This article includes descriptions of third-party software and is based on the status at the time this page was created.
Changes to the user interface on the part of the manufacturer are possible at any time and must be taken into account accordingly in the implementation.
All information without warranty.
Last adaptation to the version: 2025.10
- New Office 365 Integration with Assistant
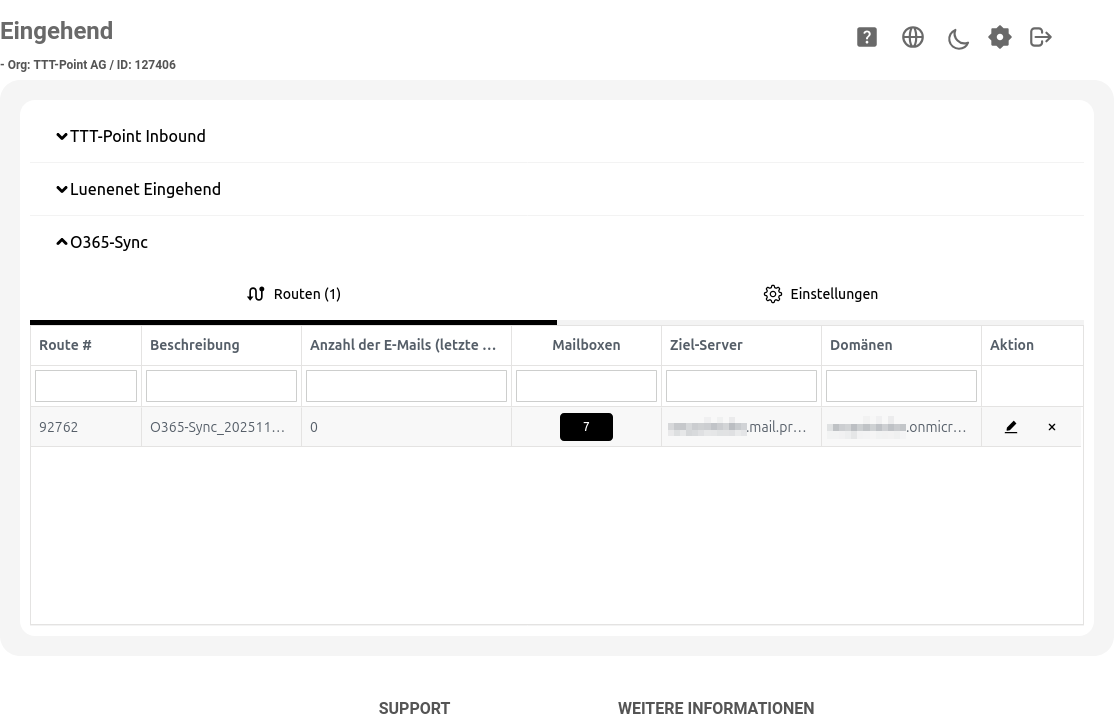
- Routes are authenticated via a TXT record in the domain and are immediately available
- Active routes are now displayed with an enabled button
Introduction
An email sent to an Microsoft office 365 mailbox is first received by the upstream Securepoint Mail Security.
Securepoint Mail Security scans the email for spam and malware. If non is detected, Mail Security forwards the email to the Office 365 mailbox.
Office 365 Integration
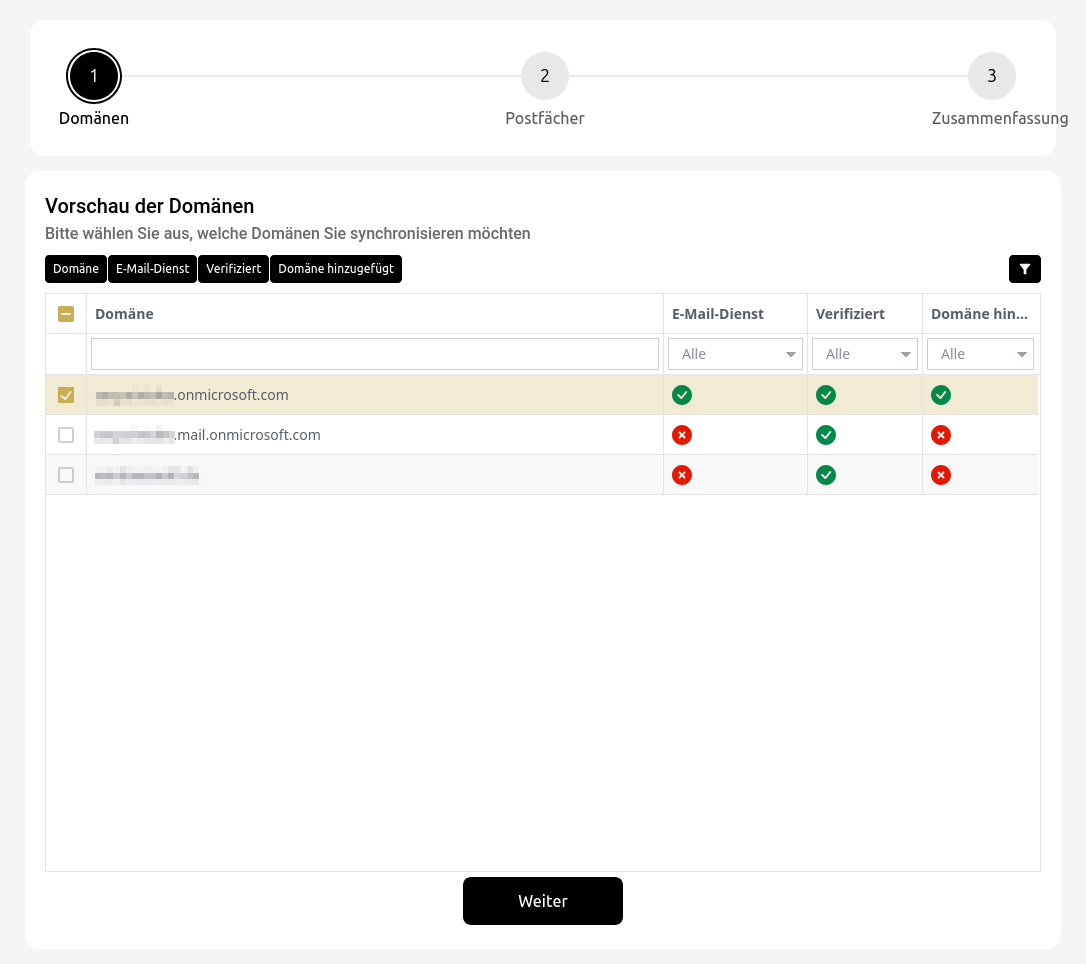
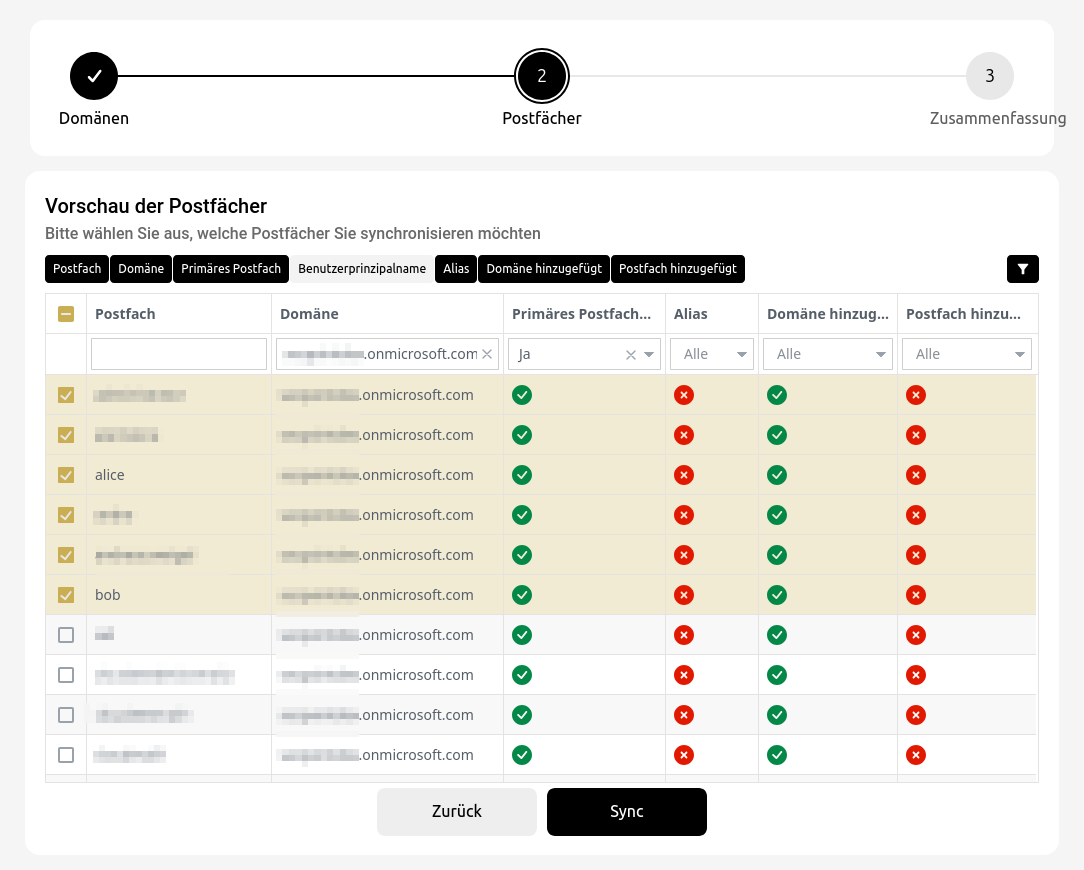
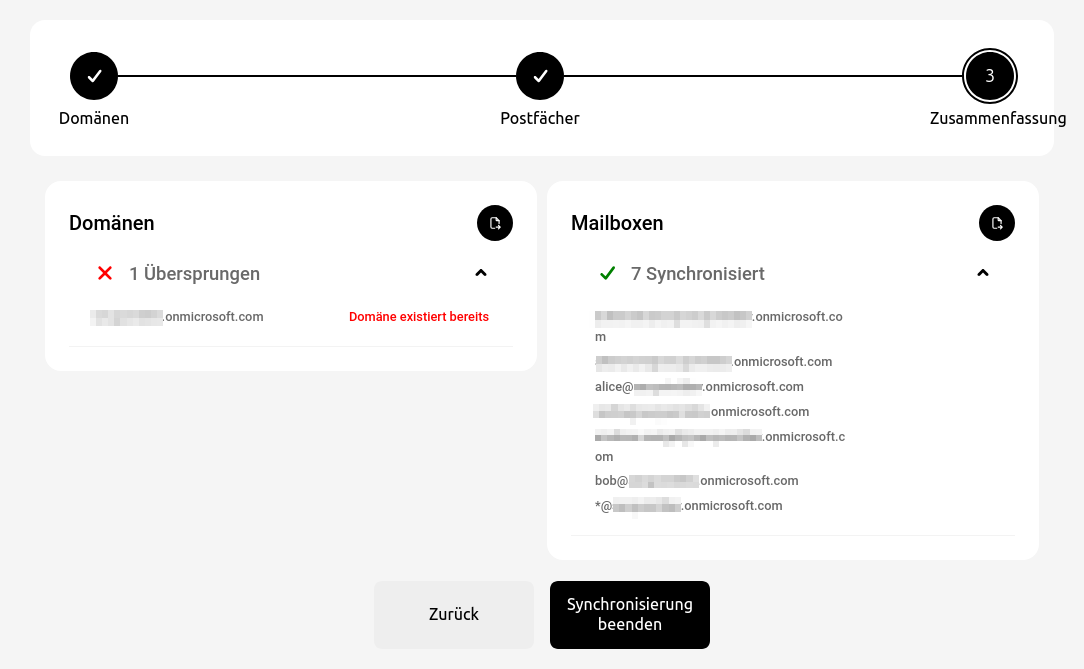
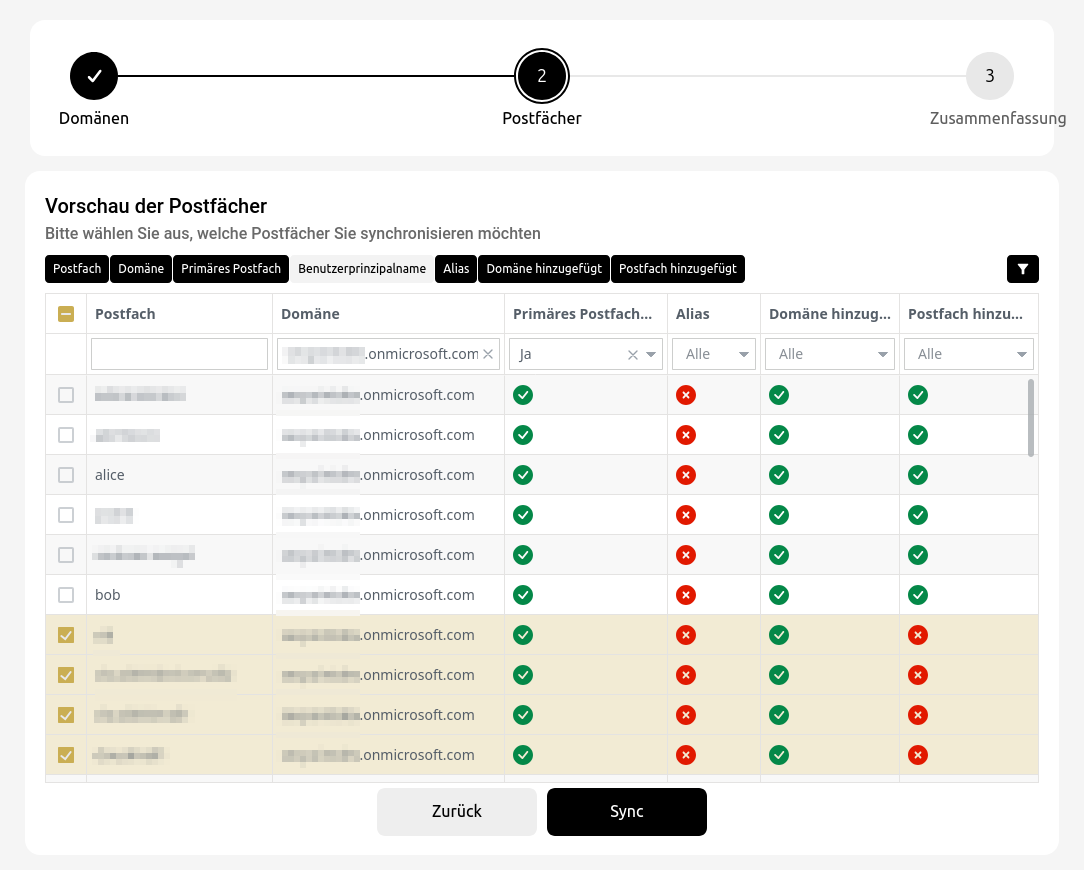
notempty
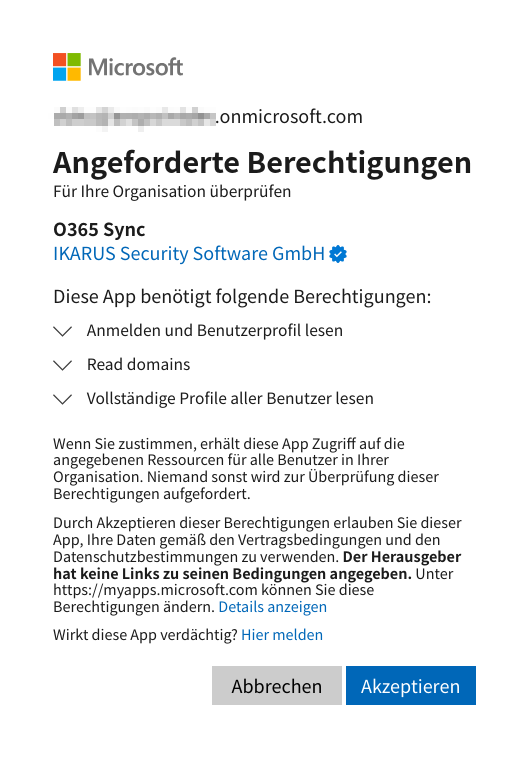
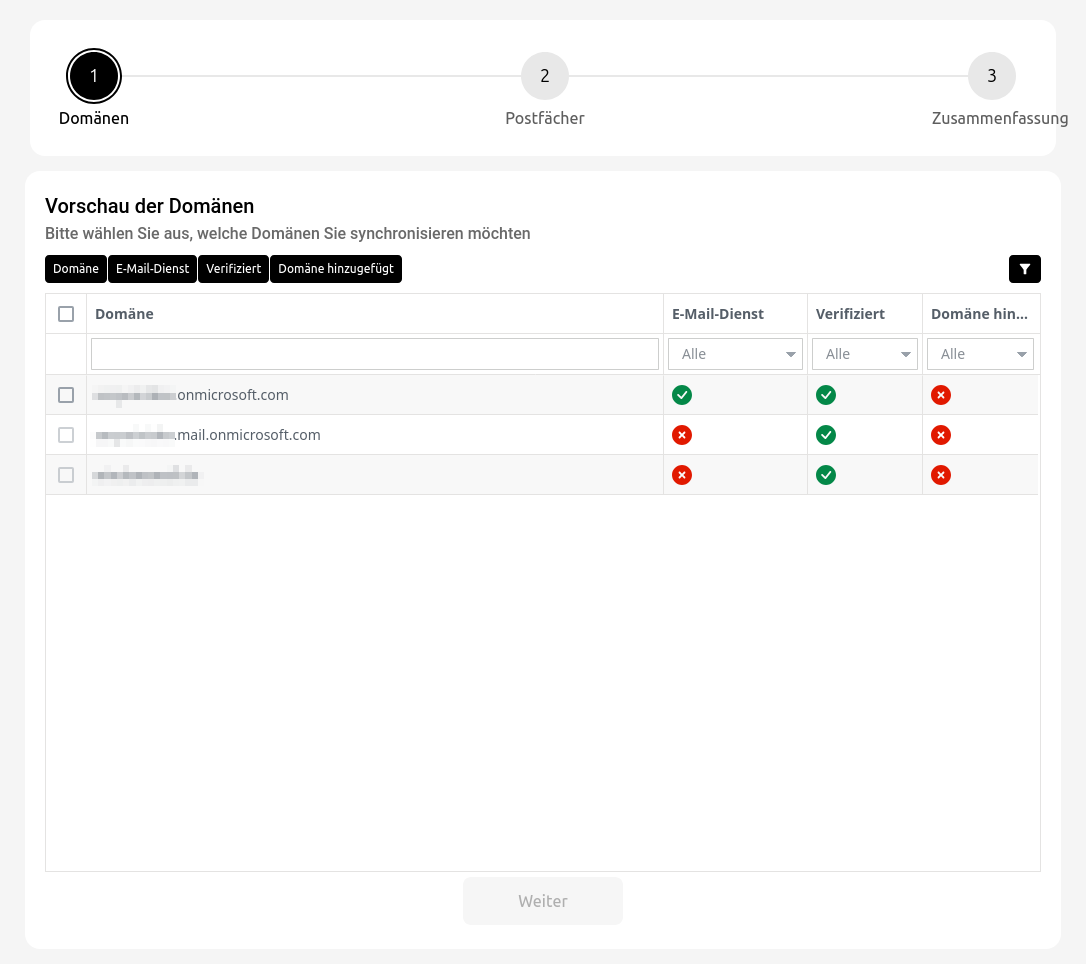
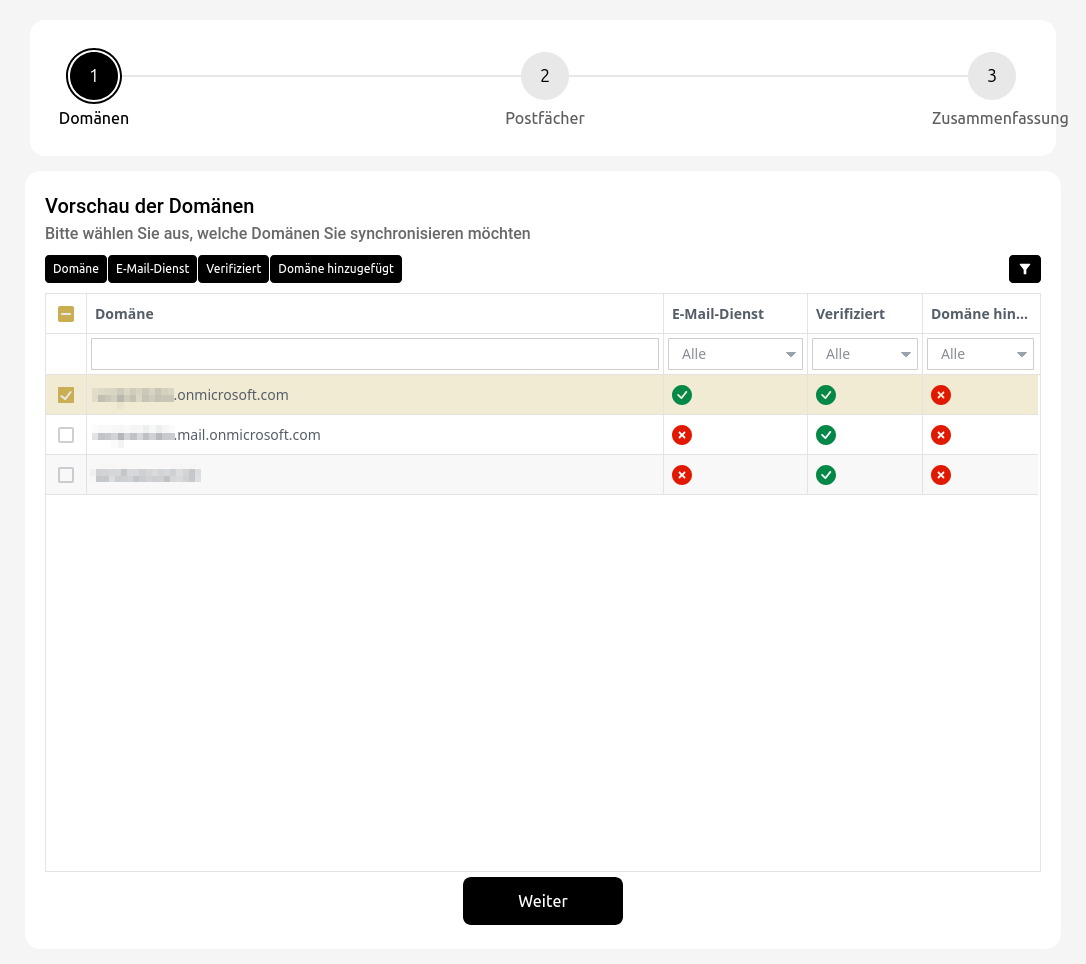
Office 365 integration with assistant
The following setup steps are required:
- Set up an inbound and outbound route in Mail Security
- Configure Office 365, assign domain, set up receive and send connectors
- Adjust the DNS entries
Set up Microsoft 365
Configure the receive connector
A receive connector must be configured so that the Microsoft Exchange Online can receive emails from Mail Security.
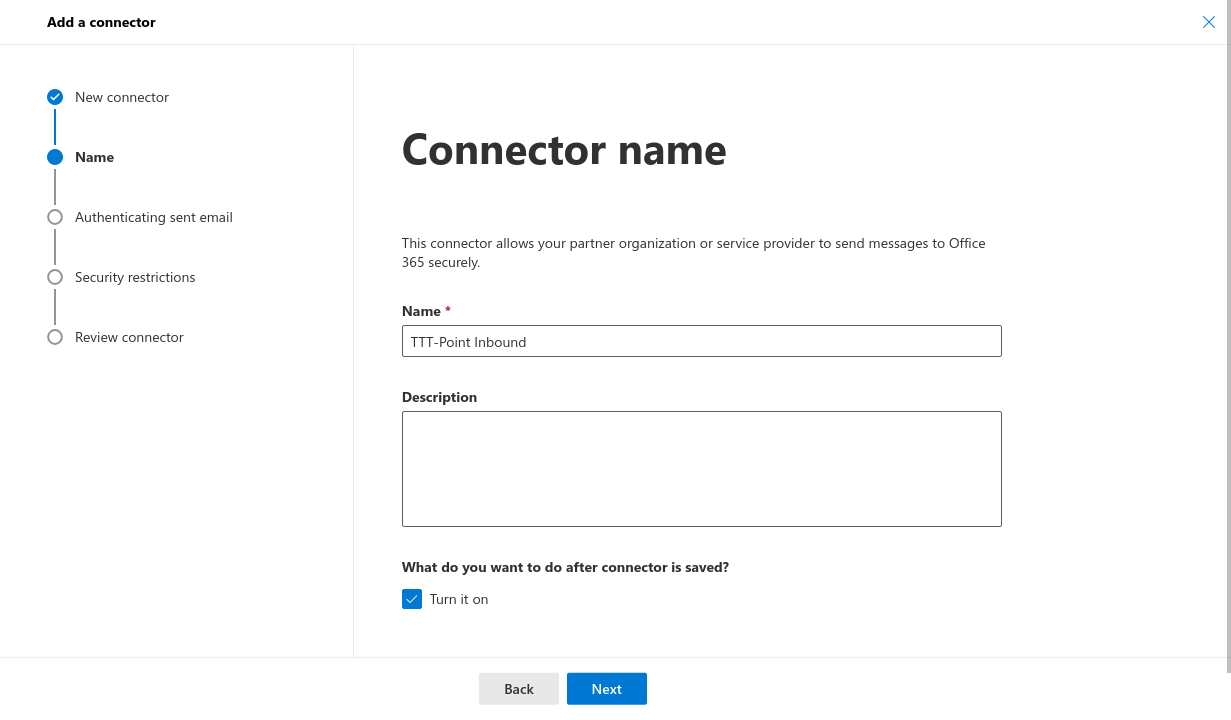
- Log in at https://admin.exchange.microsoft.com admin.exchange.microsoft.com], under Mail flow→ Connectors click the Add connector button
- New Connector: Select Connection from Partner organization, Connection to will then be filled in automatically
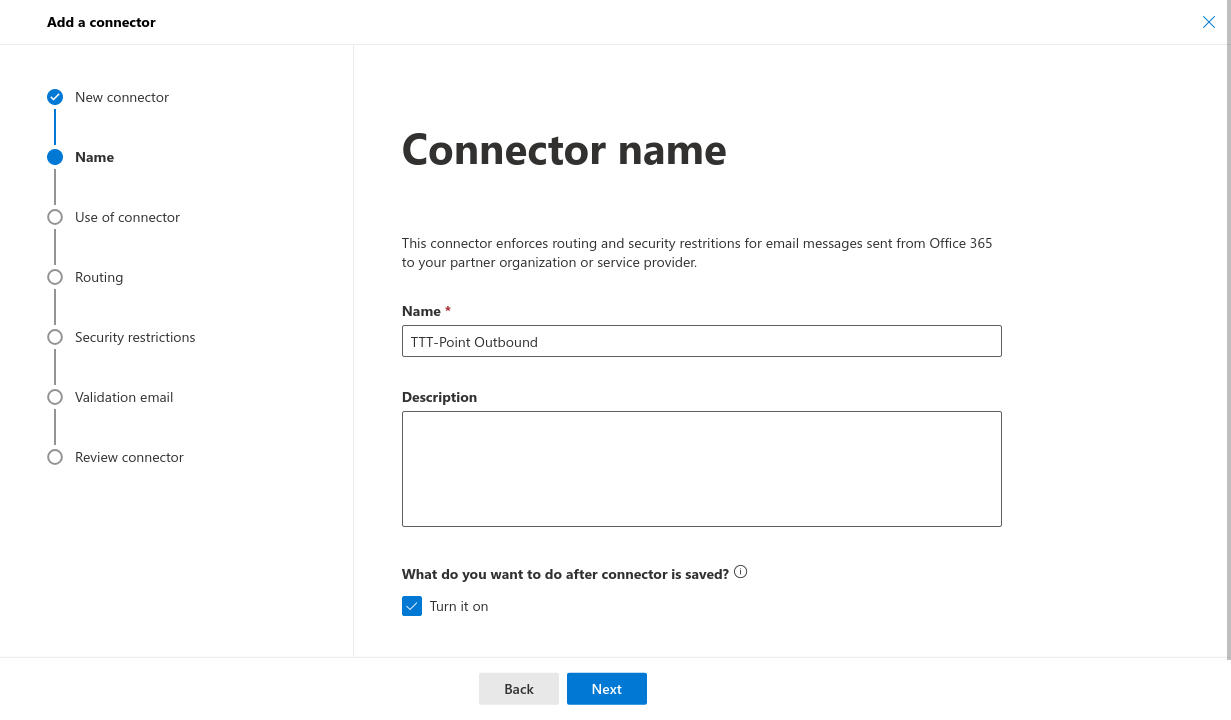
- Name: Choose an appropriate name and optionally a description
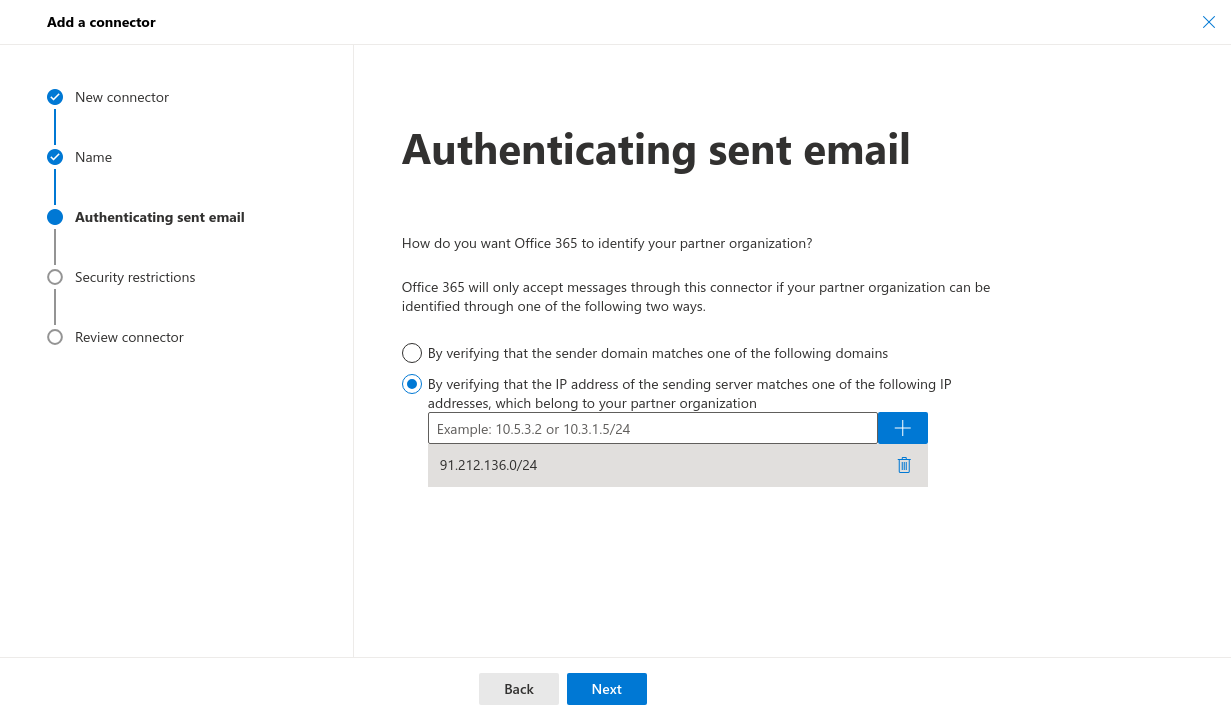
- Sent email will be authenticated: select the second option and enter the IP address from the welcome email, then click on to ensure the IP address is added the welcome email is received after ordering mail security
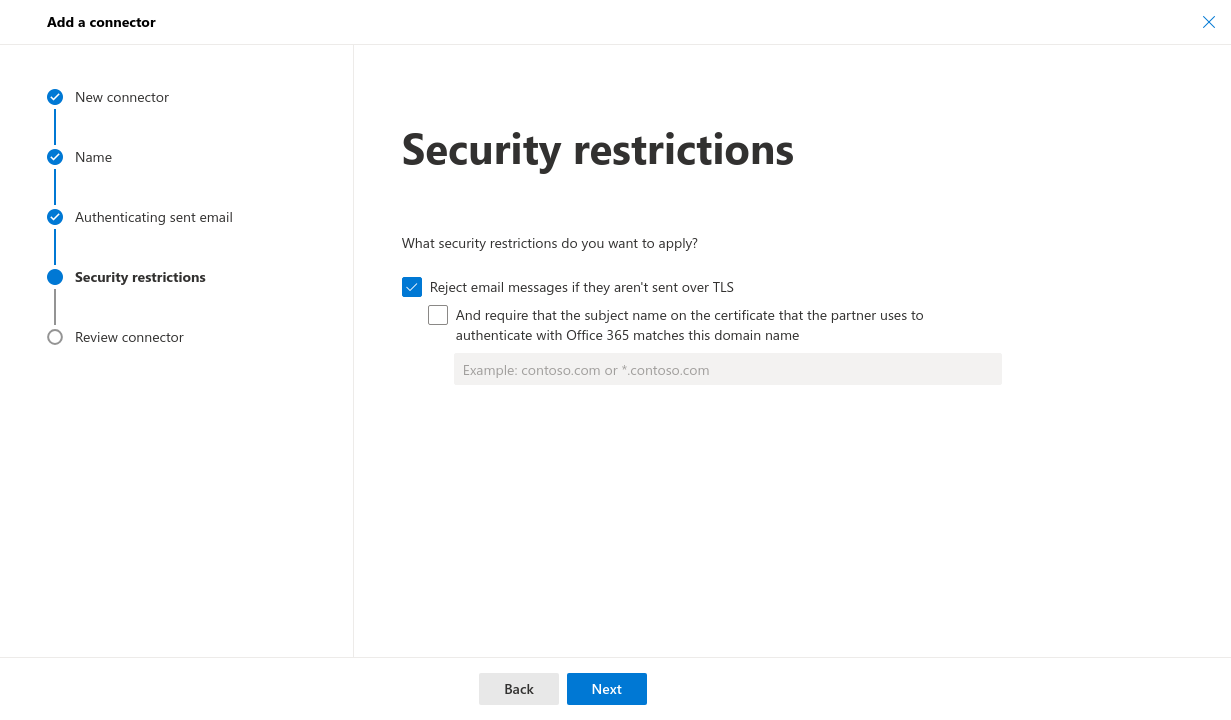
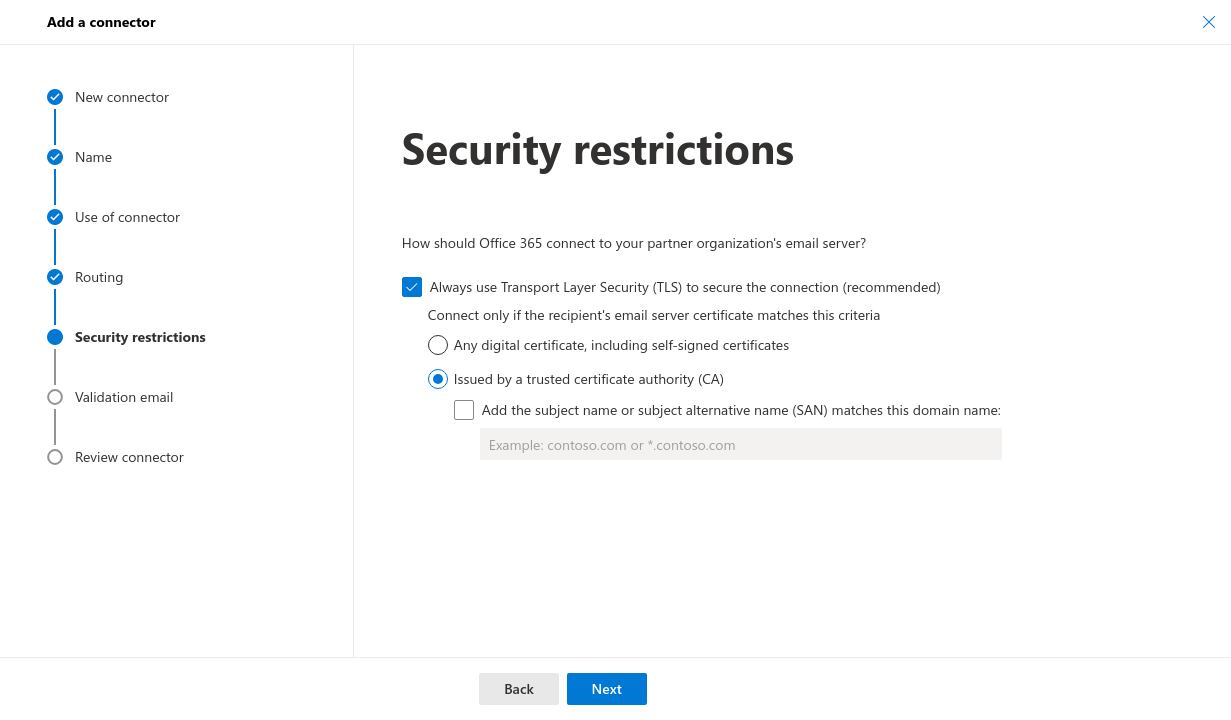
- Security restrictions: The desired security restrictions can be configured
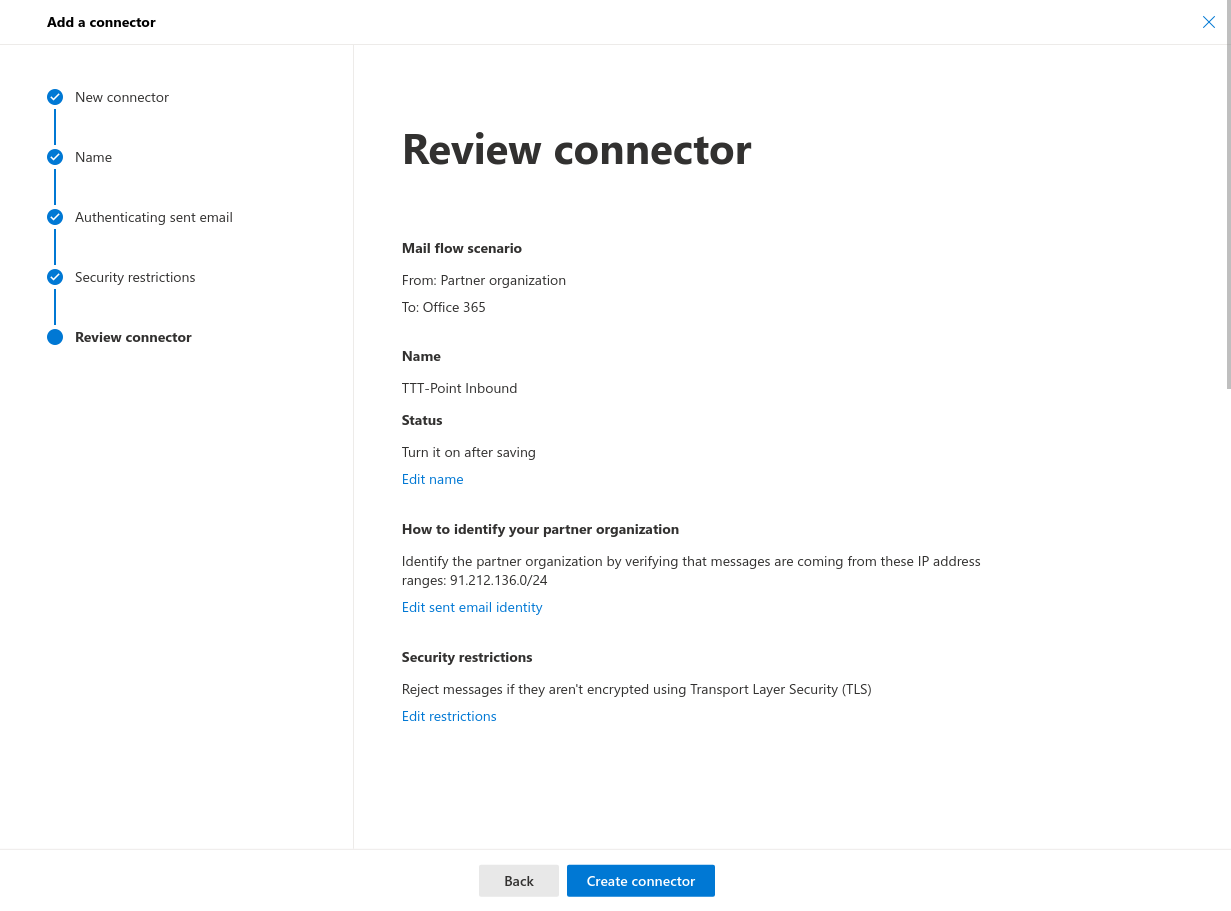
- Verify connector: After succesfully testing the configuration, the receive connector is ready to use
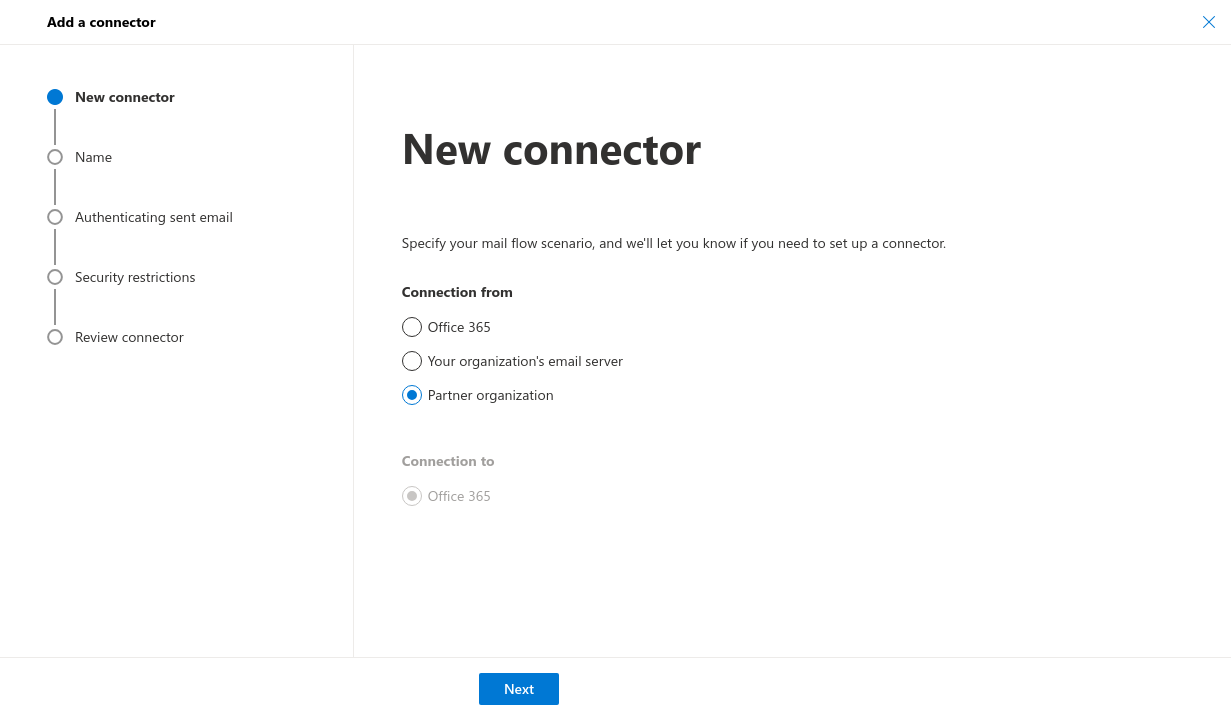
- Log in at admin.exchange.microsoft.com
- Under Mail flow → Connectors click the Add connector button
- New connector select Connection from Partner organization
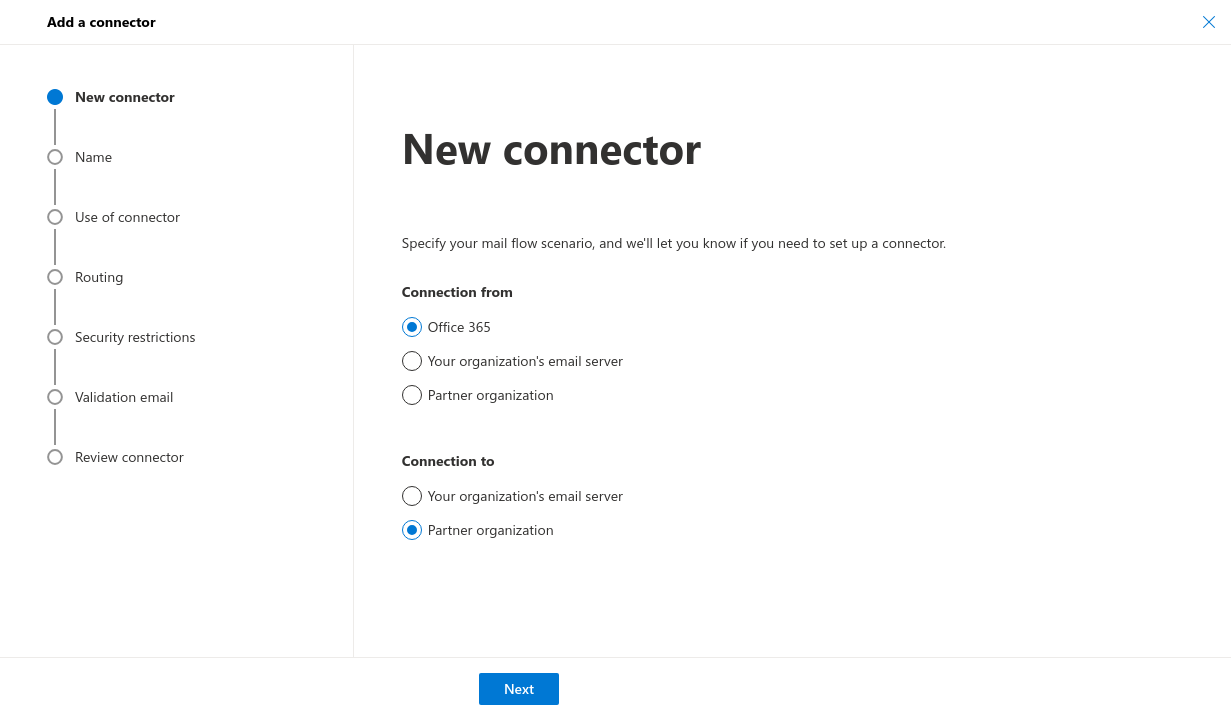
Configure send connector
A send connector must be configured so that Microsoft Exchange can send emails to Securepoint Mail Security
- Log in at admin.exchange.microsoft.com, under Mail flow → Connectors, click the Add connector button
- New Connector: Select Connection from Office 365, Connection with Partnerorganisation
- name: Choose an appropriate name and optionally add an description
- Usage of the connector: Only, when I have set up a transport rule that redirects messages to this connector
- Routing: route email through these smarthosts and use the smarthost from the outbound route in Mail Security under the Relay section
- Security restrictions: Configure as desired
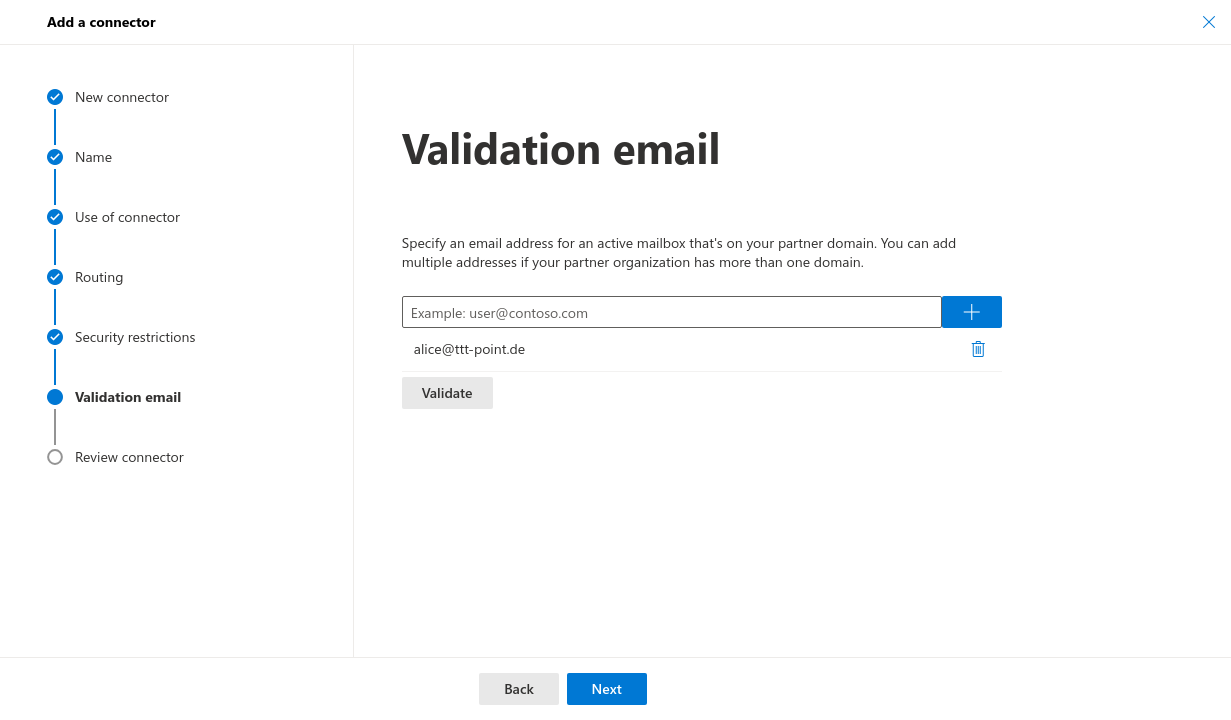
- Validation email: Email address for verification
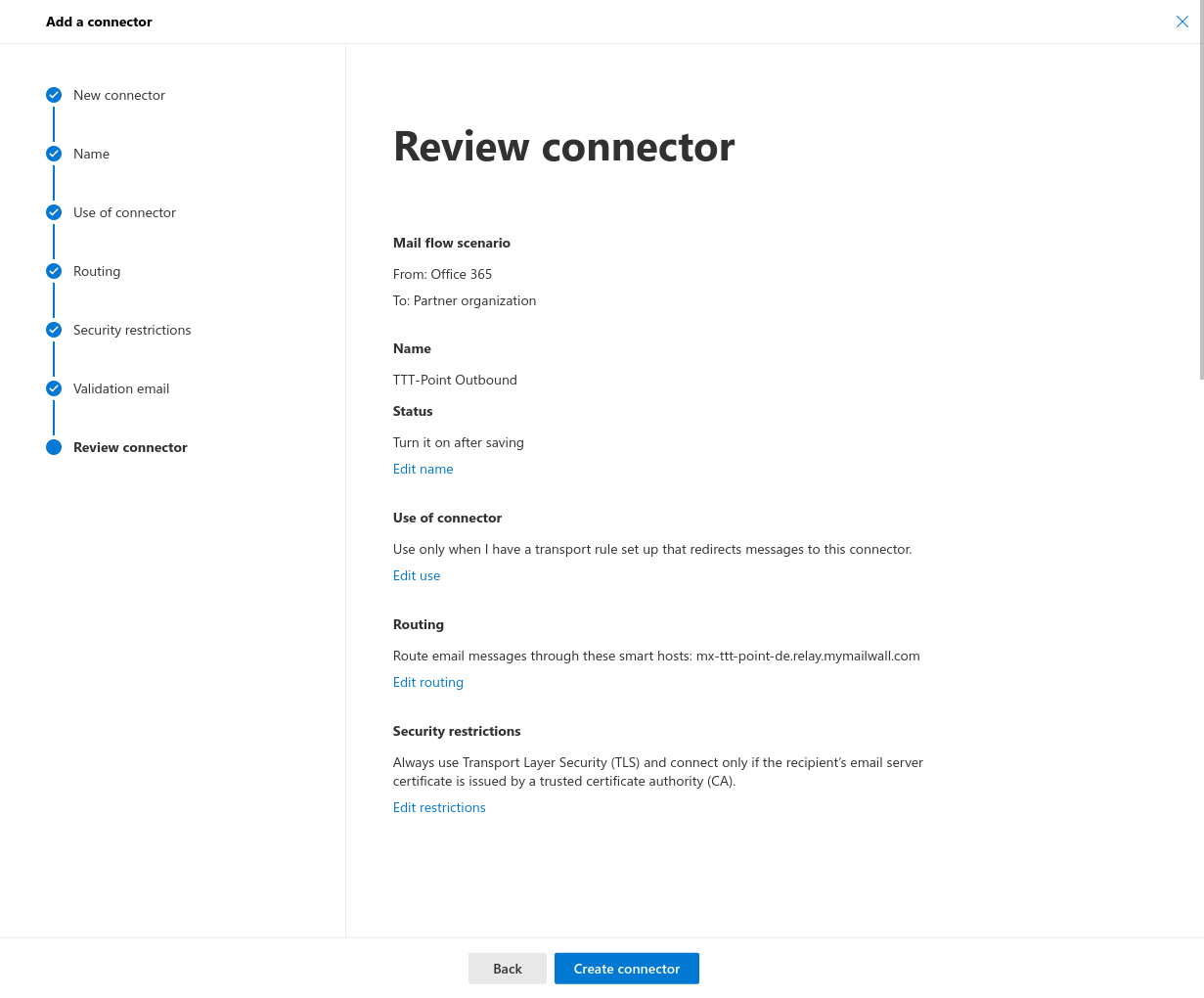
- Verify connector: After succesfully testing the configuration, the send connector is ready for use
Afterward, a rule must be added to ensure this send connector can be used.
- Log in at admin.exchange.microsoft.com
- Under Mail flow→ Connectors click the Add connector button
- New connector Select Connection from Office 365
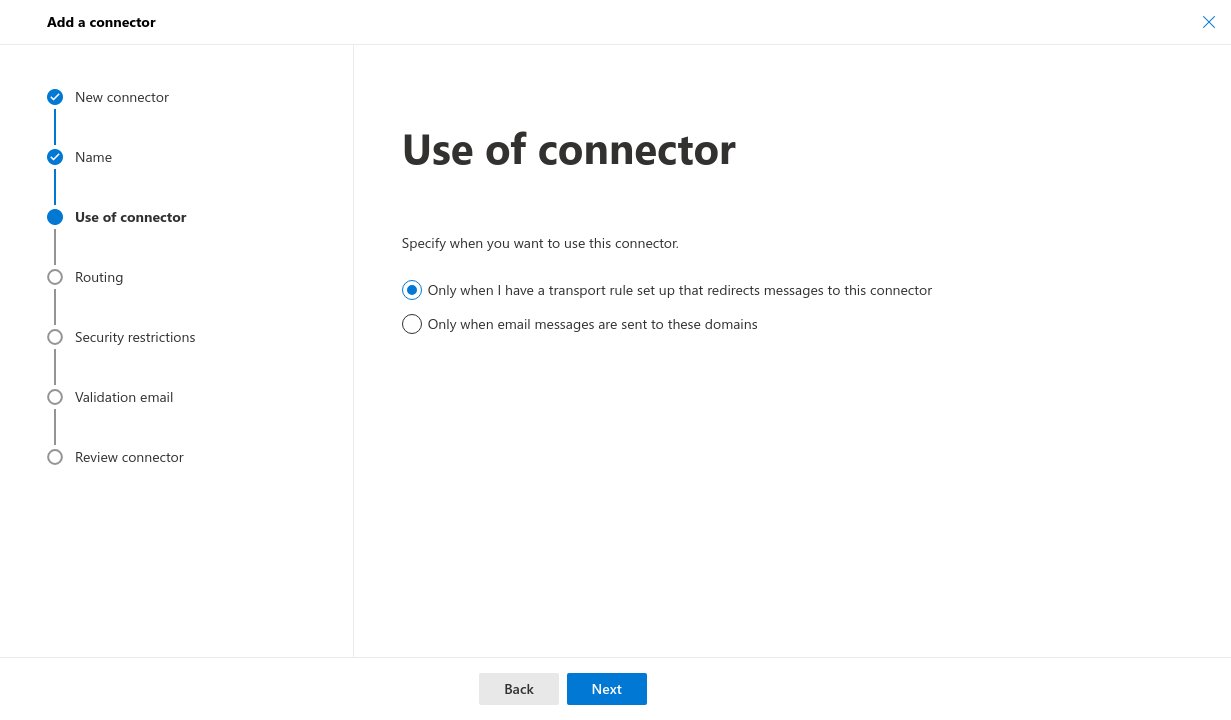
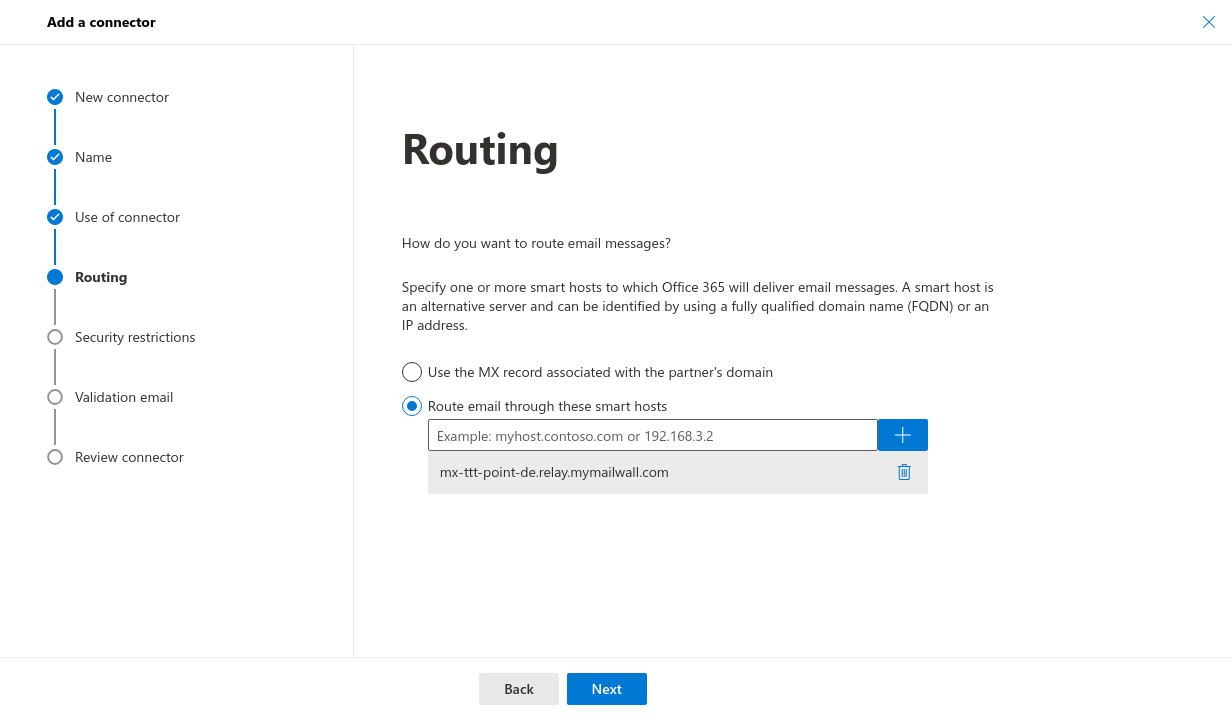
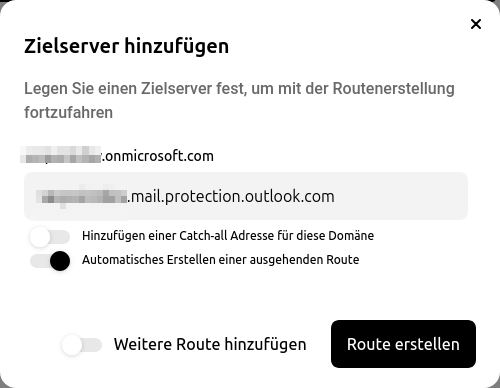
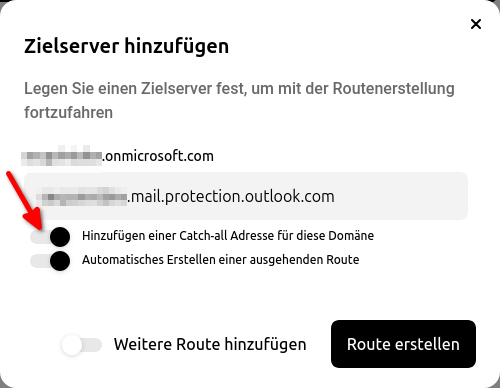
- This always follows the pattern meine-domain-de.relay.mymailwall.com Vorlage:Expand2The specific relay domain can be viewed under Mailsecurity / Outgoing / Customer / Tab Routes / Edit route / Relay
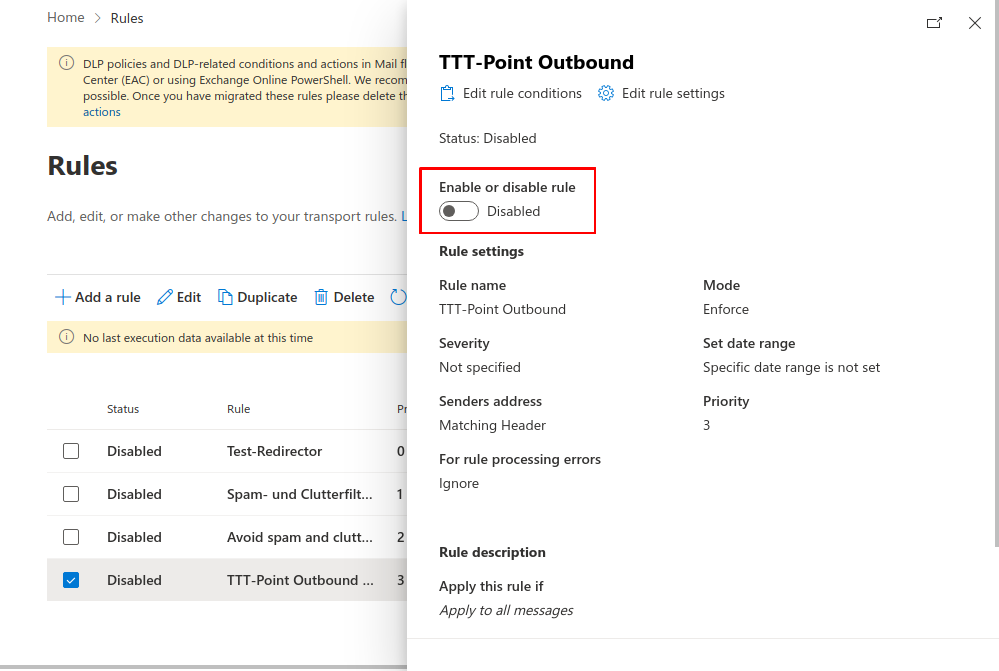
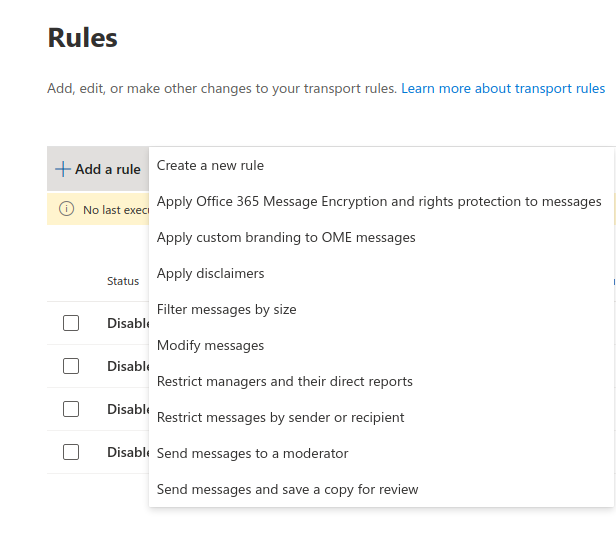
Add rule
After the send connector has been set up, a rule must be created in Microsoft Office 365 to ensure that this connector can be used.
- Log in at admin.exchange.microsoft.com, under Mail flow → Rules click the Add rule button
- In the burger menu, select Create a new rule
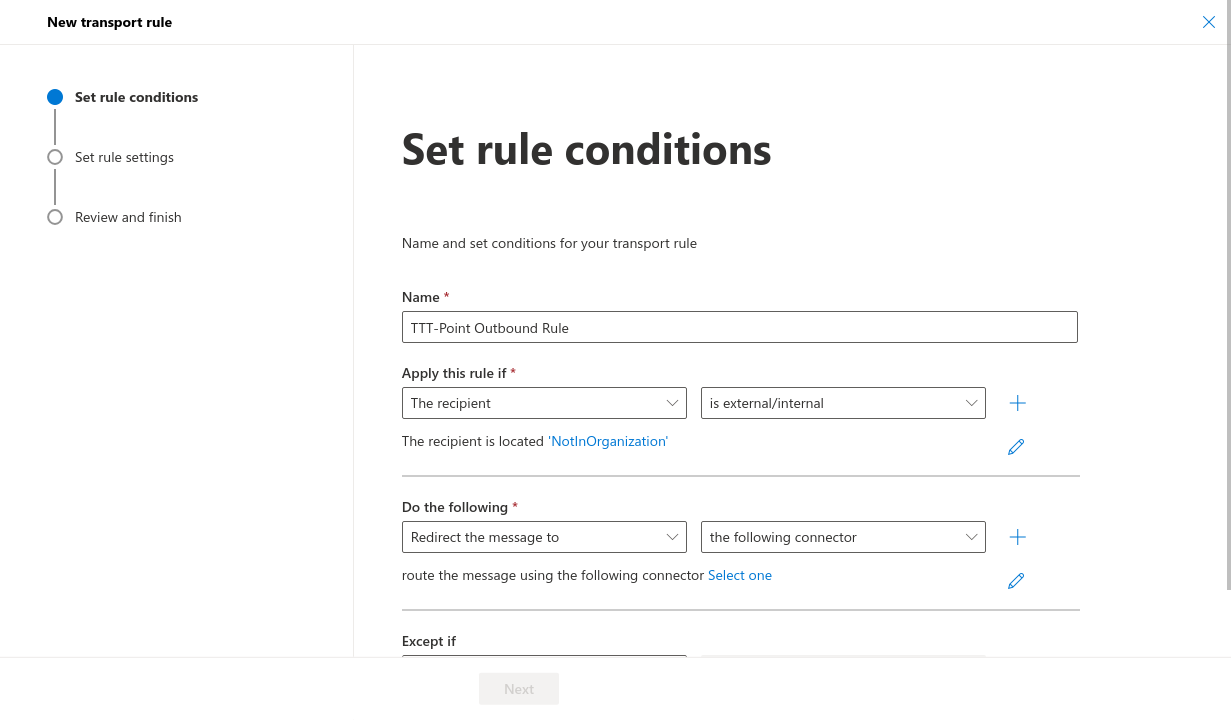
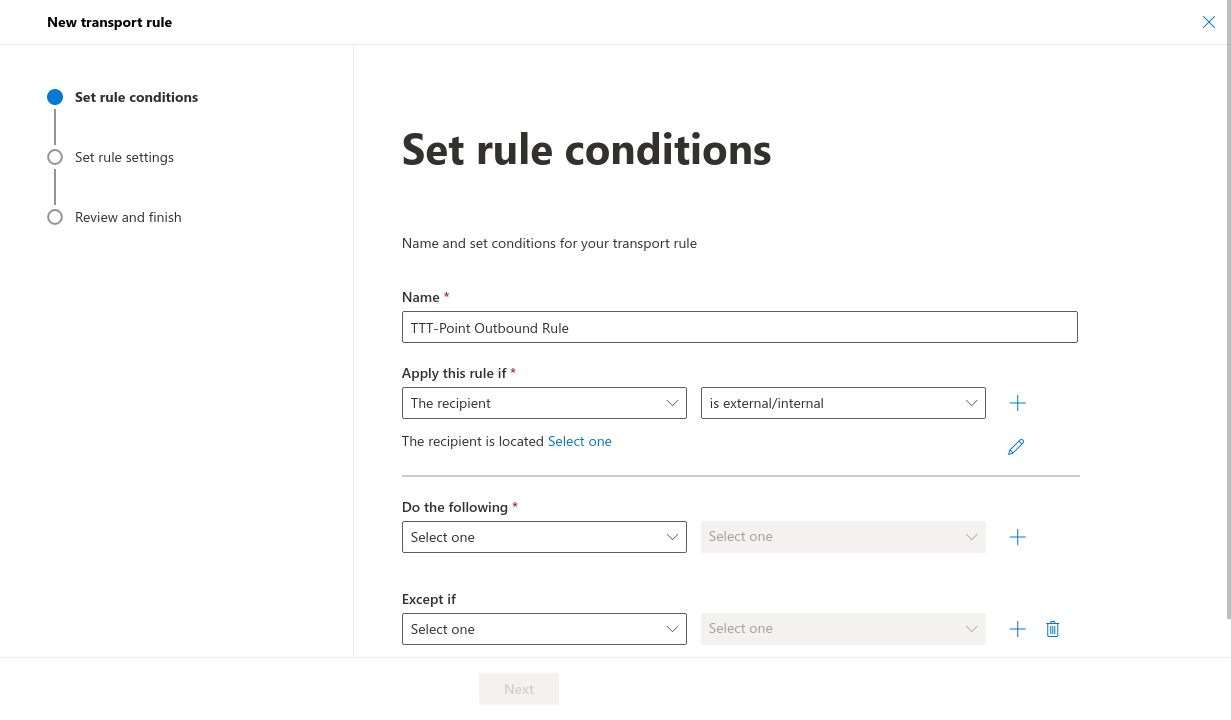
- Set the rule conditions:
- Choose an appropriate name
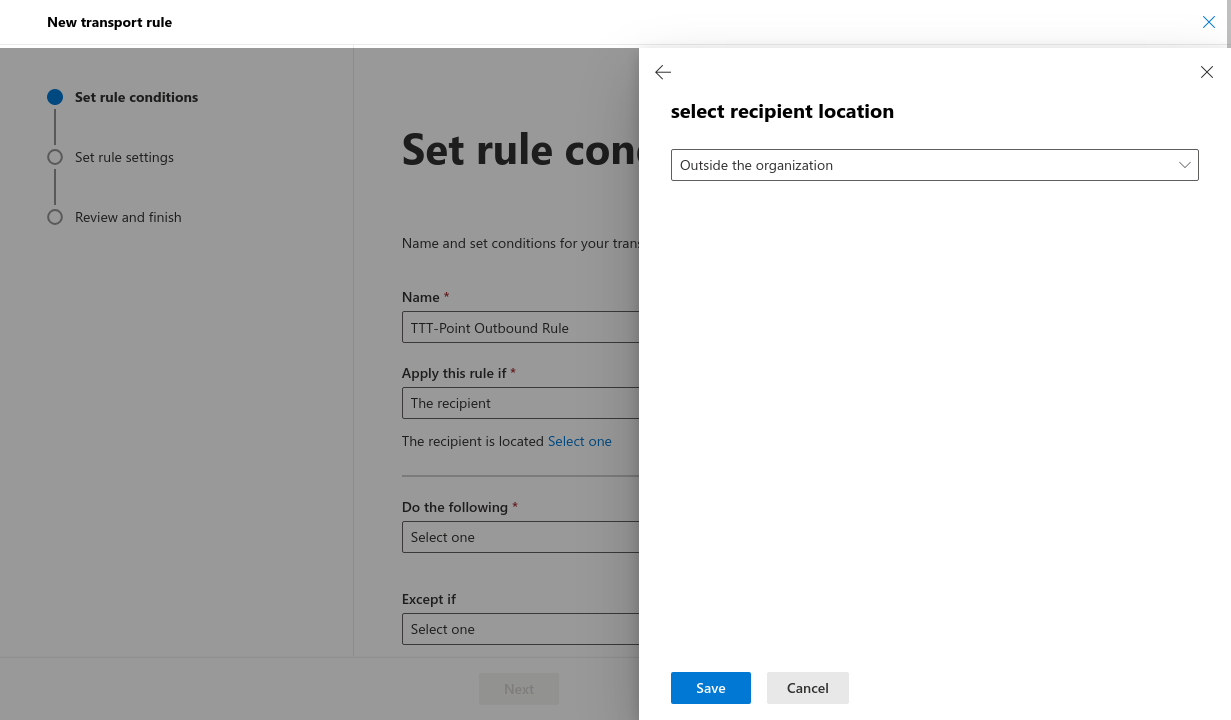
- Apply this rule, if: the recipient is external/internal outside the organization
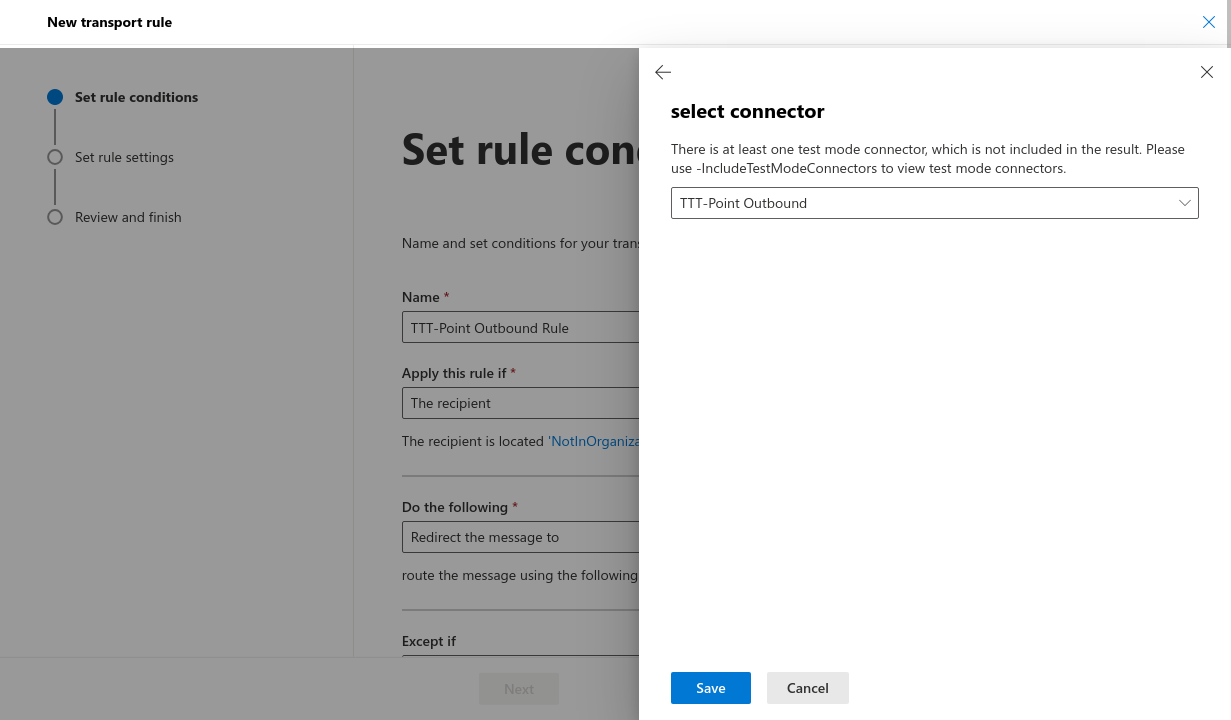
- Proceed as followed: Redirect message to the following connector and select the previously created connector there
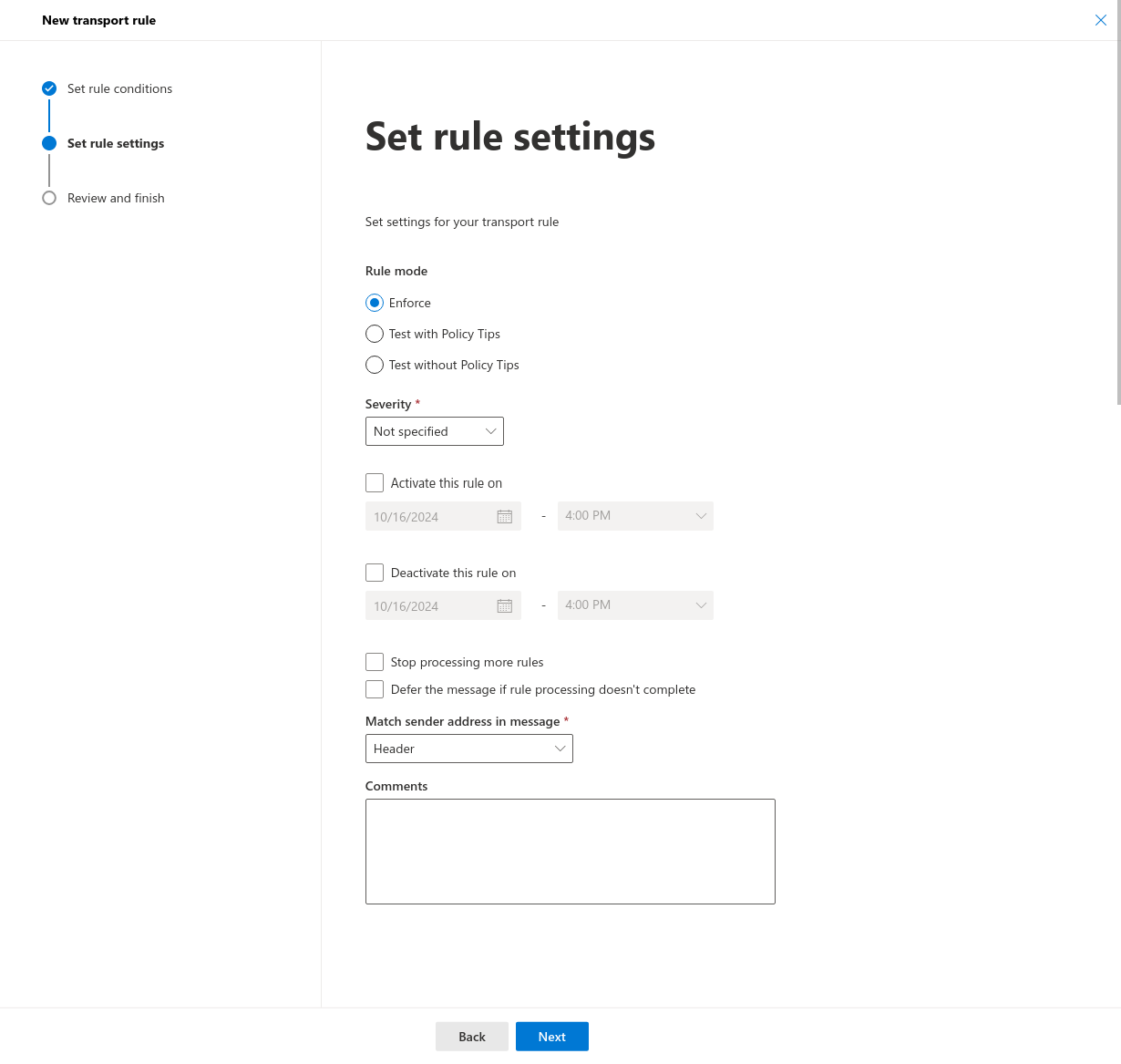
- Set rule settings: Adjust the conditions of this rule as desired
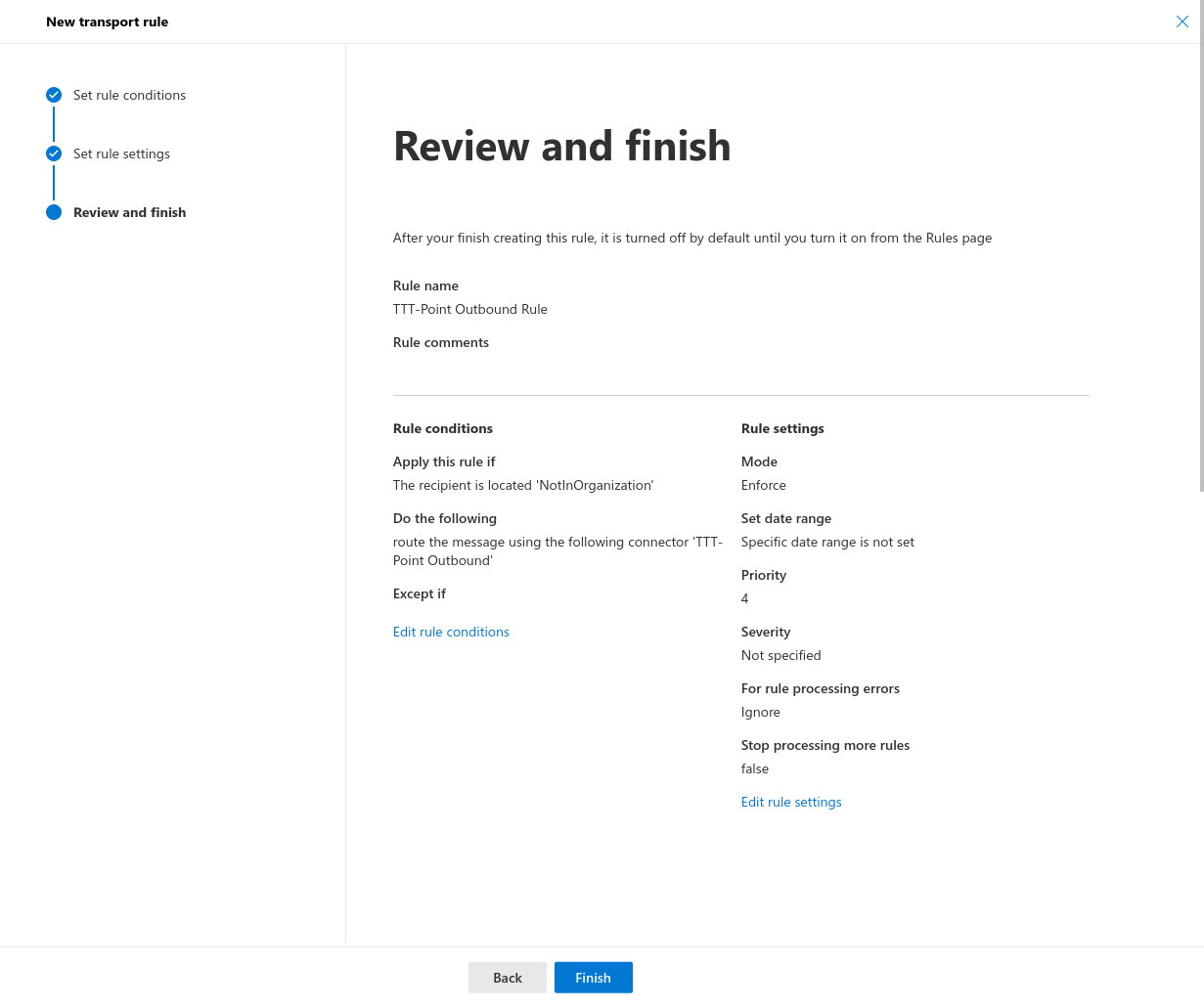
- Review and complete: The configuration can be reviewed again and corrected if necessary
- Use the Finish button to create this rule
To minimize downtime and avoid potential errors, the rule should only be activated after the MX record has already been switched to
Mail Security!
- Log in at admin.exchange.microsoft.com, under Mail flow → Rules
Click the Add rule button
- In the burger menu, select Crate a new rule
Adjust DNS entries
- The MX record must be set to mx.mymailwall.com
- the SPF record must be updated to include mymailwall.com
mx.ttt-point.de mail is handled by 10 mx.mymailwall.com.
Once the DNS entries have been succesfully redirected, the previously created rule can be activated