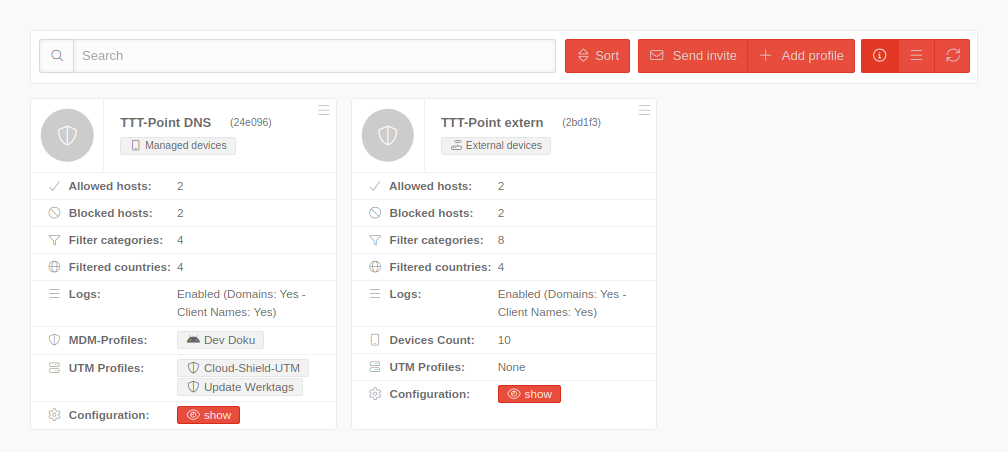
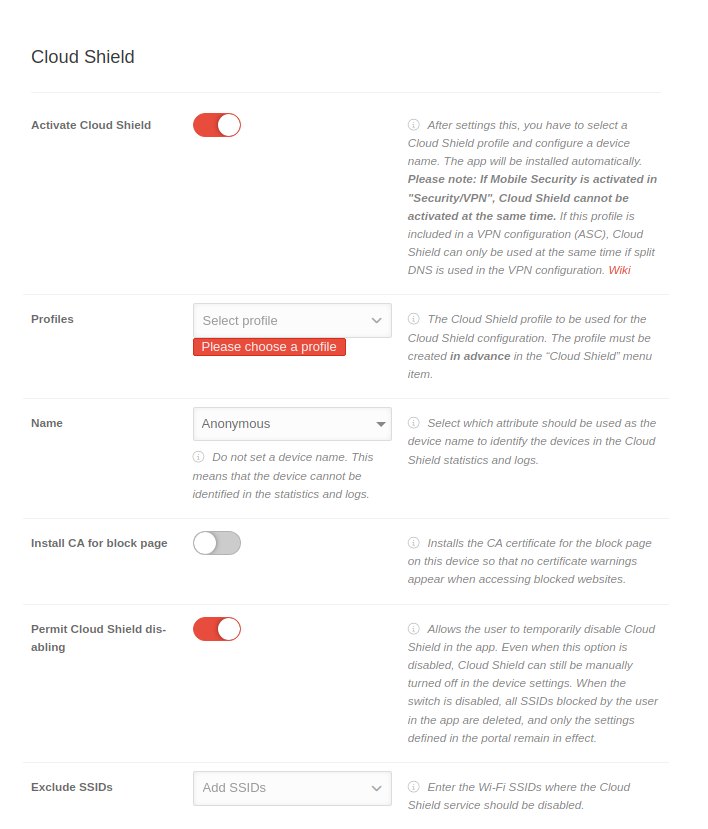
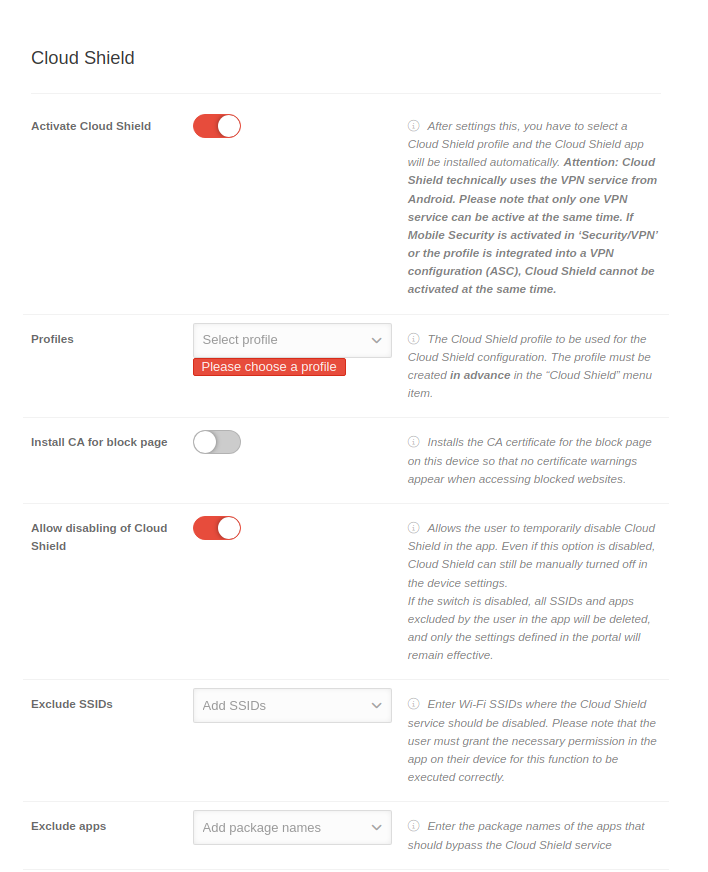
| Using the Create profile button a new profile can be crated. The same configuration options are available during both, creation and editing.
|
| Caption |
Value |
Description
|
|
|
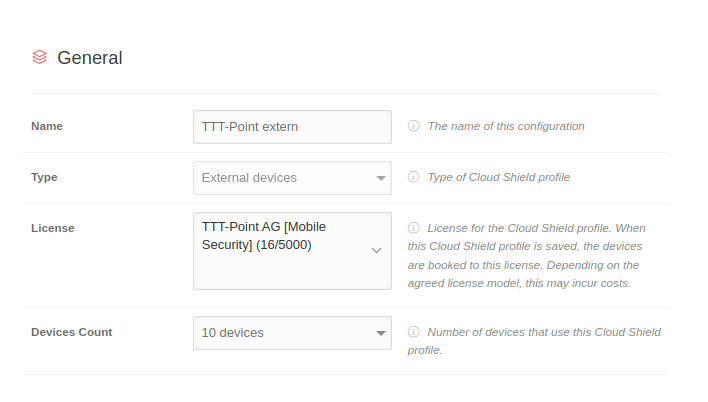
| Name |
TTT-Point extern |
The name of the configuration
|
 Create profiles General tab
|
| Type |
Managed Devices |
Type of the Cloud Shield profile
|
| External devices
|
license
Only for: External devices |
TTT-Point AG [Mobile Security] (16/5000) |
License for the Cloud Shield Profile. When this Cloud Shield Profile is saved, the devices are assigned to this license. Depending on the agreed license model, this may incur costs.
|
Number of devices
Only for: External devices |
10 devices |
Number of devices using this Cloud Shield Profile
|
|
|
|
|
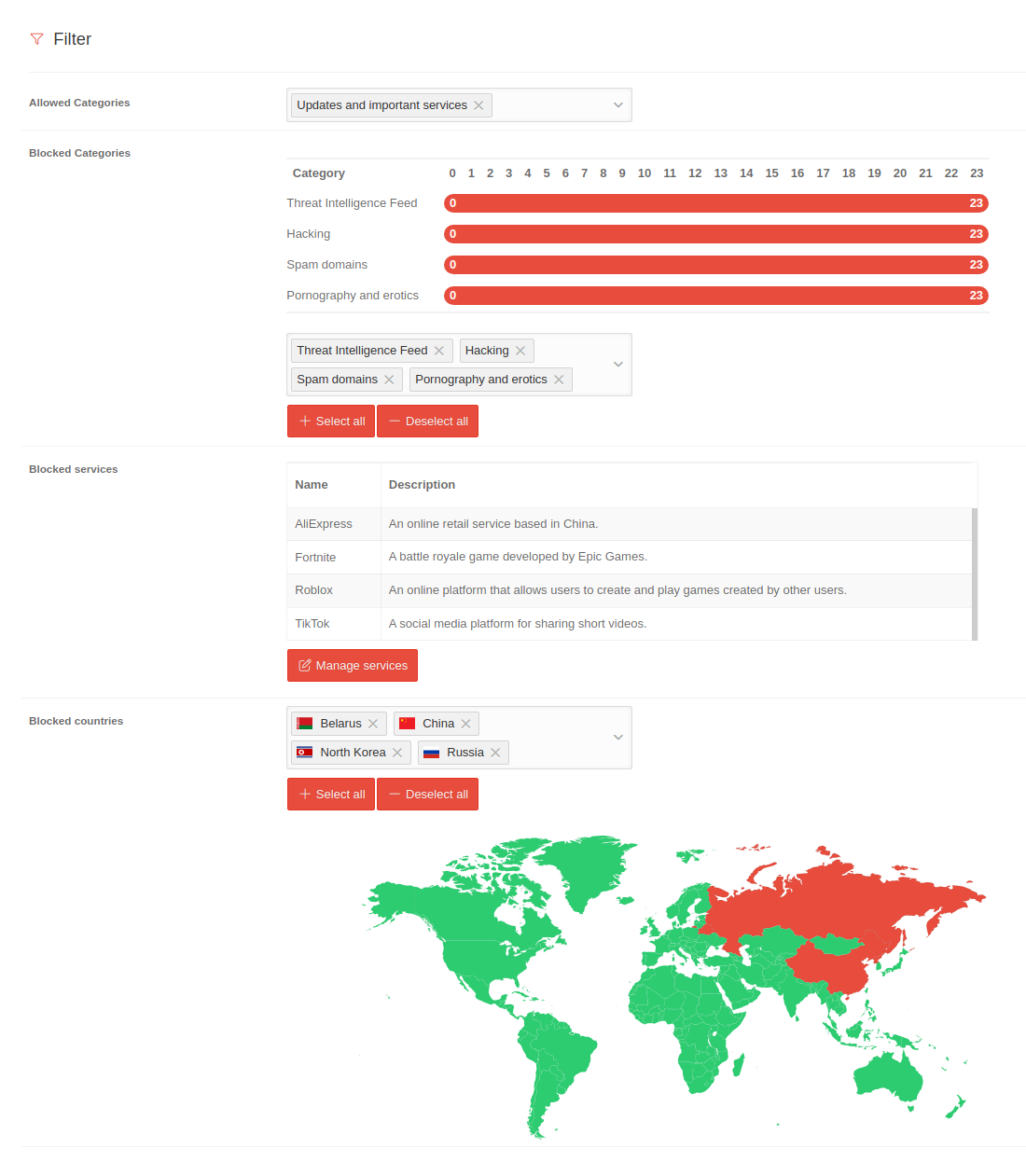
| Allowed categories |
Updates and important services |
Selection of permitted categories
|
 Create profiles General filter
|
| Blocked categories |
Threat Intelligence Feed Hacking Spam domains |
Selection of categories to be blocked. For the selected categories, you can also define which scores (0-23) should trigger blocking.
Additionally, all available categories can be selected or deselected at once using the corresponding buttons.
|
| Select all Deselect all
|
| Blocked services notemptyNew as of: 2.10 |
| Name |
Description
|
| Name of the blocked service |
Description of the blocked service
|
|
This service list maintained by Securepoint - Manage services opens a dialog box displaying the service list
- Block blocks the desired service
- Allow re-enables a blocked service
|
| Manage services
|
| Blocked countries |
Russia China Belarus |
Selection of countries whose IP addresses should be blocked. Below, an overview of the current selection is also displayed in the form of a map.
You can select or deselect all countries using the corresponding buttons.
|
| Select all Deselect all
|
|
|
|
|
| DNS rebinding protection |
|
By enabling this feature, attackers are prevented from gaining control over local devices via the internet by automatically blocking DNS responses that contain private IP addresses. Both private IPv4 and private IPv6 addresses are blocked.
|
 Create profiles Security tab
|
| Extended DNS Rebinding Protection |
|
When activated , IPv6 addresses that are reserved for special network purposes such as documentation, tunneling or packet discarding are blocked. These are not typically used on the internet.
|
| IDN Homograph Attack protection |
|
By activating this option, domains that pretend to be other domains by misusing the large character encoding that is available with the introduction of Internationalized Domain Names (IDNs) are blocked. With this option, only domains with ASCII characters are permitted.
|
| Blocking of disguised third-party trackers |
|
The activation blocks third-party trackers that disguise themselves as first-party providers. This attack is also known as CNAME cloaking.
|
| Safe Search |
|
Activation filters the results in all major search engines, including images and videos.
|
| Restricted youtube mode |
|
By activating this, YouTube content for adults is filtered. All comments will also be hidden.
|
| Block Private Relay notemptyNew as of: 2.12 |
|
- When enabled , this feature blocks iCloud Private Relay and routes traffic through Cloud Shield
- This ensures devices remain fully protected—devices with Private Relay enabled bypass protection
- It is therefore recommended to enable this function
|
|
|
AI Filter AI Filter Experimental |
| The AI-based filter detects previously unknown threats through real-time risk analysis. Only domains that are not already classified by our content filter are checked.
|
 Create profiles AI filter tab
|
| notemptyNo data transfer: All analyses take place in the Securepoint infrastructure - there is no transmission to third parties!
Own AI development: The filter is based on Securepoint's own machine learning model - specifically trained on current threat patterns on the web.
|
| Activate AI Filter |
|
When activated , malicious domains are blocked with the Securepoint machine learning model, which has been trained with tens of thousands of benign and malicious domains.
|
| Rating |
|
Adjust the threshold individually to the security needs. The lower the threshold, the more potentially harmful pages will be blocked - even if this can lead to some false positives.
|
| 50% |
A page is blocked with a probability of 50%.
This setting offers the highest possible protection, but increases the likehood of false positives.
|
| 70% |
Blocks pages that are classified as threatening with a probability of least 70%.
Good balance between security and surfing comfort.
|
| 90% |
Ideal for uasers who want maximum freedom on the web while still being protected from clearly malicious pages.
With this setting, the risk of false positives is low, but potentially more threats remain undetected.
|
|
|
|
|
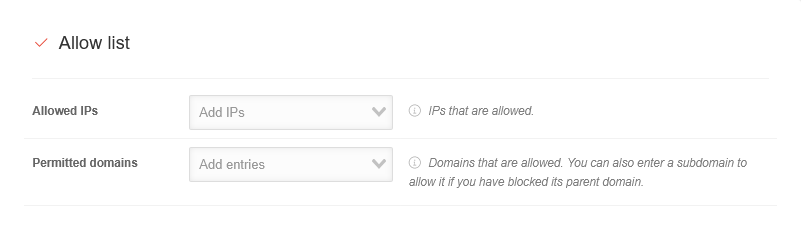
| Allowed IPs |
|
Explicitly allowed IP addresses (even if they are on the block list)
|
 Create profiles Allow list tab
|
| Allowed domains |
|
Domains that should be allowed. A subdomain can also be added to allow this if the associated higher domain is not allowed.
|
|
|
|
|
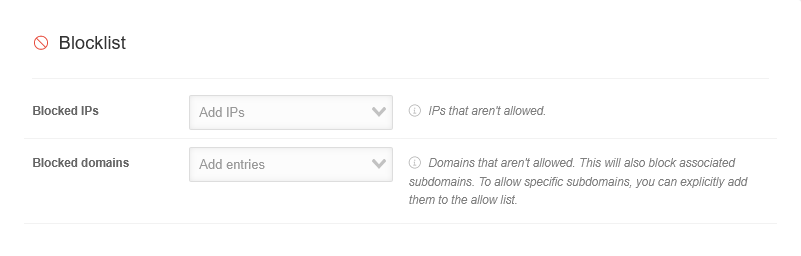
| Blocked IP's |
|
IP addresses that are to be blocked
|
 Create profiles tab block list
|
| Blocked domains |
|
Domains that are to be blocked. This also blocks all associated subdomains. If certain subdomains are to be allowed, they can be explicitly added to the allow list.
|
|
|
External Lists External Lists |
| Custom Blocklists |
Add Blocklist |
Adding custom blocklists. All common formats are supported, e.g. hosts and ABP.
|
 Create profiles External lists tab
|
| Custom Blocklists
|
| Activated |
|
When activated , the blocklist is activated
|
| Name |
|
Name of the blocklist
|
| URL |
|
URL of the blocklist
|
| Authentication notemptyNew as of: 2.12
|
| Authentication method |
No authentication |
Sets the authentication method for accessing the list
|
| No authentication |
Access to the list does not require authentication
|
| Basic-Authentication |
Access to the list requires Basic Authentication with a username and password
|
| Bearer-Token |
Access to the list requires a Bearer-Token
| |
Username
For the Basic-Authentication method |
|
The username for authentication
|
Password
For the Basic-Authentication method |
Show password
Hide password |
The password for authentication
|
Bearer-Token
For the Bearer-Token method |
Show password
Hide password |
Enter the required Bearer-Token
|
|
|
| HTTP-Header notemptyNew as of: 2.12 |
Add HTTP-Header |
Add custom HTTP headers for accessing the list
|
| Header
|
| Key |
X-Example-Header |
The key for the HTTP-Header
|
| Value |
12345 |
The value for the HTTP-Header key
|
|
|
| Custom Allowlists |
Add Blocklist |
Adding custom allowlists. All common formats are supported, e.g. hosts and ABP.
|
| Custom Allowlists
|
| Activated |
|
When activated , the allowlist is activated
|
| Name |
|
Name of the allowlist
|
| URL |
|
URL of the allowlisten
|
| Authentication notemptyNew as of: 2.12
|
| Authentication method |
No authentication |
Sets the authentication method for accessing the list
|
| No authentication |
Access to the list does not require authentication
|
| Basic-Authentication |
Access to the list requires Basic Authentication with a username and password
|
| Bearer-Token |
Access to the list requires a Bearer-Token
| |
Username
For the Basic-Authentication method |
|
The username for authentication
|
Password
For the Basic-Authentication method |
Show password
Hide password |
The password for authentication
|
Bearer-Token
For the Bearer-Token method |
Show password
Hide password |
Enter the required Bearer-Token
|
|
|
| HTTP-Header notemptyNew as of: 2.12 |
Add HTTP-Header |
Add custom HTTP headers for accessing the list
|
| Header
|
| Key |
X-Example-Header |
The key for the HTTP-Header
|
| Value |
12345 |
The value for the HTTP-Header key
|
|
|
DNS-Rewrites DNS-Rewrites |
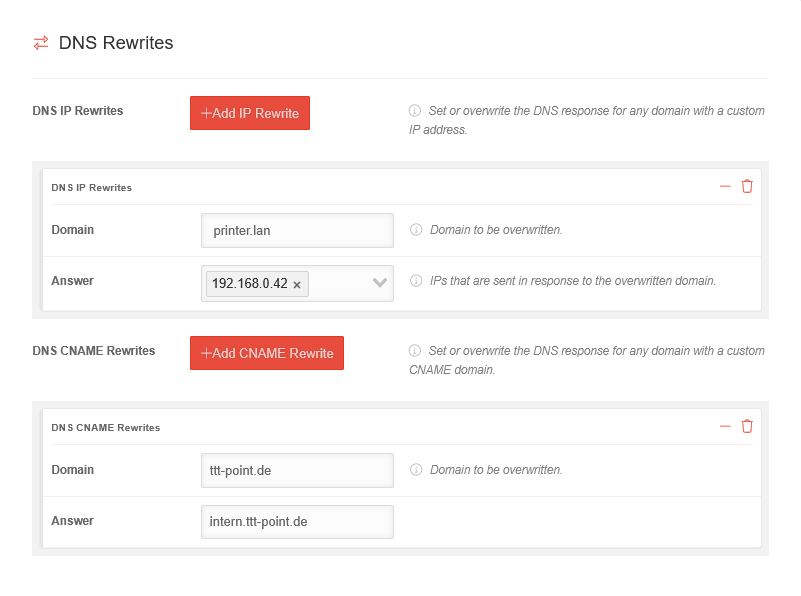
| DNS-IP-Rewrites |
Add IP-Rewrite |
Define or overwrite the DNS response for any domain. Any IP address can be used as the response.
|
 Create profiles tab DNS-Rewrites
|
| DNS-IP-Rewrites
|
| Domain |
printer.lan |
Domain which is to be overwritten
|
| Answer |
192.168.0.42 |
IPs that are sent in response to the overwritten domain
|
|
|
| DNS-CNAME-Rewrites |
Add CNAME rewrites |
Define or overwrite the DNS response for any domain. Any other domain can be used as the response.
|
| DNS-CNAME-Rewrites
|
| Domain |
ttt-point.de |
Domain which is to be overwritten
|
| Answer |
intern.ttt-point.de |
Domain that is sent in response to the overwritten domain
|
|
|
|
|
| Activate protocols |
|
Activates the recording of DNS logs. This setting is required for evaluating the statistics.
|
 Create profiles tab Protocols
|
Log domains
is only displayed if Enable protocols is activated |
|
If this setting is set, domain names are saved for the statistics and logs. Otherwise, a placeholder is displayed.
|
Log device names
is only displayed if Enable protocols is activated |
|
If this setting is set, the device names for the statistics and logs are saved independently of the client setting.
|
|
|
|
|
| Performance
|
 Create profiles Tab Other
|
| Cache-Boost |
|
Reduces the number of DNS queries by enforcing a minimum TTL (Time-To-Live) of 5 minutes. Higher TTLs are not overwritten.
|
| Behavior for blocked domains
|
| Behaviour |
Block page |
Specifies the action for blocked domains
|
| 0.0.0.0 / ::0 |
Returns an address that cannot be routed
|
| Block page |
Displays a block page as soon as a domain is blocked. In some cases an HTTPS warning may be displayed, this can be avoided by downloading and installing the Securepoint Certification Authority.
|
| User defines IPs |
Responds with user-defined IP addresses
|
| User defined CNAME |
Responds with a user-defined CNAME
|
| NXDOMAIN |
Tells the client that the requested domain does not exist
|
| REFUSED |
Tells the client that the DNS server refuses to answer the request
|
|
|
|