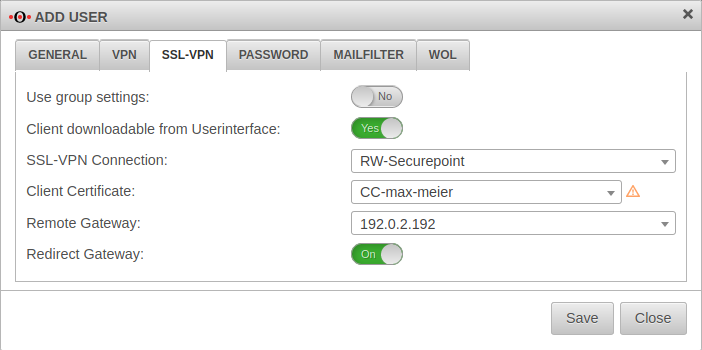
User
Tab Add User Button or Edit User .
GeneralTab General | ||
| Groups: | ×RW-SSL-VPN | The user must be assigned the previously created group. |
SSL-VPNTab SSL-VPN | ||
| Use settings from the group | On | If settings have already been made for the group, these can be adopted here instead of individual values. |
| If the information has been saved, the corresponding files can already be downloaded by the administrator at this point. | ||
Further information on users can be found in the article on User Management.
The SSL VPN Client
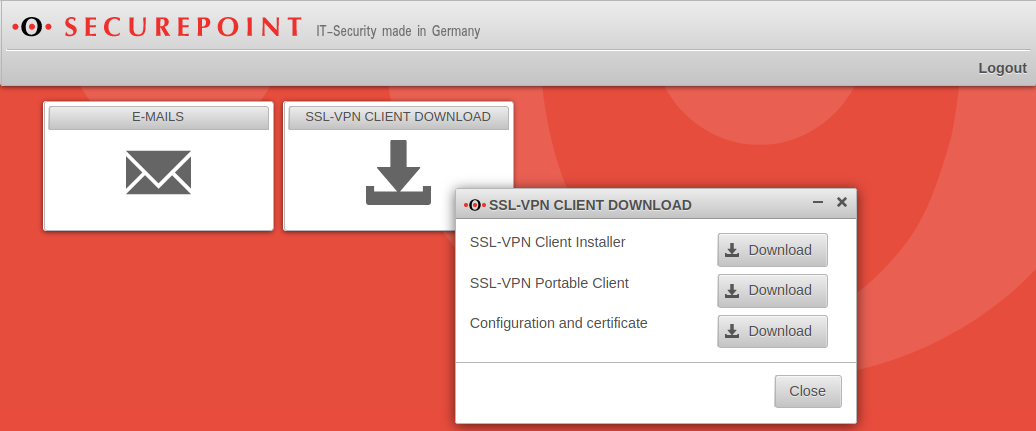
Downloading the SSL VPN client in the user interface
For users who wish to connect to the UTM via SSL VPN, the appliance provides a pre-configured SSL VPN client:
.
- This client contains the configuration files and all required certificates.
- Logon to the user interface of the UTM by default via port 443, e.g. at https://192.168.75.1.
- The user interface is reached via the internal interface of the Securepoint appliance.
The client is offered as:
SSL VPN Client Installer
- The installation must be performed with administrator rights. Required processor architecture: x86 / x64
- SSL VPN Portable Client
The portable version can be copied to a USB stick, for example, and can thus be run on other computers.
This requires administration rights, as a virtual TAP device must be installed and routes set. Required processor architecture: x86 / x64
- Configuration and certificate
For use in other SSL VPN clients
- In addition to the SSL VPN client, the compressed folders contain
- a configuration file
- the CA and client certificates
- and a driver for the virtual TAP network interface.
To install the virtual TAP interface, the user needs administrator rights on the machine being used.
As of Windows 10, older SSL VPN clients < V2 can no longer be used.
Installation: Hints for the installation can be found on our wiki page for the VPN client.
Establish SSL VPN connection as client
Double-click on the lock icon in the taskbar to open the SSL VPN client.
Start the connection by clicking ![]()
Multiple VPN servers as targets for one connection
In the settings of a connection under Advanced/Remote additional VPN servers with IP or hostname can be stored as destination.
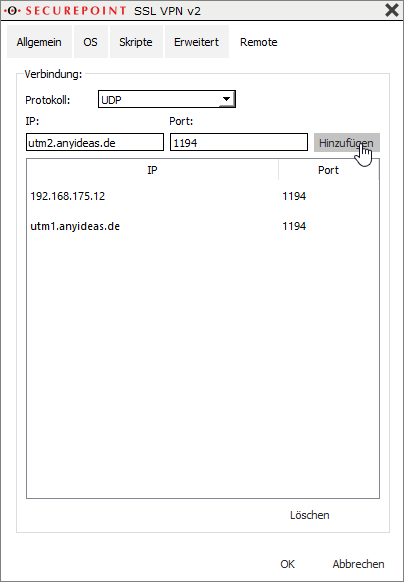
- IP: utm1.anyideas.de
- Port: 1194
Apply details with Add
Close window with OK.
Use multiple VPN profiles
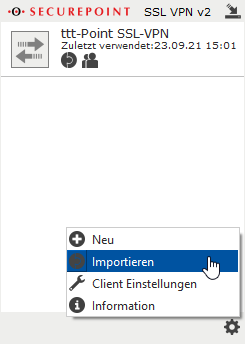
Multiple VPN profiles can be imported and used at the same time.
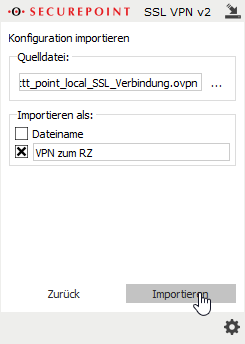
- By clicking ... in the source file:section, a file in .ovpn format can be selected.
- In the Import as:section, either the filename or any custom identifier can be selected, which will then be displayed in the client window for that connection.
- Finish with the button.
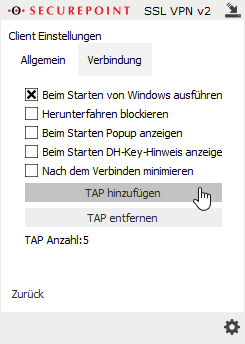
- If several VPN profiles are to be used simultaneously, additional TAP drivers must be added:
- Left click on the cogwheel symbol
- Menu {spc
- By clicking ... in the source file:section, a file in .ovpn format can be selected.
- In the Import as:section, either the filename or any custom identifier can be selected, which will then be displayed in the client window for that connection.
- Finish with the button.
Notes
Encryption
By default, an AES128-CBC method is used. The encryption method can be customized in the server or/and client profile.
The parameters must be identical on the server and client side. Otherwise data transfer is not possible
Hash method
By default, a SHA256 hash method is used. The hash method can be customized in the server or/and client profile.
The parameters must be identical on the server and client side. Otherwise data transfer is not possible
QoS
For the VPN connection, the TOS fields for automatic QoS can be set in the packets. This setting can be enabled in the VPN connection settings under "Advanced".
Note on upstream routers/modems
There are always problems with the stability of the connection if a router/modem in front of the appliance also has an active firewall. Please do not use any firewall functionality on these devices.
It must be ensured that the required ports are forwarded.
IPv6 for incoming connections
In the settings of the roadwarrior server , the protocol or for IPv6 can be activated under General / Protocol.
Troubleshooting
For advice on troubleshooting SSL VPN, see the Troubleshooting Guide SSL-VPN (pdf document).