Last adaptation to the version: 14.1.1 (11.2025)
- BetaFor participants on the Beta Channel only:
- New notification for eMMC Hard Disk Status
- Note added if the Alerting Center is not enabled in the license v14.1.0
- New section: Read out the messages via SNMP
Introduction
The Alerting Center automatically sends emails with log events. This sets up monitoring of log events and simplifies monitoring. Error messages can be forwarded to the admin before a malfunction occurs or a malfunction can be detected more quickly.
The Alerting Center is always active by default as soon as a valid email address has been entered and the mail relay has been configured correctly.
It sends notifications by email to the global email address.
There are
- Immediate reports that are sent immediately when an event occurs, and
- Regular reports that are sent in a fixed period of time.
notempty
Requirements
For the Alerting Center to be able to send messages, the Mailrelay must be configured.
If no own mail server or no fixed public IP address is available, a Smarthost can be configured in the menu .
Configuration
Menu Item
General
| Caption | Default | Description | UTMuser@firewall.name.fqdn 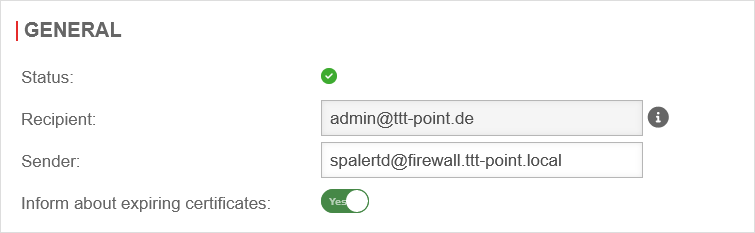 Alerting Center - General Alerting Center - General
| |||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Status: | ||||||||||||||||||||||||||||||||||||
| Recipient: | admin@ttt-point.de | Here must be a valid mail address. This is displayed in the menu Area Appliance settings Firewall →global email address.
| ||||||||||||||||||||||||||||||||||
| Sender: | spalertd@firewall.ttt-point.local | The sender address can be freely configured. The default is spalertd@firewallname | ||||||||||||||||||||||||||||||||||
| Inform about expiring certificates: | Yes | Should remain activated so that certificates can be extended in good time. | ||||||||||||||||||||||||||||||||||
Immediate email report | ||||||||||||||||||||||||||||||||||||
| Enabled: | Yes | Immediate e-mail reports are sent by default | 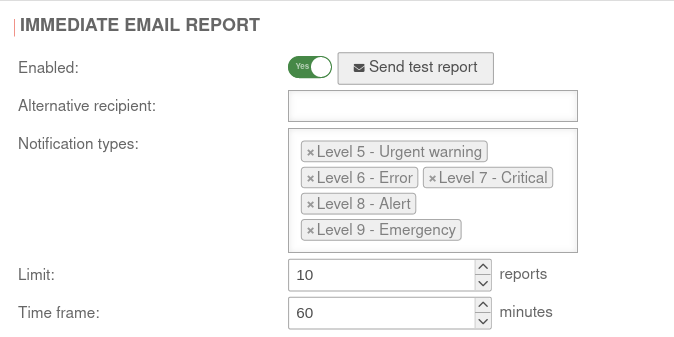 | |||||||||||||||||||||||||||||||||
notempty New as of v12.6.0 |
Sends a test report to the stored address or to the alternative recipient | |||||||||||||||||||||||||||||||||||
| Alternative recipient: | Here, an alternative recipient can be entered | |||||||||||||||||||||||||||||||||||
| Notification types | Level 5 - Urgent warning Level 6 - Error Level 7 - Critical Level 8 - Alert Level 9 - Emergency |
There are two different groups of notifications: | ||||||||||||||||||||||||||||||||||
| Limit: | 10 Reports | Immediate reports for the same error within a time frame | ||||||||||||||||||||||||||||||||||
| Time frame: | 60 Minutes | Period after which reports are sent again until the maximum number is reached. | ||||||||||||||||||||||||||||||||||
Regular email report | ||||||||||||||||||||||||||||||||||||
| Enabled: | Yes | Regular email reports are sent by default. This only happens if any event with a log level has occurred. Otherwise, no report will be sent. If a report is desired nevertheless, this can be realized via the Unified Security Report.
|
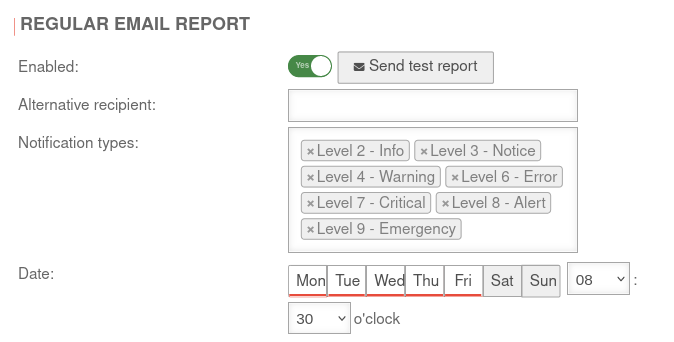 | |||||||||||||||||||||||||||||||||
notempty New as of v12.6.2 |
Sends a test report to the stored address or to the alternative recipient | |||||||||||||||||||||||||||||||||||
| Alternative recipient: | Here, an alternative recipient can be entered | |||||||||||||||||||||||||||||||||||
| Notification types | Level 2 - Info Level 3 - Notice Level 4 - Warning Level 5 - Urgent warning Level 6 - Error Level 7 - Critical Level 8 - Alert Level 9 - Emergency |
In the click box further priority groups can be selected or deselected. Events configured with these syslog groups are listed in a regularly sent mail. | ||||||||||||||||||||||||||||||||||
| Date: | Mon Tue Wed Thu Fri : |
Click on the days of the week to select or deselect them. | ||||||||||||||||||||||||||||||||||
HTTP RequestHTTP Request
| ||||||||||||||||||||||||||||||||||||
| Enabled: | No | By default disabled. If enabled, HTTP requests can be sent. Thereby, the alerting centre transmits an HTTP request to a defined address with defined content. |
 | |||||||||||||||||||||||||||||||||
| Notification types | The notification types can be selected in the click box. | |||||||||||||||||||||||||||||||||||
| Content: | This is where the content is determined, and the structure should look like this:
<init> URL=xxx METHOD=xxx CONTENT_TYPE=xxx <body> My message. </body> </init> | |||||||||||||||||||||||||||||||||||
Showcase with a paid service that can in turn forward the messages to a mobile phone app.
| ||||||||||||||||||||||||||||||||||||
Notifications
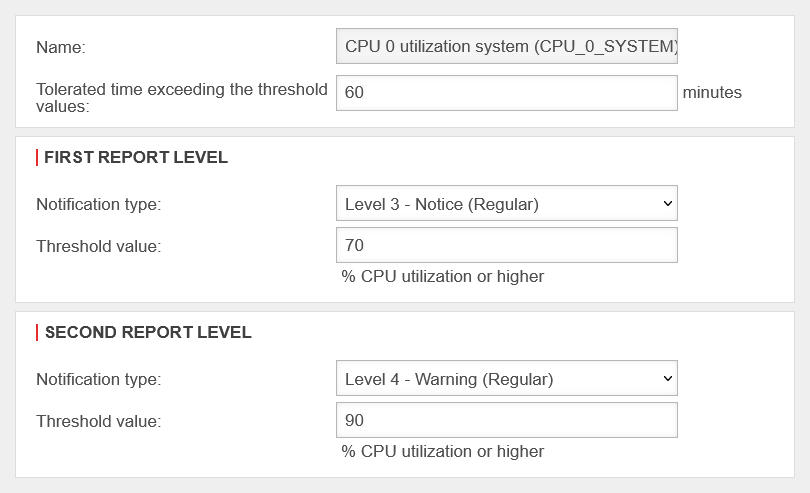
| Name: | Toleranced exceedance of threshold values: Default |
Threshold Value: 1 Default Notification type: Severity-Level |
Threshold Value: 2 Default Notification type: Severity-Level |
|---|---|---|---|
|
60 Minutes | 70 % CPU utilization or higher Level 3 - Notice |
90% Level 4 - Warning |
|
60 Minutes | 70 % CPU utilization or higher Level 3 - Notice |
90% Level 4 - Warning |
|
... | ... | ... |
|
240 Minutes | Hard disk temperature rises to 60°C or higher Level 4 - Warning |
70°C Level 6 - Error |
|
60 Minutes | 1.5 load average (5 minutes) or higher. Average value of the last 5 minutes. |
4 Level 5 - Urgent warning |
|
240 Minutes | 100 e-mails or more could not be processed yet and are in the mail queue Level 4 - Warning |
1000 E-Mails Level 6 - Error |
|
0 Minutes | 20000 bytes / second or more Level 0 - No message |
200000 Bytes Level 0 - No message |
|
... | ... | ... |
|
0 Minutes | 20 % free disk space or less Level 4 - Warning |
10% Level 5 - Urgent warning |
Event-based notifications
| For event-based notifications, a is directly assigned to the Notification Type. | UTMuser@firewall.name.fqdnAlerting Center  Evident-based notification example Evident-based notification example
| ||
| Name: | Message: | Default Syslog Group: | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ACME Errors | Error messages for ACME certificates | Level 6 - Error | |||||||||||||||
| ACME Information | ACME certificate messages | Level 3 - Notice | |||||||||||||||
| AD/LDAP | Connection problems to Active Directory or LDAP server. | Level 4 - Warning | |||||||||||||||
| Bond Failure notempty New as of v14.0 |
A malfunction has been detected. | Level 8 - Alert | |||||||||||||||
| Bond Information notempty New as of v14.0 |
Bond events were detected. | Level 2 - Info | |||||||||||||||
| Cloud-Backup | Regular cloud backup failed. | Level 6 - Error | |||||||||||||||
| Cluster Switch | Cluster: Switching between MASTER and BACKUP. | Level 8 - Alert | |||||||||||||||
| Connection Tracking | The maximum number of Conntrack entries has been reached | Level 7 - Critical | |||||||||||||||
| DBUS Rule Policy | DBUS security violation detected. | Level 7 - Critical | |||||||||||||||
| Driver Error notempty New as of v14.0 |
A driver malfunction has been detected. | Level 6 - Error | |||||||||||||||
| DSL/VDSL | Dial-up problem over DSL or VDSL. | Level 4 - Warning | |||||||||||||||
| DynDNS-Client Account | Account error message of the DynDNS client. | Level 4 - Warning | |||||||||||||||
| DynDNS-Client Host | Host error message of the DynDNS client. | Level 4 - Warning | |||||||||||||||
| DynDNS-Client Server | Server error message of the DynDNS client. | Level 4 - Warning | |||||||||||||||
| eMMC Harddisk | There is a warning about the hard disk status. The message contains detailed information about the specific problem. Possible error messages:
limit values:
The thresholds and test parameters, including the path to a program that is executed when thresholds are exceeded, can be adjusted under /etc/spemmcd/spemmcd.conf. |
Level 8 - Alert | |||||||||||||||
| Fallback-Interface | Fallback interface activated/deactivated. | Level 7 - Critical | |||||||||||||||
| Firmware Updates | Firmware update messages | Level 2 - Info | |||||||||||||||
| Firmware Update Error | Firmware update error messages | Level 6 - Error | |||||||||||||||
| GeoIP Objects | Notifications from the GeoIP service | Level 4 - Warning | |||||||||||||||
| GeoIP Update | GeoIP databases were updated. | Level 2 - Info | |||||||||||||||
| GeoIP Update Error | Error updating the GeoIP databases. Databases were reset to their previous state. | Level 4 - Warning | |||||||||||||||
| HTTP-Proxy Workers | HTTP-Proxy: No more worker processes. For load balancing, the HTTP proxy squid outsources its services to worker processes. When all worker processes are terminated, the HTTP proxy no longer runs. |
Level 6 - Error | |||||||||||||||
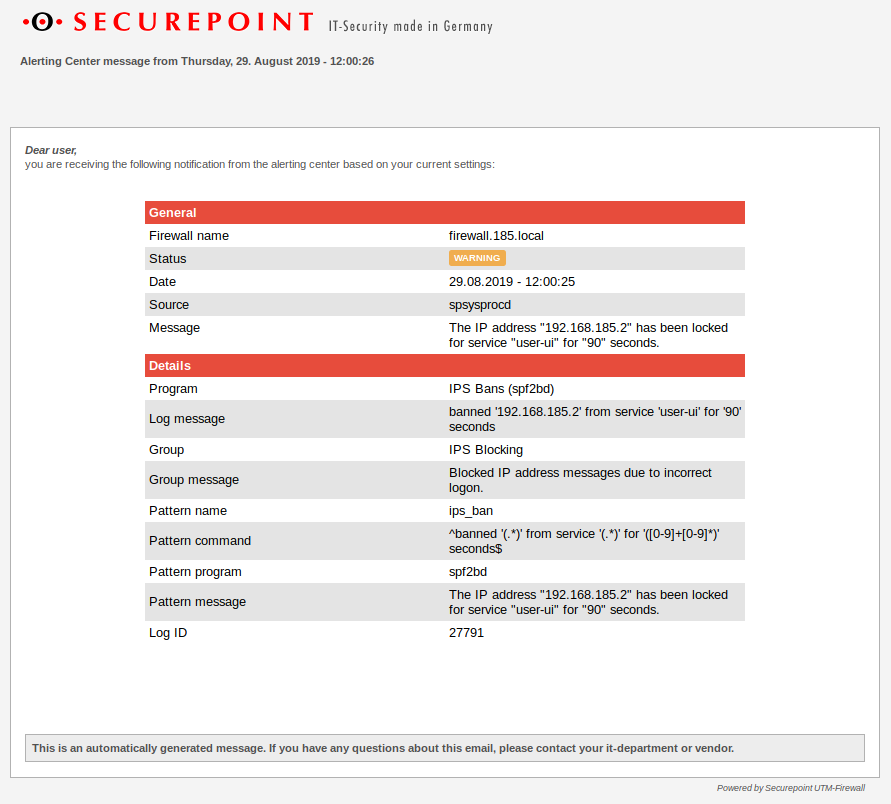
| IPS Blocking | Blocked IP address messages due to incorrect logon | Level 4 - Warning | |||||||||||||||
| License Error | License error messages | Level 6 - Error | |||||||||||||||
| License Information | License information messages. | Level 3 - Notice | |||||||||||||||
| Mail Scanner | Mail scanner has detected a virus | Level 6 - Error | |||||||||||||||
| Mailconnector Authentication | Mailconnector authentication problem to the e-mail provider | Level 6 - Error | |||||||||||||||
| Mailconnector Fetch | Mailconnector rejects an e-mail due to message size | Level 4 - Warning | |||||||||||||||
| Mailrelay Greylist Pass-All Mode | Failed to reset greylisting database, greylisting module will be bypassed (deactivated). | Level 7 - Critical | |||||||||||||||
| Mailrelay Greylist Reset | Failed to load greylisting database, greylisting database will be reset. | Level 4 - Warning | |||||||||||||||
| Mandatory Access Control (MAC) | Security breach detected (MAC) | Level 7 - Critical | |||||||||||||||
| Network Interface Changes | Change of a network interface detected. | Level 4 - Warning | |||||||||||||||
| Shutdown Detection | Unclean shutdown detected | Level 7 - Critical | |||||||||||||||
| Spam Filter Cloud | Spam Filter can not connect to cloud | Level 4 - Warning | |||||||||||||||
| Squid Virus Scanner | Squid (HTTP proxy) has detected a virus | Level 6 - Error | |||||||||||||||
| SSL VPN | Authentication failed with SSL VPN Cert&Auth | Level 4 - Warning | |||||||||||||||
| Threat Intelligence Filter - FORWARD | Forwarding to an IP address prevented by Threat Intelligence Filter | Level 8 - Alert | |||||||||||||||
| Threat Intelligence Filter - OUTPUT | Calling an IP address prevented by Threat Intelligence Filter | Level 8 - Alert | |||||||||||||||
| Threat Intelligence Filter - INPUT | External access from an IP address prevented by Threat Intelligence Filter | Level 8 - Alert | |||||||||||||||
| USC PIN Block | An incorrect USC PIN was entered multiple times for authentication on the UTM. Authentication via a PIN is thus blocked. Unlock the PIN in the UTM by authenticating yourself at the UTM with username and password (and OTP if necessary). | Level 7 - Critical | |||||||||||||||
| USC PIN Mismatch | The verification of the USC PIN for authentication at the UTM failed. | Level 6 - Error |
The settings are concluded with .
Result
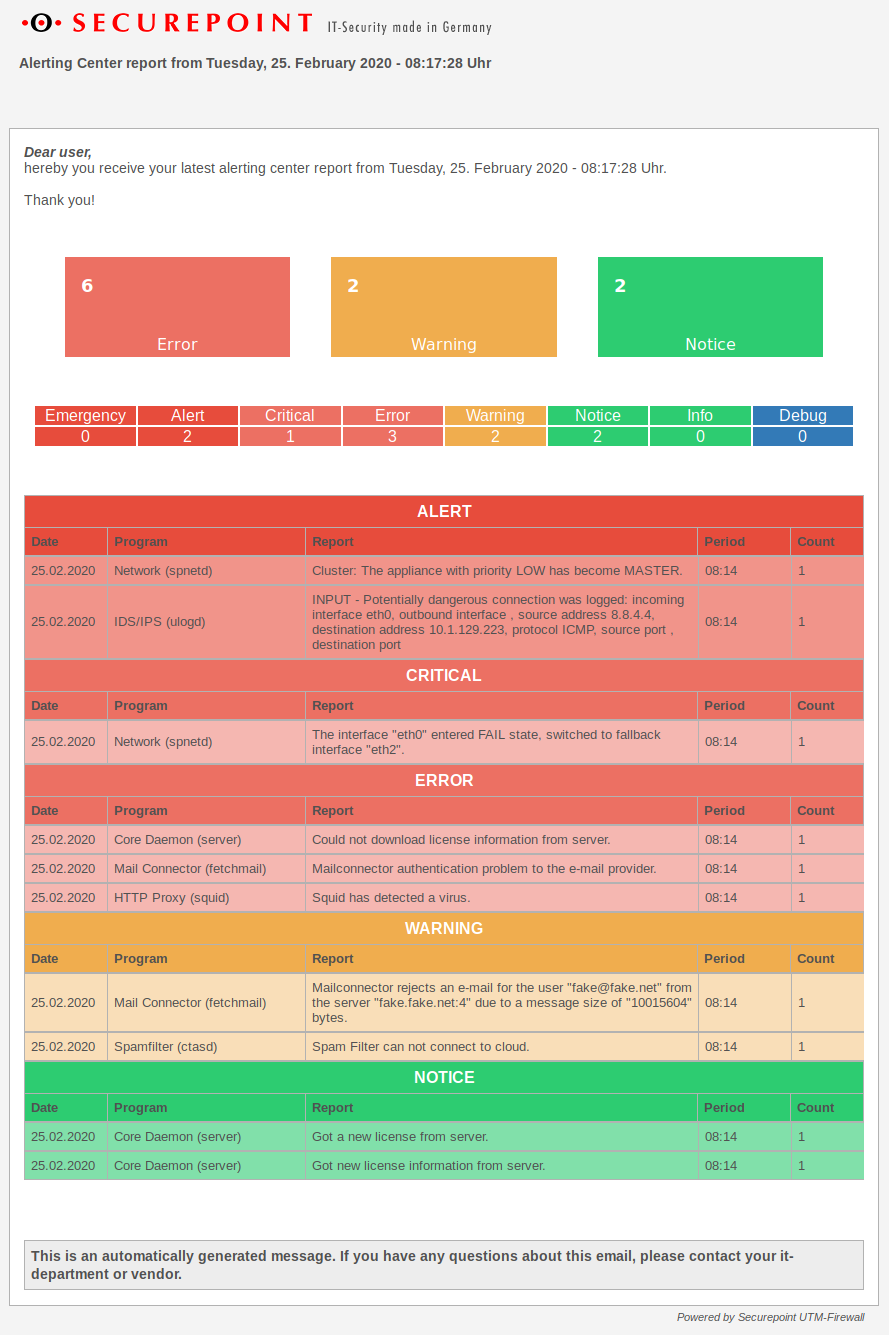
Notifications are now sent to the specified mail address at the configured times and system states.
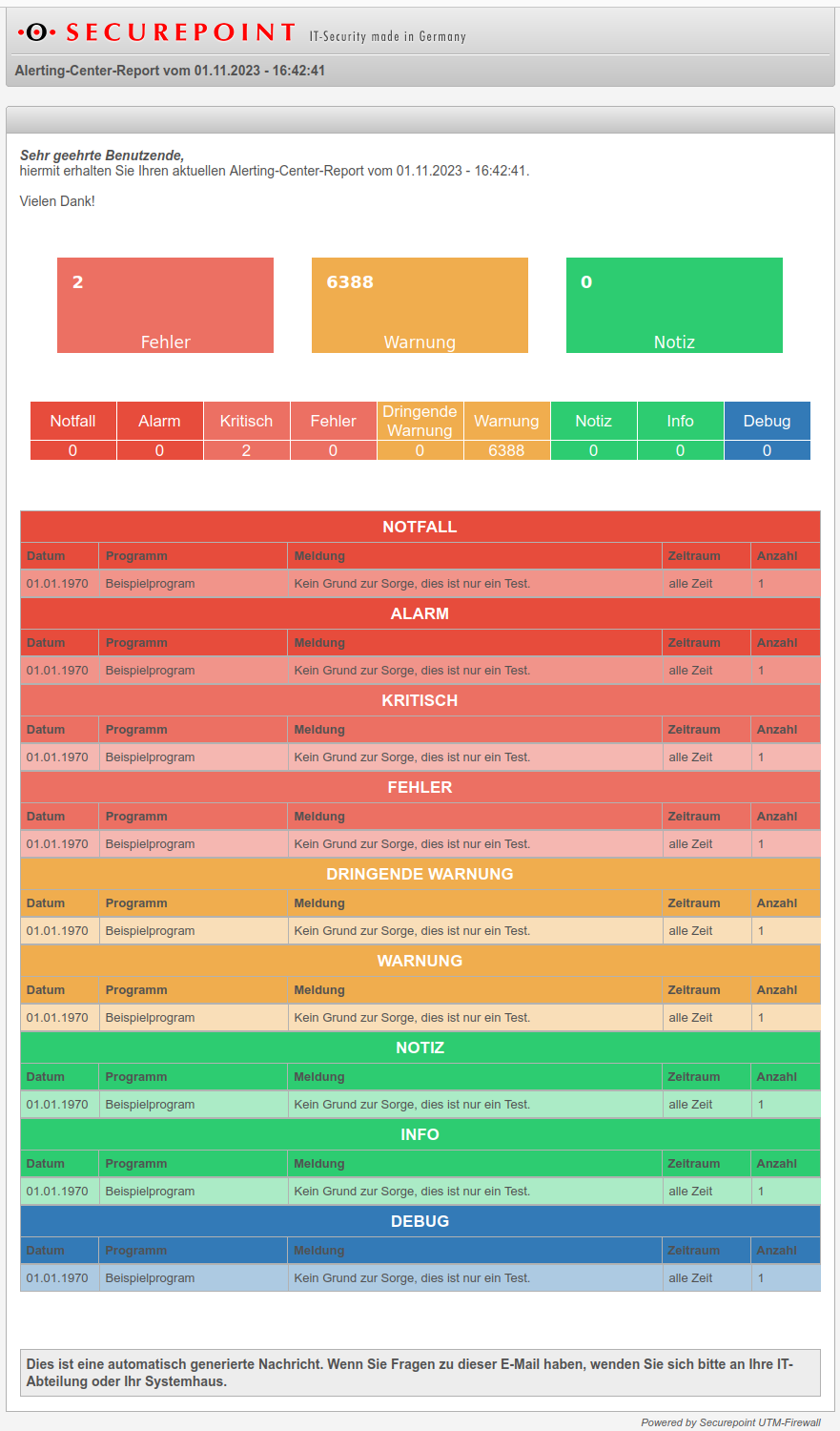
The subject of the messages is structured as follows: Subject:Alerting-Center (firewall-name): Report type. Where this means:
- Report → Regular report
- Error / Critical / Alert / Emergency → Syslog severity level of an immediate report
In the report the messages are first sorted by syslog level and then by date/time
Functionality test
The alerting center can send test reports to test the correct notification. The following CLI commands are used for this purpose:
alertingcenter report test
alertingcenter fast report test
alertingcenter http request test
The email itself, however, contains clear indications that it is a test.
Read out the messages via SNMP
The alerting centre messages can also be read out via SNMP.
Excerpt from the MIB:
More information are available in the article about SNMP-Oids