Last adaptation to the version: 14.1.1 (11.2025)
- BetaFor participants on the Beta Channel only:
- Servergruppen und Sites werden in einer gemeinsamen Tabelle angezeigt
- Regex expressions of the ACL sets can consider/ignore upper and lower case (v14.1.0)
- Hinweis, das Sites mindestens ein ACL Set mit dstdomain beinhalten müssen (v14.1.0)
notempty
- With v12.7.0, nginx can be selected as the reverse proxy engine
- Changing the engine will most likely result in an adjustment of the configuration, as each engine supports different features.
- Unsupported settings are marked after the changeover
Intended use
With a reverse proxy, one can control access to the "internal" web servers from the Internet. In contrast to a port forwarding, dedicated filter rules can be created via the reverse proxy. In addition, with only one public IP address, several internal web servers can be addressed based on the domain.
Another highlight is offered by the load balancing. Servers can be combined into groups, to which the requests are then distributed using the selected algorithm (e.g. Round-Robin).
Requirements
The following values are assumed for the example configuration:
- Web server with the private IP: 10.1.0.150
- Domain: www.ttt-point.de
Preparations
- Attention:
If the web server is also to be accessed via https, the port of the Userinterface must be changed first.
UTMuser@firewall.name.fqdnNetwork 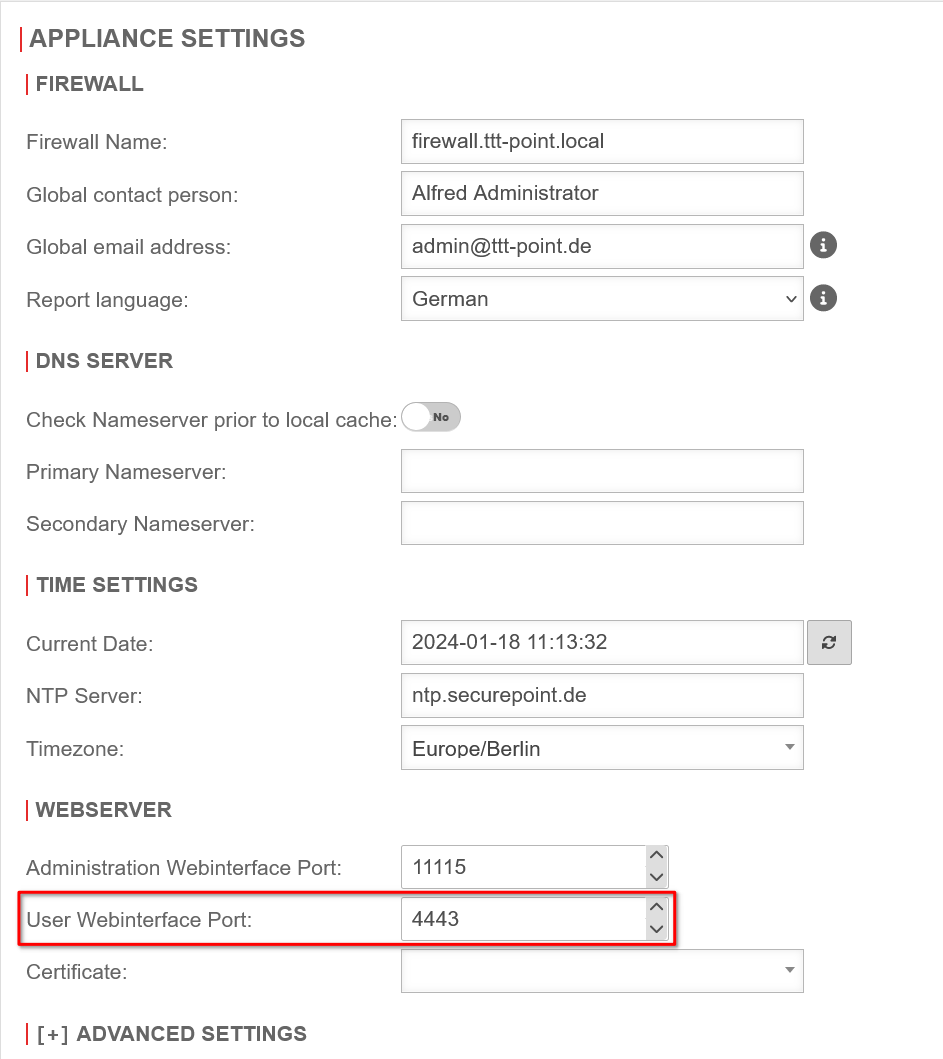
The settings for this are in the menu Area Appliance Settings in the section
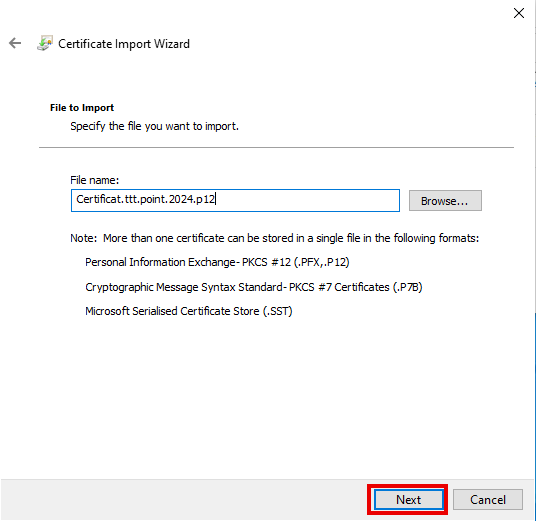
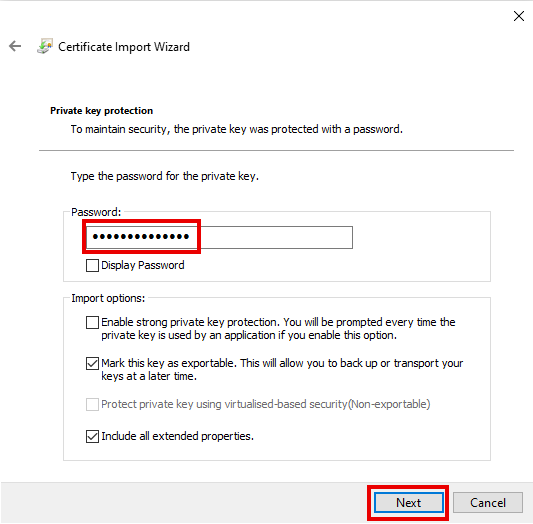
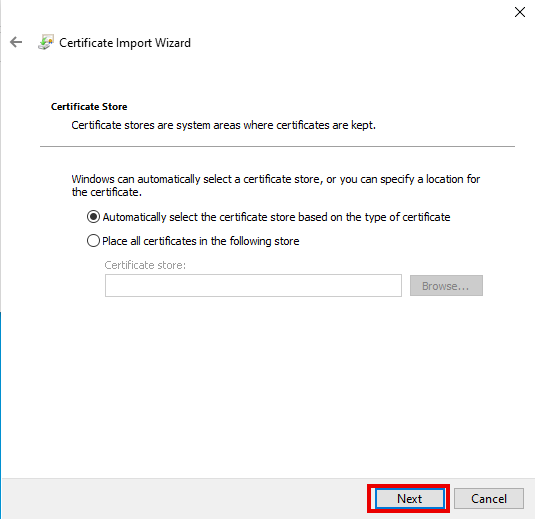
- For https, the reverse proxy needs a certificate to accept the encrypted connection.
- For this, a certificate is used from
In this example, a wildcard certificate *.ttt-point.de is used.
Packet filter rule
For the reverse proxy to be reachable, the following packet filter rule must be in place. This can be checked under . If this is not present, will add this rule.
| # | Source | Destination | Service | NAT | Logging | Acion | Active | ||
| Accept | On |
Use multiple IP addresses differently
notemptyFor this, the rule of the reverse proxy must explicitly specify that the “external interface” of the specific IP should be used as the destination. For the other use, the traffic is redirected using DestNAT, i.e. the traffic arrives on port 443, but is then redirected to another port (e.g. 1194 for VPN) using a packet filter rule.
Setup wizard | |||
| Under with the button the wizzard can be opened in the Header. | |||
Step 1 - Internal | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationReverse-Proxy 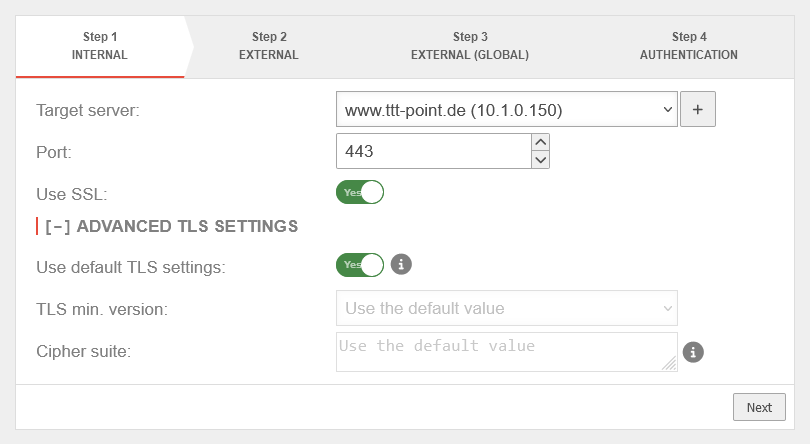 Target server already exists as a network object Target server already exists as a network object
|
|---|---|---|---|
| Target Server: | If the host has already been created as a network object, it can be selected directly in the drop-down menu. | ||
| Add network object | If no network object has been created yet, a network object can be created using this button. | ||
| Port: | 443 | The web server should be accessed via an encrypted connection. | |
| Use SSL: | On | Determines whether SSL can be used | |
[ - ] Advanced settings notempty These TLS settings apply to the connection between this appliance and the (local) server. For TLS settings between the clients and this appliance, the settings in the Area Reverse-Proxy dialog apply. | |||
| Use default TLS settings: | Yes | Allows connections with TLS 1.2 or 1.3 only | |
| Minimal TLS version: | The outdated TLS versions 1.1 and 1.0 can be selected. | ||
| Cipher-Suite: | Standardwert verwenden | Note that to directly use a OpenSSL security level, the notation @SECLEVEL=N can be used in the cipher string, where N represents the selected level from 0 to 5.
| |
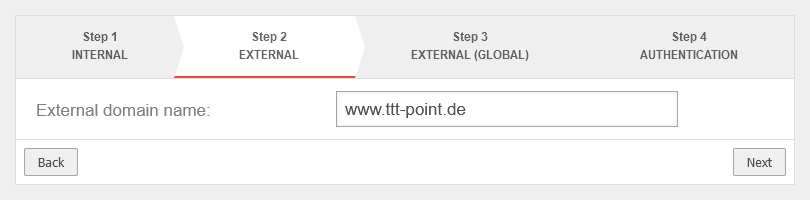
Step 2 - External | |||
| External domain name: | www.ttt-point.de | Here you enter how the server behind the UTM is addressed. |
 |
Step 3 - External (Global) | |||
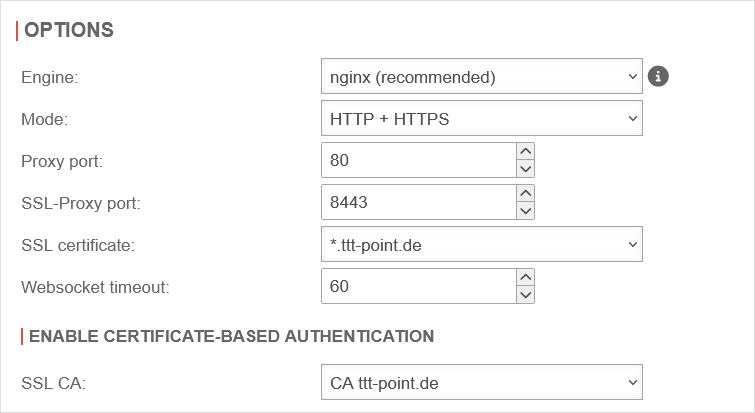
| Mode | Mode to be used | 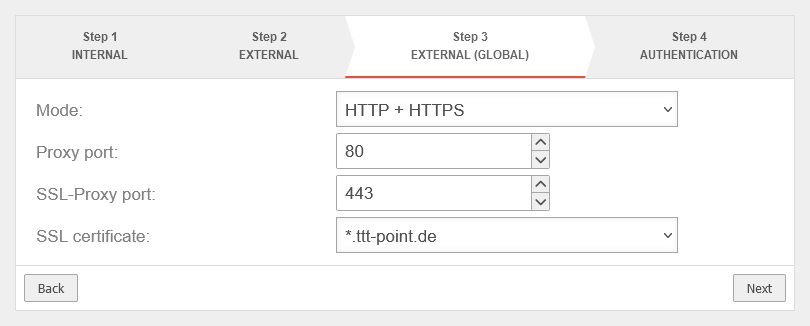 | |
| Proxy-Port: | 80 | Port for the proxy of the corresponding server | |
| SSL-Proxy Port: | 443 | Port for the SSL proxy of the corresponding server | |
| SSL certificate: | The certificate that was selected in the step Preparations is selected here. | ||
Step 4 - Authentication | |||
| Forward authentication: | The proxy should not perform authentication The string can include URL escapes (i.e. %20 for spaces). This also means % must be written as %%. |
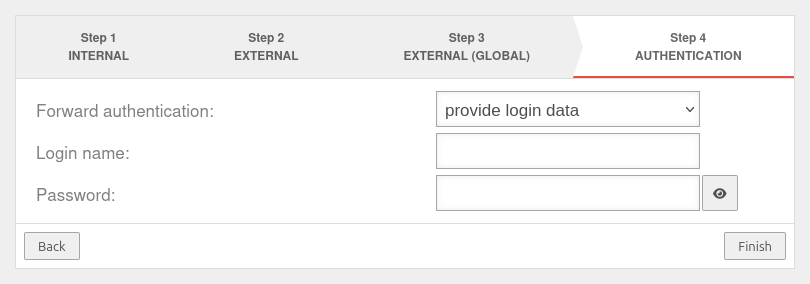 | |
| Forwards the client's authentication headers to the remote station. Login data received from the UTM is sent to the reverse proxy. Authentication is not required for this option. | |||
| Proxy and authentication headers are forwarded unchanged. Sends the login data received from the client to the reverse proxy. Both proxy and WWW authorisation headers are forwarded to the remote peer without modification. | |||
| Login name | |||
| Password | |||
Server groups and Sites
| |||
| notempty New as of: 14.1.1 |
UTMuser@firewall.name.fqdnApplication 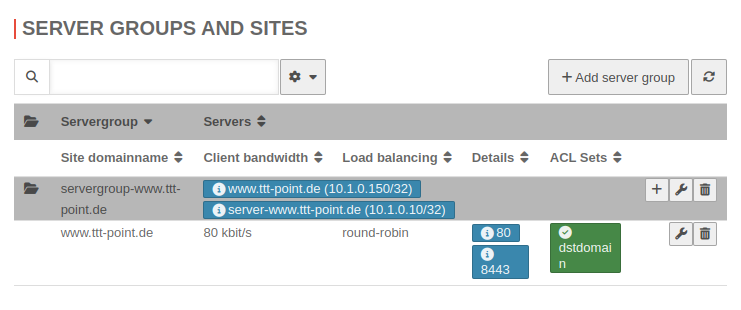 Automatically created server group Automatically created server group
| ||
Add server group | |||
The arrangement in server groups makes it possible to display different relationships in the reverse Proxy:
| |||
| Adds a new server group. The wizard automatically creates a server group. | |||
| General | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationReverse-Proxy 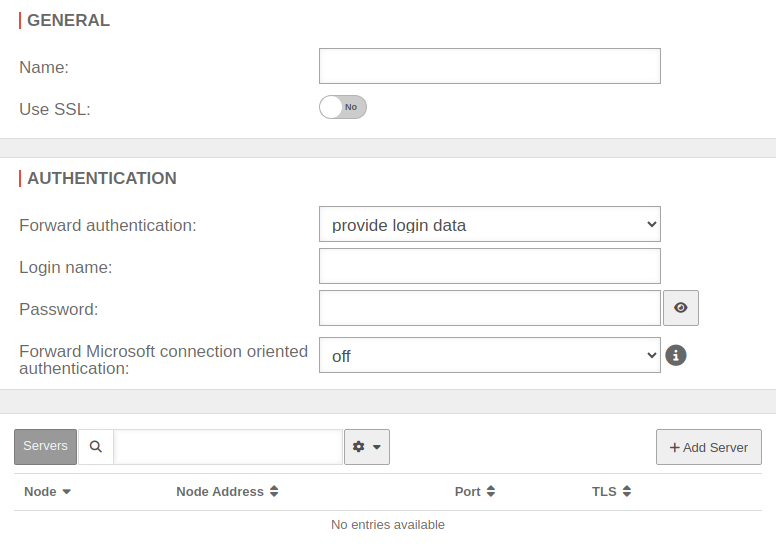
|
|---|---|---|---|
| Name | Name of the server group (not editable) | ||
| Use SSL | No | Determines whether SSL can be used | |
| Authentication When using the ‘’squid‘’ engine, this is done individually for each server. | |||
| Forward authentication: | The proxy should not perform authentication The string can include URL escapes (i.e. %20 for spaces). This also means % must be written as %%. | ||
| Forwards the client's authentication headers to the remote station. Login data received from the UTM is sent to the reverse proxy. Authentication is not required for this option. | |||
| Proxy and authentication headers are forwarded unchanged. Sends the login data received from the client to the reverse proxy. Both proxy and WWW authorisation headers are forwarded to the remote peer without modification. | |||
| Login name: Only for Provide login data |
|||
| Password: Only for Provide login data |
|||
| Forward connection-oriented Microsoft authentication: notempty New as of v12.7.1 |
Enables support for NTLM, Negotiate and Kerberos | ||
| Server | |||
| Mittels dieser Schaltfläche lässt sich ein neuer Server hinzufügen | UTMuser@firewall.name.fqdnApplicationReverse-Proxy 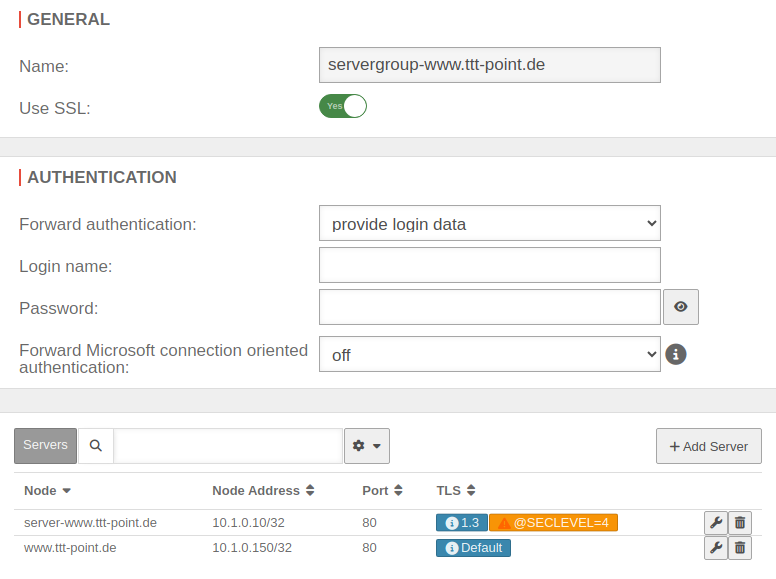 Example with different TLS versions and cipher suites using the nginx engine Example with different TLS versions and cipher suites using the nginx engine
| ||
| Search field for the servers | |||
| Network | www.ttt-point.de | Name | |
| IP address | 10.1.0.150 | IP address of the webserver | |
| Port | 443 | Port via which the server is to be addressed | |
| TLS | Default @Sec Level=4 | TLS settings for this server | |
| Delete | Deletes the server from the reverse proxy server group | ||
| Edit | Der Server aus der Servergruppe kann darüber bearbeitet werden | ||
Add server | |||
| General | |||
| Network | Name | UTMuser@firewall.name.fqdnApplicationReverse-ProxyAdd server group 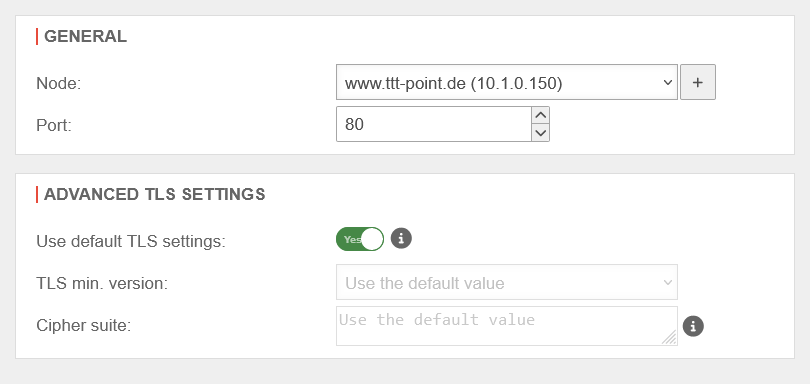
| |
| Opens the dialogue for adding a network object | |||
| Port | 80 | Port via which the server is to be addressed | |
Advanced settings notempty These TLS settings apply to the connection between this appliance and the (local) server. For TLS settings between the clients and this appliance, the settings in the Area Reverse-Proxy dialog apply. | |||
| Use default TLS settings: | Yes | Allows connections with TLS 1.2 or 1.3 only | |
| Minimal TLS version: | The outdated TLS versions 1.1 and 1.0 can be selected. | ||
| Cipher-Suite: | Standardwert verwenden | Note that to directly use a OpenSSL security level, the notation @SECLEVEL=N can be used in the cipher string, where N represents the selected level from 0 to 5.
| |
Sites
| |||
| If a server group already exists, a site can be added using the button. notempty New as of v14.1.1 If there are invalid configurations, these are provided with a warning (). When hovering over this warning, a short description of the problem is also shown.
|
UTMuser@firewall.name.fqdnApplicationReverse-Proxy  Sites overview when using the nginx engine Sites overview when using the nginx engine
| ||
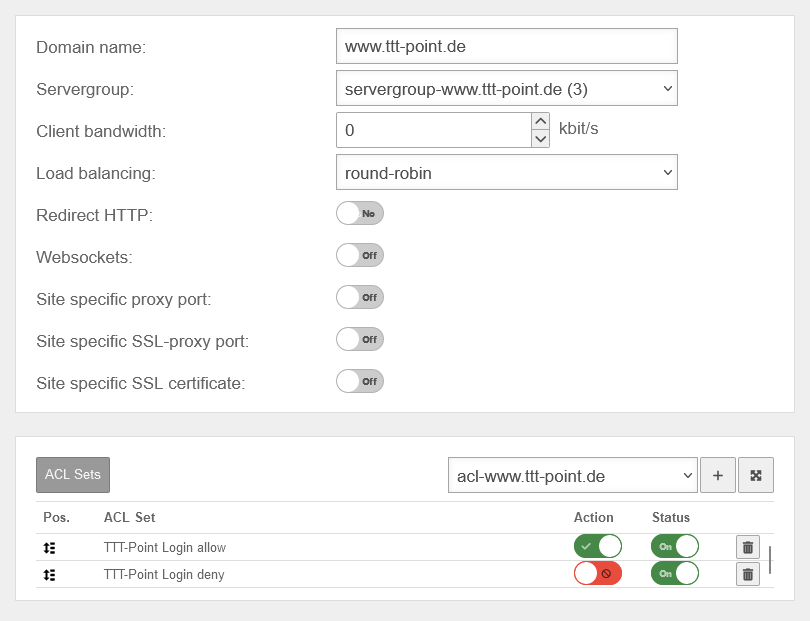
Site hinzufügen | |||
| Domain name: | www.ttt-point.de | This is where you enter how the server behind the UTM is addressed. | UTMuser@firewall.name.fqdnApplicationReverse-Proxy 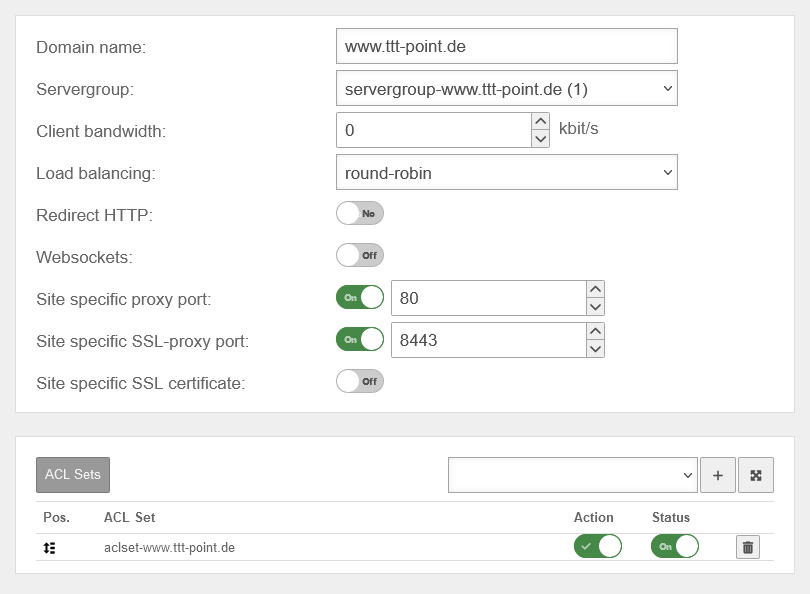 Edit sites when using the nginx engine Edit sites when using the nginx engine
|
| Server group: | The associated server group is selected here | ||
| Client bandwidth: | 0 kbits/s | Maximum bandwidth that should be available to a client | |
| Load distribution: | The connections are processed one after the other. | ||
| A user's connections (hash on the user name) are always routed to the same server. | |||
| Connections from the same source (IP address) are always routed to the same server. | |||
| Redirect HTTP: Only with mode: |
No | When activated, HTTP requests are redirected to the HTTPS port | |
| Websockets: | off | Activates Websockets connections for the site | |
| Site-specific proxy port: | On 80 Default: off |
Enables a specific port for HTTP connections in this site | |
| Site-specific SSL proxy port: | On 8443 Default: off |
Enables a specific port for HTTP connections in this site | |
| Site-specific SSL certificate: | off | A site-specific server certificate can be selected | |
| ACL Sets | Selection of an ACL set to be added | ||
| Add | Add selected ACL set | ||
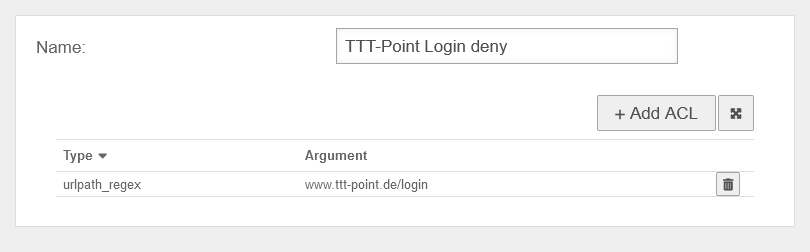
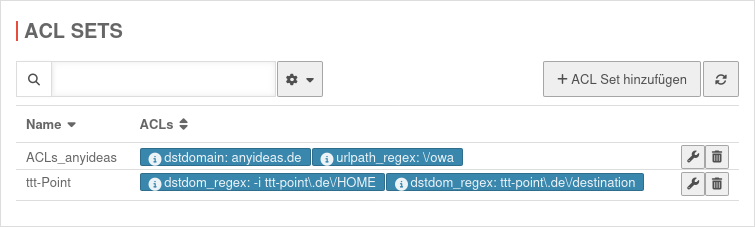
Sites benötigen wenigstens ein ACL Set, in dem ein dstdomain oder dstdom_regex ACL vorhanden ist.
Dieses ACL Set muss der Site mit der Aktion zulassen zugeordnet sein und den Status Ein aktiviert haben. | |||
| Pos. | The order of the ACL sets can be customised using drag and drop. | ||
| ACL Set | aclset-www.ttt-point.de | Name | |
| Acion | Configuration of whether the ACL set should be permitted or prohibited | ||
| Status | On | Activation or deactivation of the configuration for the ACL set | |
| Delete | Deletes the entry for the ACL set | ||
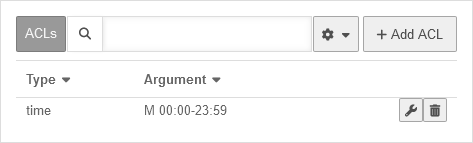
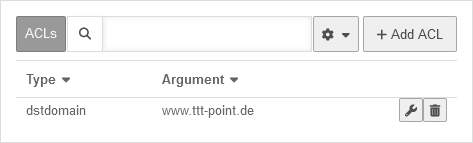
Combination example | |||
| By combining different ACL sets with corresponding authorisations, it is possible, for example, to ensure that the login page of a server can only be accessed from a specific (e.g. your own) public IP address. | |||
UTMuser@firewall.name.fqdnApplicationReverse-Proxy 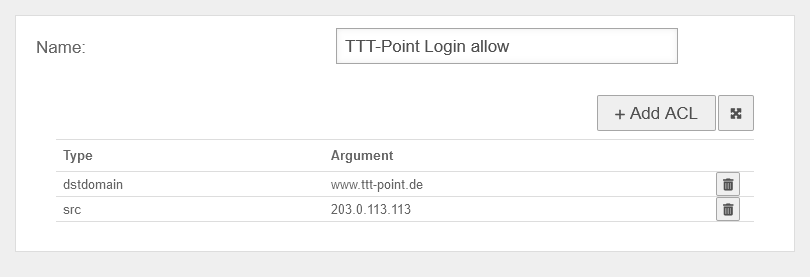 Combination example step 1 Firstly, an ACL is required for this, which contains the dstdomain and the public IP address as src. | |||
ACL Sets
Options
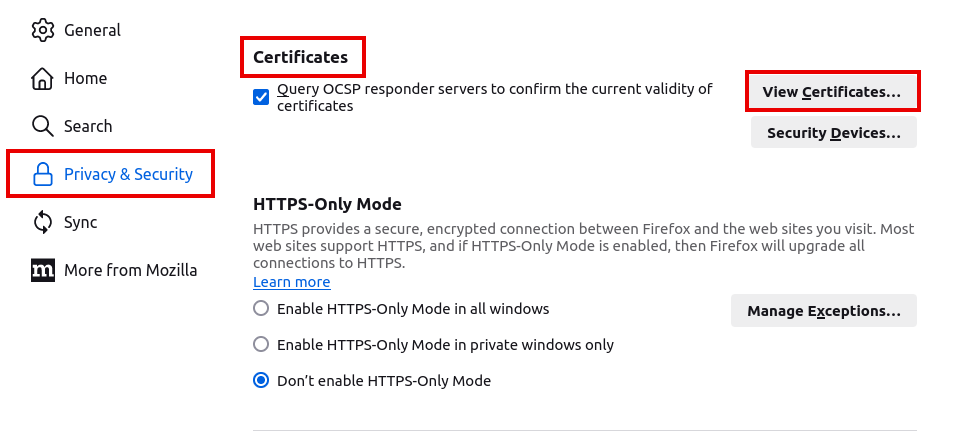
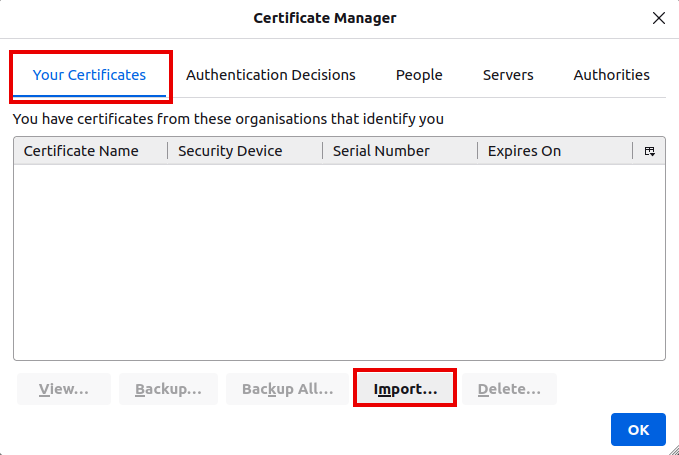
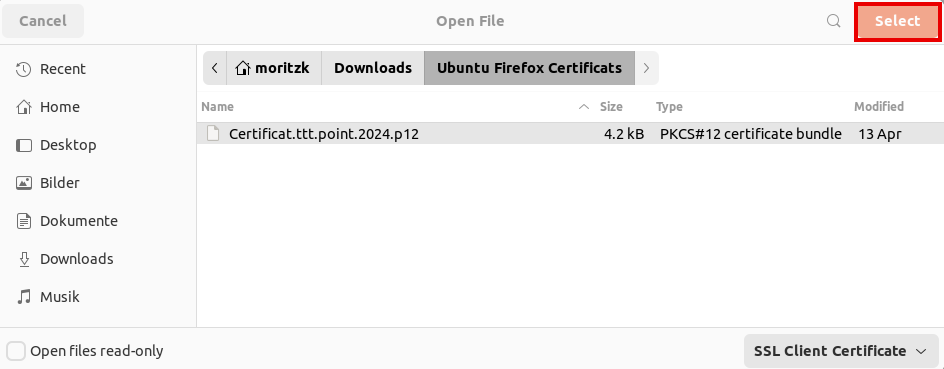
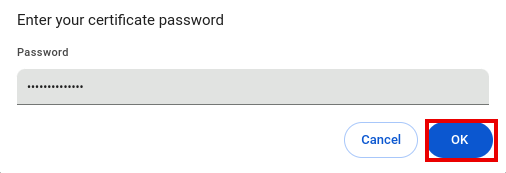
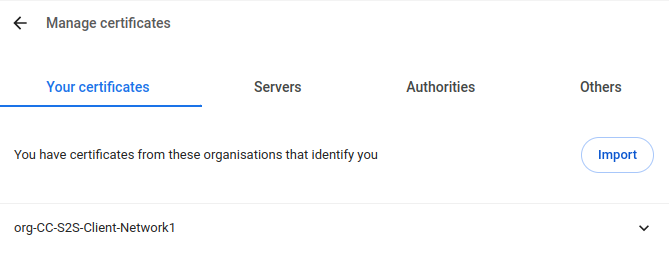
Import of personal certificates
notemptyIn order for the Enable certificate-based authentication function to be used correctly, the personal certificate must be available in the browser used.