Configuration of an IPSec connection with EAP-MSCHAPv2
Last adaptation to the version: 12.6.0
New:
- Updated to Redesign of the webinterface
This article refers to a Beta version
Preparations
User rights and settings
Group with IPSec EAP authorization | |||
| Active | Permissions | Description | UTMuser@firewall.name.fqdnAuthenticationUser 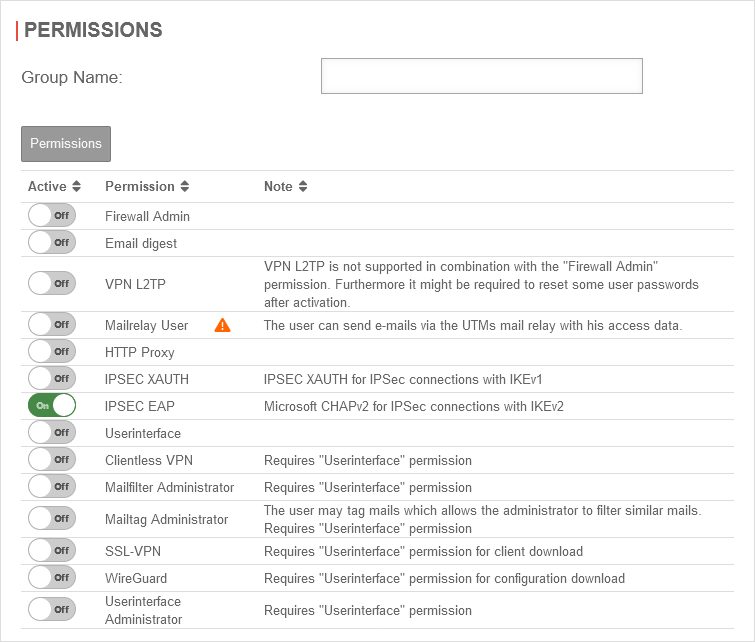 In this new group, IPSec EAP still needs to be enabled. In this new group, IPSec EAP still needs to be enabled.
|
|---|---|---|---|
| On | IPSec EAP | Enables Microsoft CHAPv2 for IPSec connections with IKEv2 | |
Edit group
or
Further configuration options in the wiki article on User Groups | |||
User configuration | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnAuthenticationUser 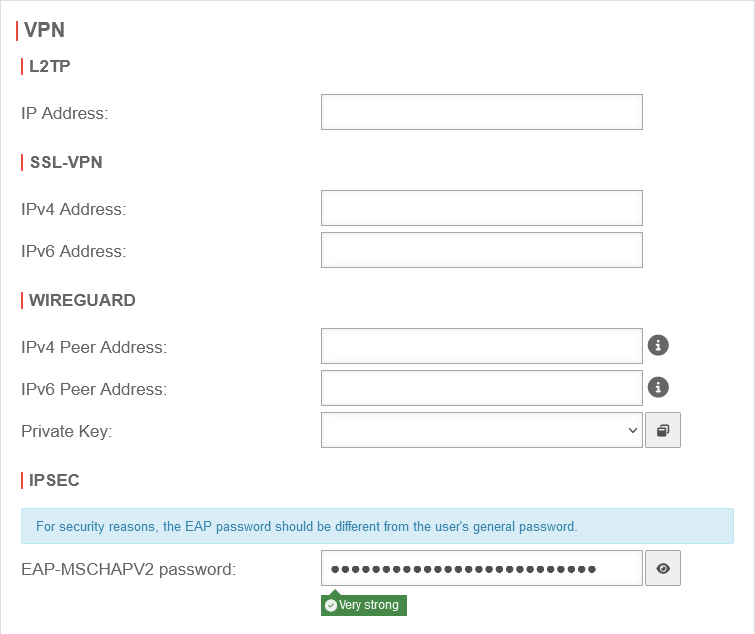
|
| EAP MSCHAPv2 password: | **************** | An appropriate password is entered. | |
Edit user
or
The user must be a member of the newly configured group with the IPSEC EAP permission
Enter MSCHAPv2 password
Further configuration options in the wiki article on User management | |||
Configure IPSec
Preparations
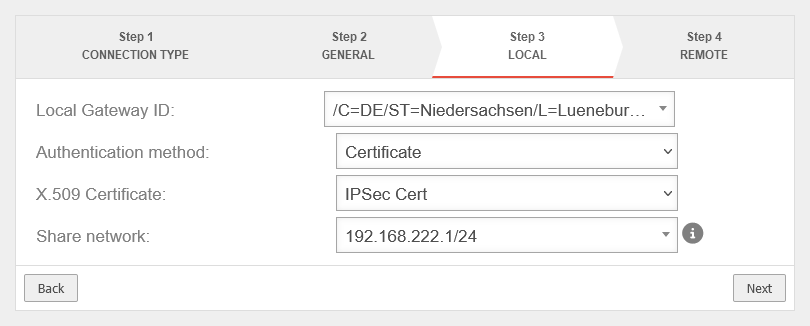
Create CA and server certificate
A corresponding CA and server certificate is required for an IPSec connection. If these do not yet exist, they must be newly created.
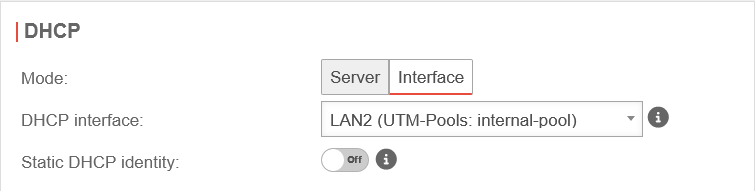
Set up DHCP
If desired, clients can receive IP addresses from a local network via DHCP.
To do this, a few general settings must be made.
Preparations
An IP address range for the network of the selected interface must be available on the DHCP server.
On the UTM, this is configured under Area DHCP Pools.
Further setup instructions in the Wiki article on DHCP.
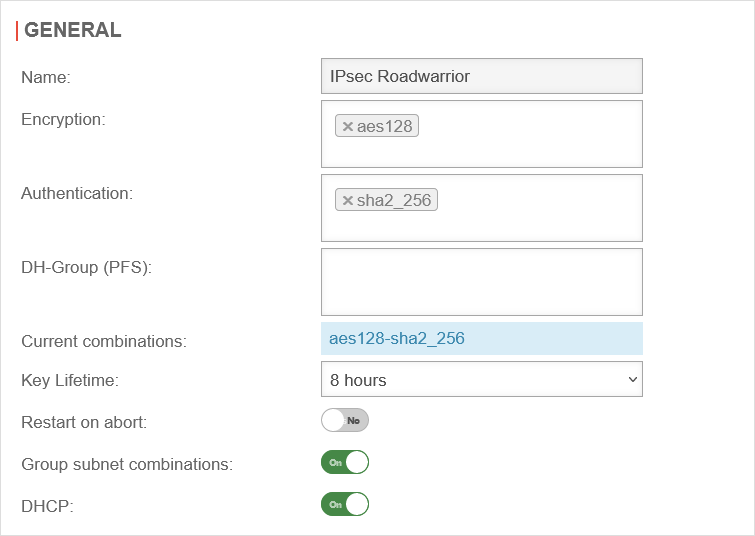
IPSec DHCP settings
Menu Area DHCP
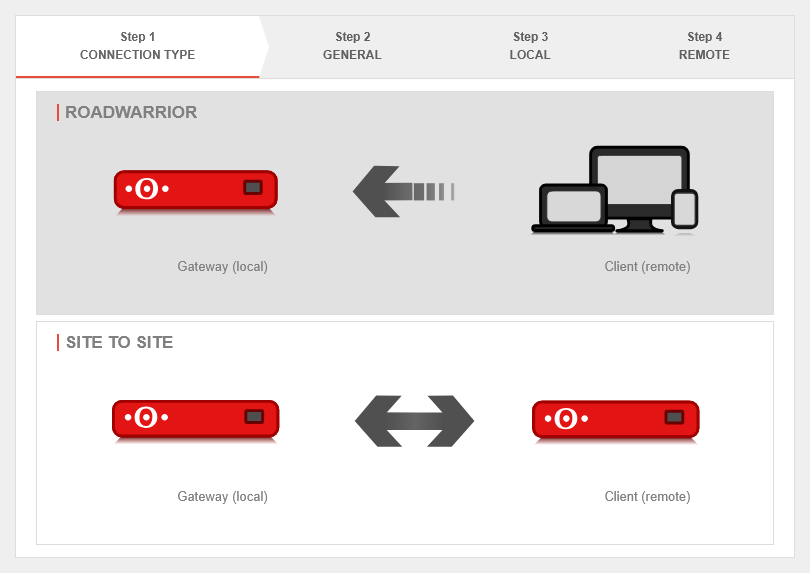
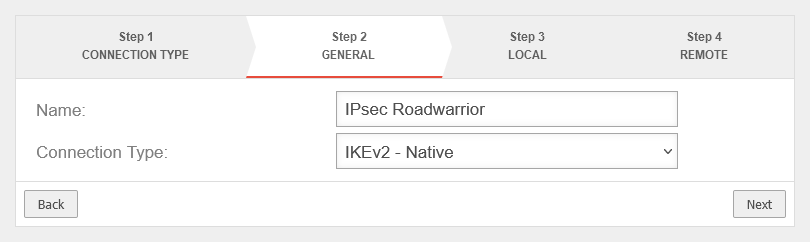
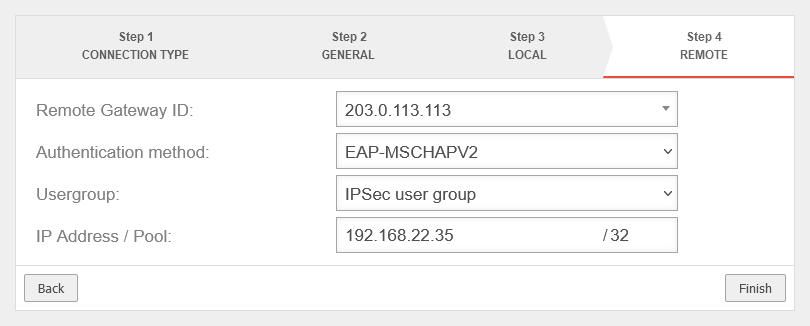
Create IPSec Roadwarrior connection
Add connection using the setup wizard at: Area Connections button