Last adaptation to the version: 14.0.3
Introduction
A roadwarrior connection links individual hosts to the local network.
This allows, for example, a field worker to connect to the headquarters network.
SSL-VPN uses the TLS/SSL standard to encrypt the connection.
There is a separate article for creating certificates on the UTM: Certificates
Preparations
These certificates can also be created during setup if necessary.
The BSI recommends—as of January 2025—key lengths of 3000 bits or more and SHA256
BSI – Technical Guideline – Cryptographic Methods: Recommendations and Key Lengths BSI TR-02102-1 | Chapter 2.3: RSA encryption
The default setting of the UTM for new certificates is RSA encryption with 3072 bits and SHA256 as the hash algorithm
Internal hostname resolution in SSL-VPN
If servers in the SSL-VPN are to be accessible to Roadwarrior under their host name, the following settings are required:
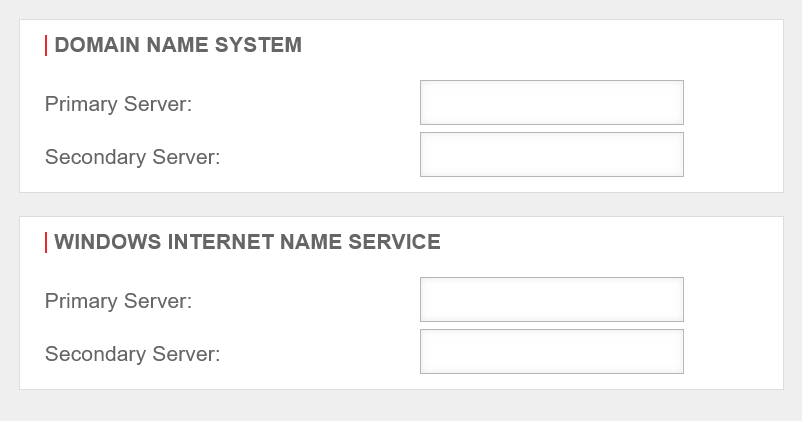
Push DNS/WINS
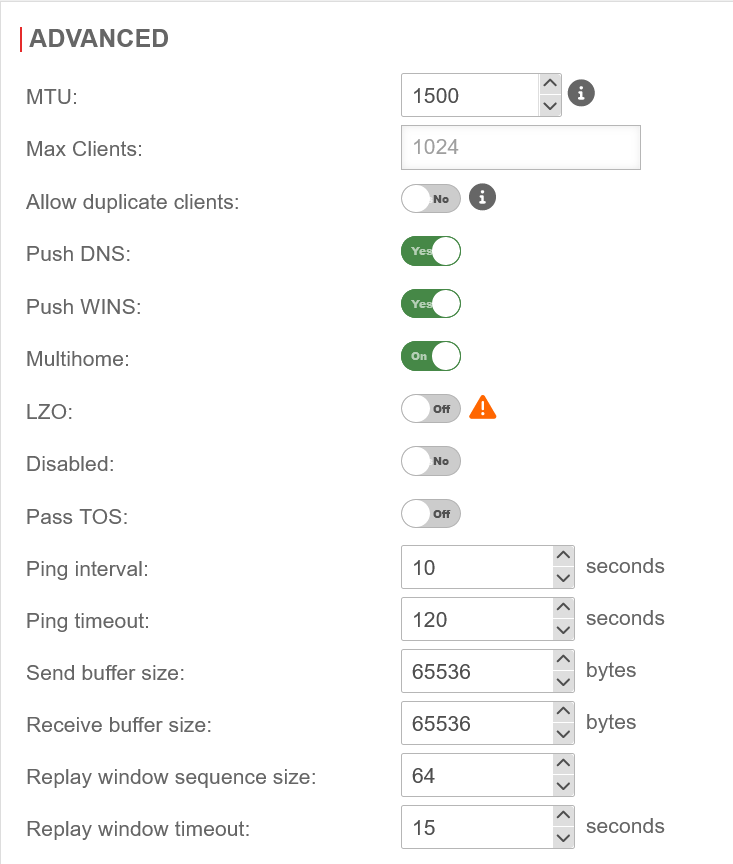
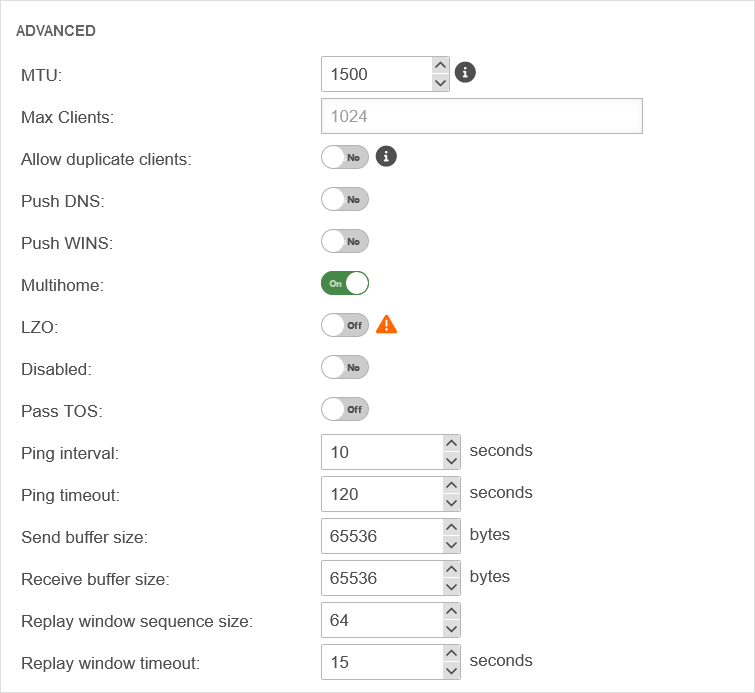
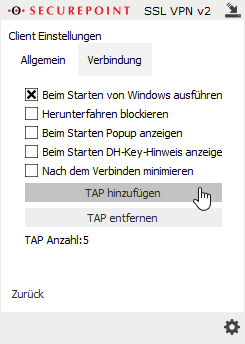
In order for DNS/WINS to be transmitted, the configured VPN connection must be edited and enabled in the Advanced tab.
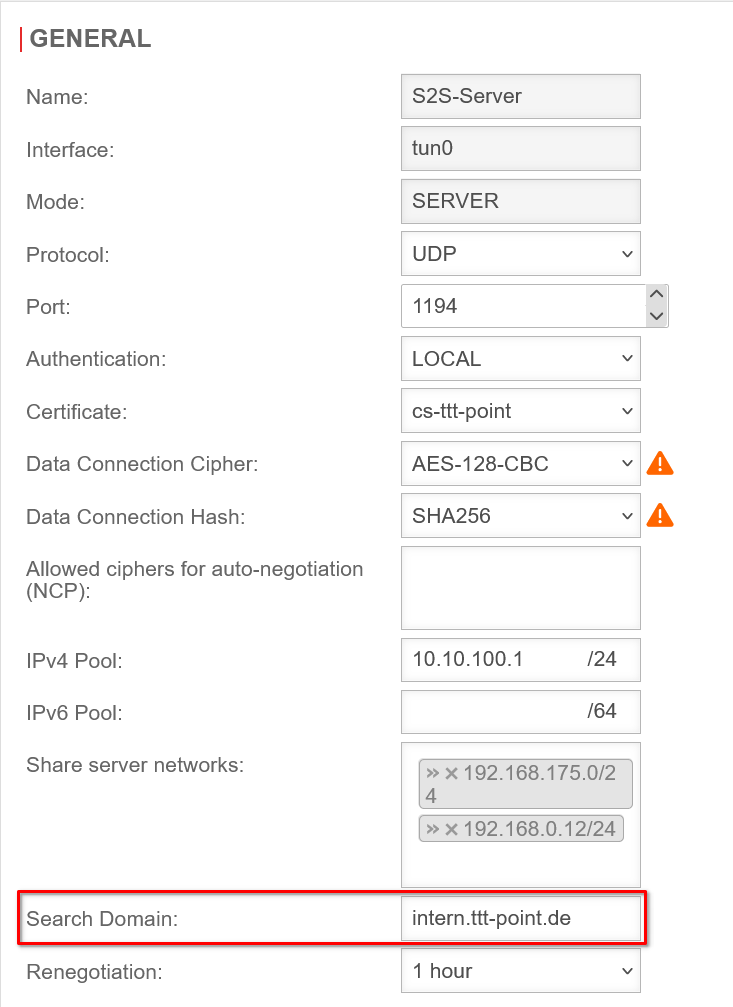
Search Domain
Block Outside DNS
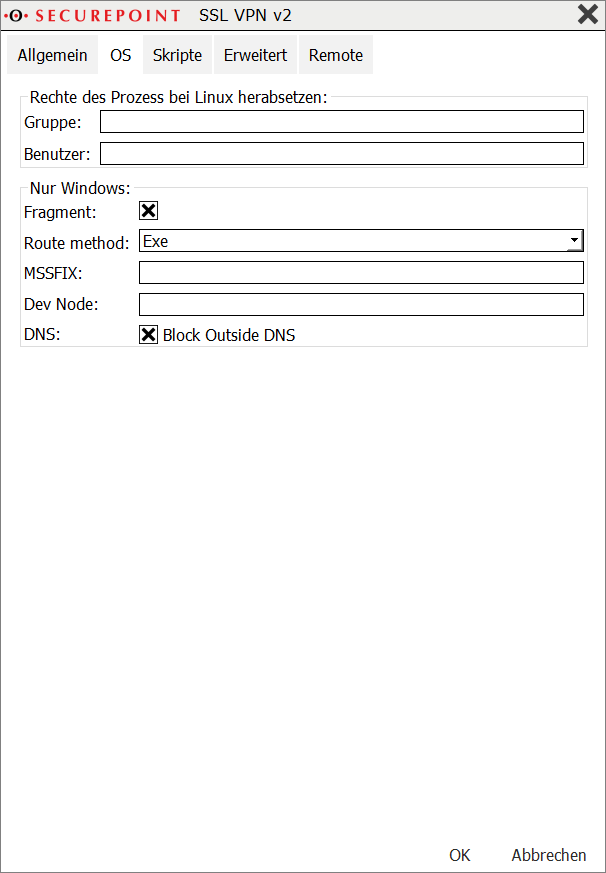
For some Windows 10 clients, it may be necessary to set the "block-outside-dns" option in the configuration of the SSL-VPN client:
Right click on the desired connection in the Securepoint SSL-VPN Client, menu Settings Advanced button tab OS Entry DNS Block Outside DNS
Roadwarrior configuration
Setup Wizard
After the login on the firewall's administration interface (by default: https://192.168.175.1:11115), the setup wizard can be called up with button .
Step 1 |
UTMuser@firewall.name.fqdnVPNSSL-VPN 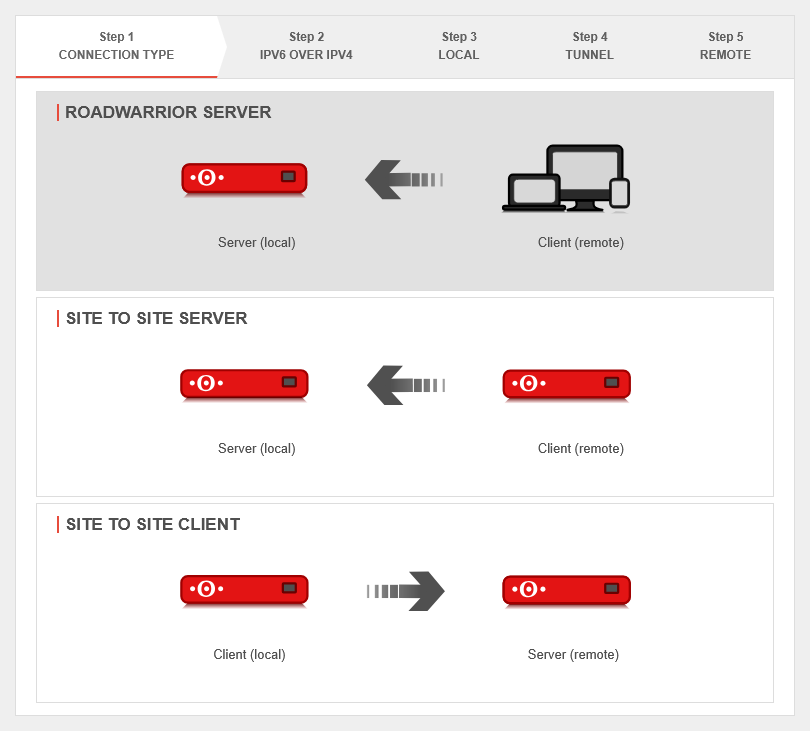 Setup step 1 Setup step 1
| ||||||||||||||||||
| In installation step 1, the connection type is selected. The following connections are available.
For the configuration of the Roadwarrior Server this one is selected. | |||||||||||||||||||
Step 2 |
 | ||||||||||||||||||
| If IPv6 is to be used in the source and destination network, this must be enabled here. | |||||||||||||||||||
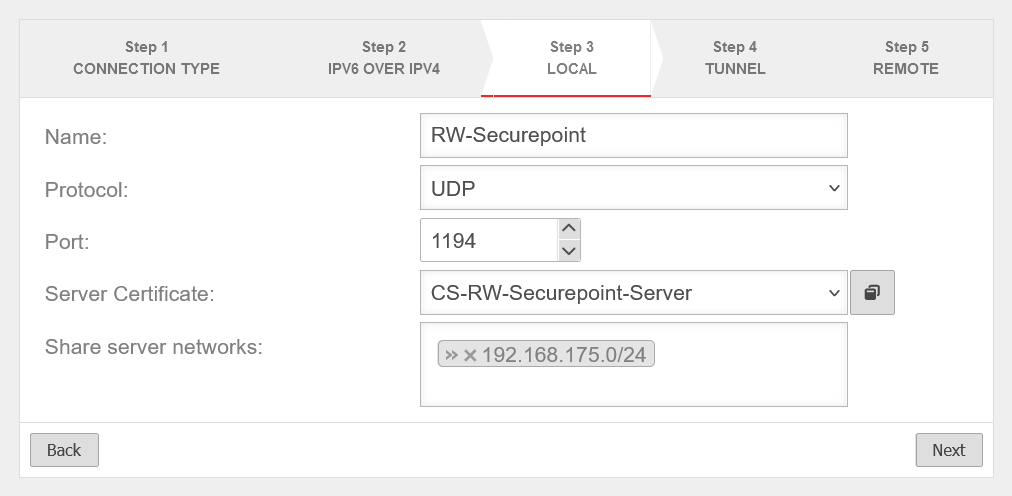
Step 3Local settings for the Roadwarrior server can be made in step 3. | |||||||||||||||||||
|
 | ||||||||||||||||||
Step 4 |
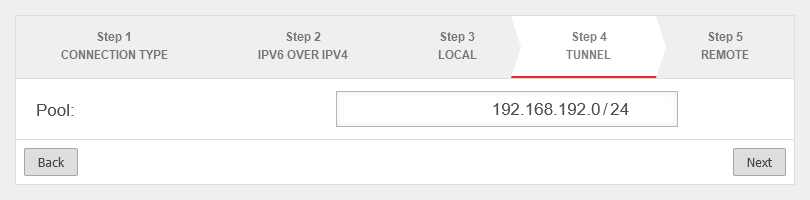 | ||||||||||||||||||
| In installation step 4, the transfer network for the Roadwarrior is entered. The transfer network can be freely selected, but must be otherwise unused on the UTM. error in the description of the order corrected error corrected, ’'.254 is occupied by the virtual DHCP server
| |||||||||||||||||||
Step 5 |
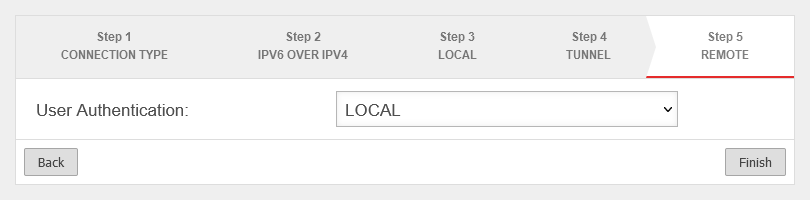 | ||||||||||||||||||
| User authentication is selected in the last step. The setup wizard can then be completed.
| |||||||||||||||||||
Completion |
UTMuser@firewall.name.fqdnVPN 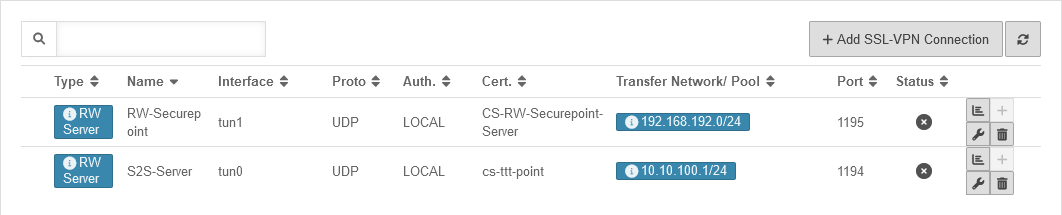 Setup completion Setup completion
| ||||||||||||||||||
| In the SSL-VPN overview all configured connections are displayed. In order for the connection to become active, the SSL-VPN service must be restarted: | |||||||||||||||||||
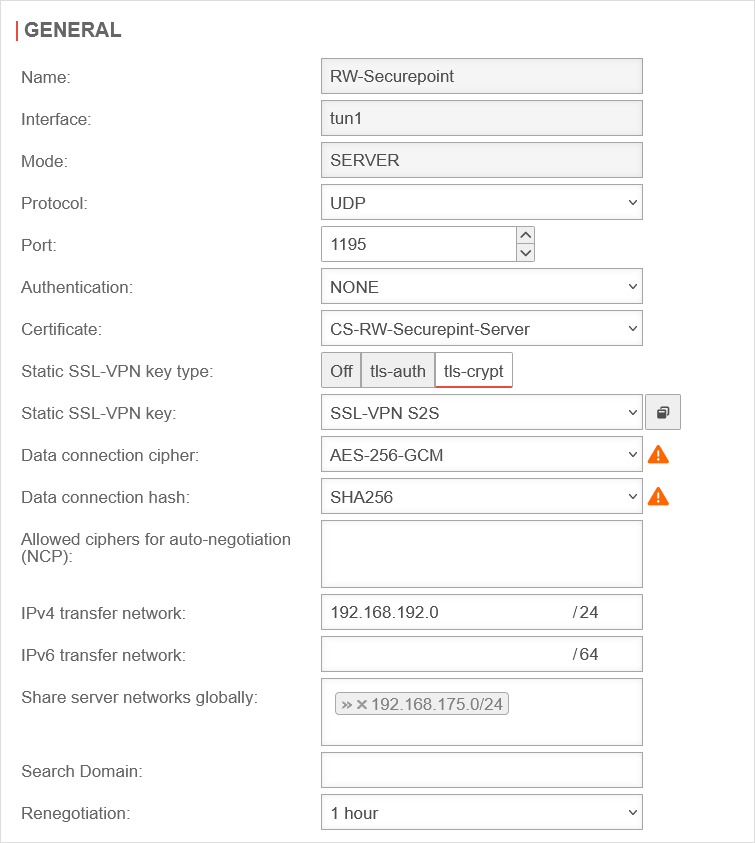
Edit connection
Policy
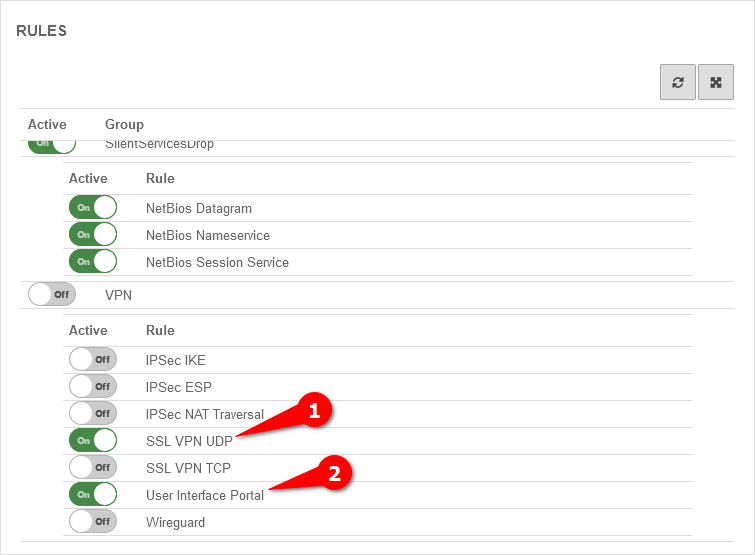
Implied rules
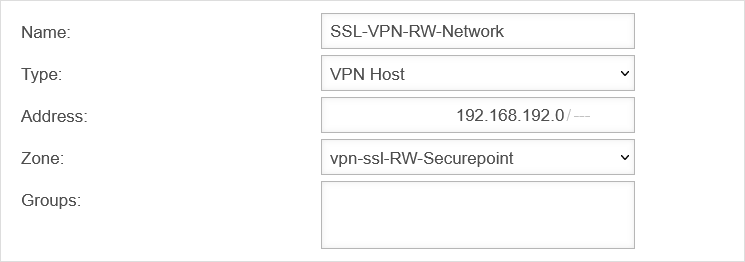
Network objects
A tun interface was created when the connection was set up. It automatically receives the first IP address from the transfer network configured in the connection and a zone "vpn-ssl-<servername>".
The Roadwarrior clients will receive an IP address from this network and will be located in this zone.
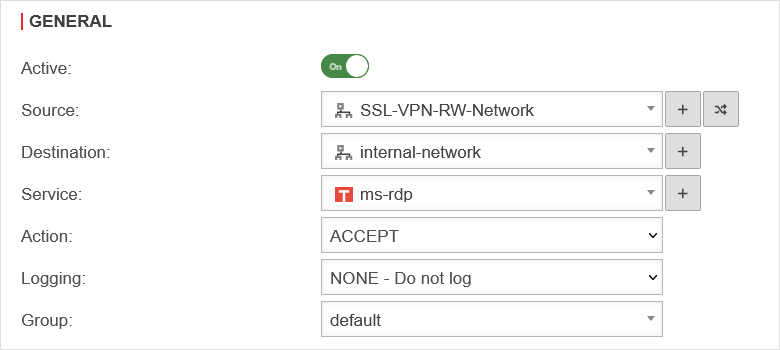
To grant the roadwarriors access to your own network, a network object must be created.
Packetfilter rule
Creating users and groups
Group
| Permissions | UTMuser@firewall.name.fqdnAuthenticationUser 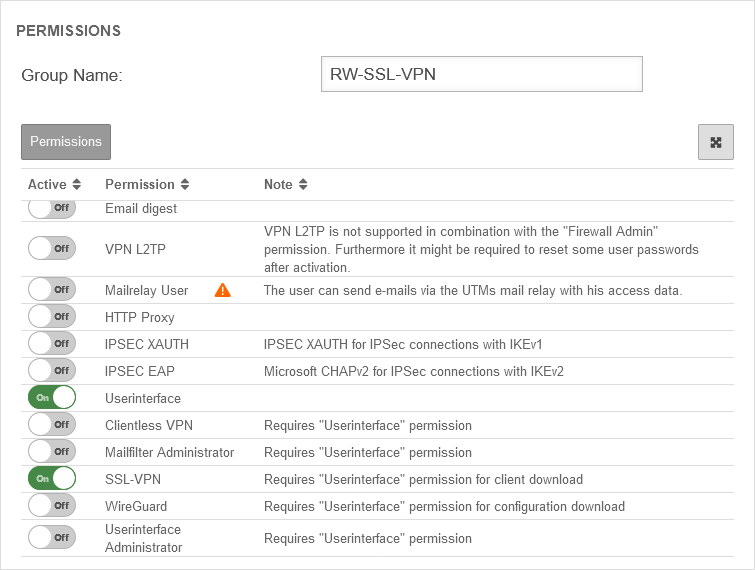
| |
| Under Area Group button . The following authorisations must be given:
| ||
| SSL-VPN | |||
| Client downloadable in the user interface: | Yes | Per default over the port 443, so e.g. under https://192.168.75.1 accessible | 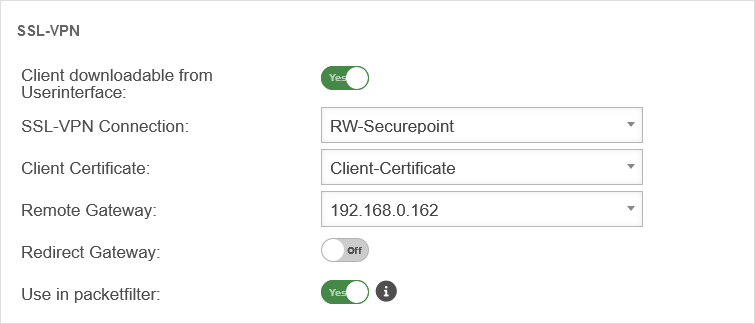 |
| SSL-VPN connection: | RW-Securepoint | Select just created connection | |
| Client-Certificate: | Client-Certificate | Selection of the client certificate described in Step 3 of the setup wizard.
| |
| Remote Gateway: | 192.0.2.192 | The remote gateway is the address of the external interface. This address must be accessible external. | |
| Redirect Gateway: | Off | When activated, requests from roadwarrior clients to the Internet or networks outside the VPN are also redirected via the local gateway. As a result, these connections also benefit from the protection of the UTM. | |
| Available in the port filter: | Yes | Enables Identity-Based Firewall (IBF) for SSL-VPN | |
User
| General | |||
| Groups: | RW-SSL-VPN | The user must be assigned the previously created group. | |
| SSL-VPN | UTMuser@firewall.name.fqdnAuthenticationUser 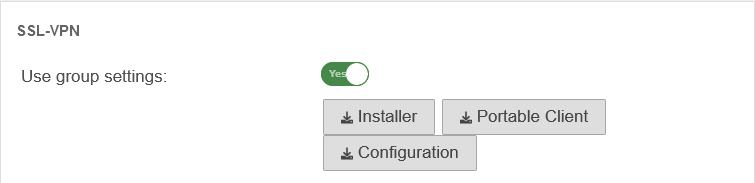 SSL-VPN settings for the users SSL-VPN settings for the users
| ||
| Use settings from the group: | On | If settings have already been made for the group, these can be adopted here instead of individual values. | |
| If the information has been saved, the corresponding files can already be downloaded by the administrator at this point. | |||
| Further information on users can be found in the article on User Management. | |||
The SSL-VPN Client
Downloading the SSL-VPN client in the user interface
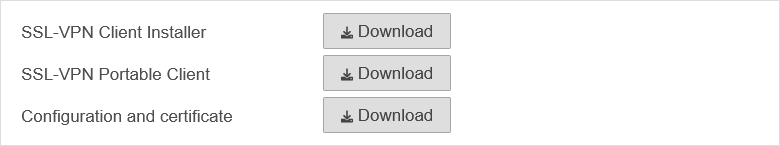
For users who want to connect to the UTM via SSL-VPN, the appliance provides a preconfigured SSL-VPN client:
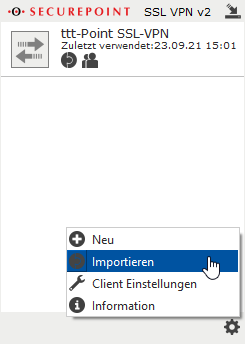
- Access the download via the menu item .
- This client contains the configuration files and all required certificates.
- Login to the user interface of the UTM by default via port 443, e.g. under https://192.168.75.1
- The user interface is accessed via the internal interface of the Securepoint appliance.
The client is offered as:
- SSL-VPN Client Installer
- Required processor architecture: x86 / x64
- SSL-VPN Portable Client
- The portable version can be copied to a USB stick, for example, and can thus be run on other computers.
- Required processor architecture: x86 / x64
- Configuration and certificate
- For use in other SSL-VPN clients
- a configuration file
- the CA and client certificates
- and a driver for the virtual TAP network interface.
- To install the virtual TAP interface, the user needs administrator rights on the machine being used.
notempty
Installation: Hints for the installation can be found on our wiki page for the VPN client.
Establish SSL-VPN connection as client
Double-click on the lock icon in the taskbar to open the SSL-VPN client.
Start the connection by clicking ![]()
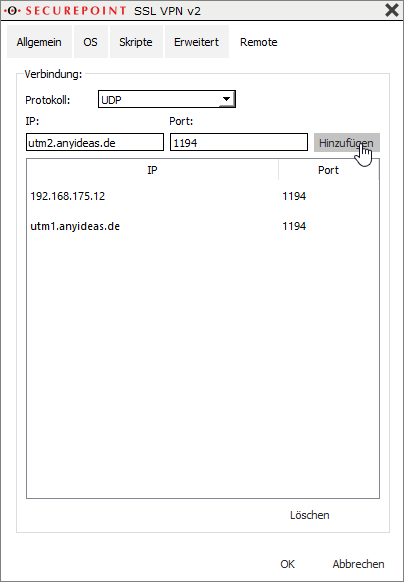
Multiple VPN servers as targets for one connection
In the settings of a connection under Advanced/Remote additional VPN servers with IP or hostname can be stored as destination.
Use multiple VPN profiles
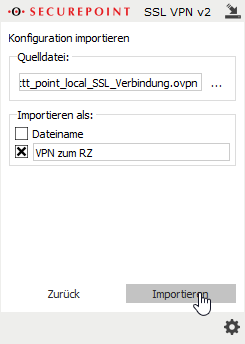
Multiple VPN profiles can be imported and used at the same time.
Notes
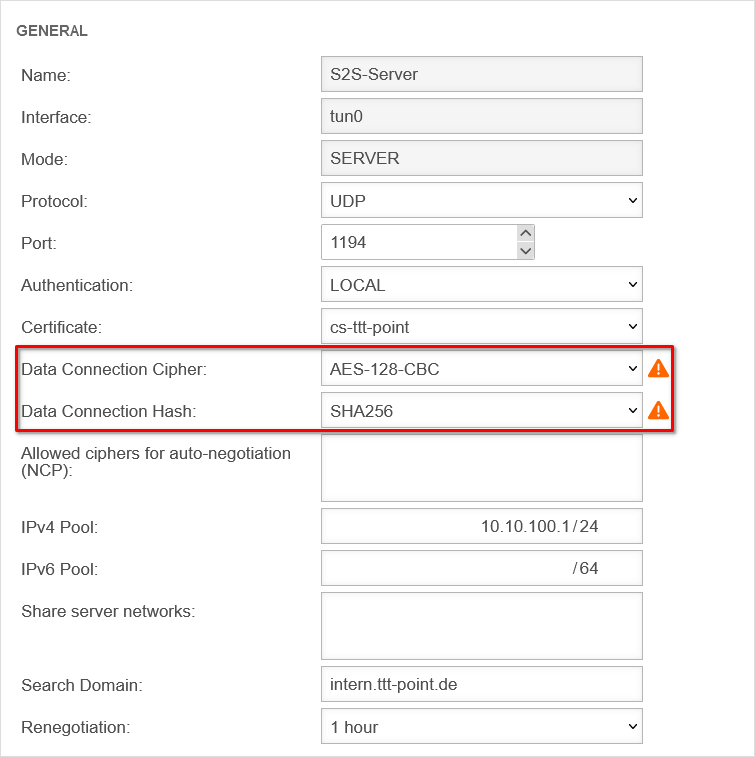
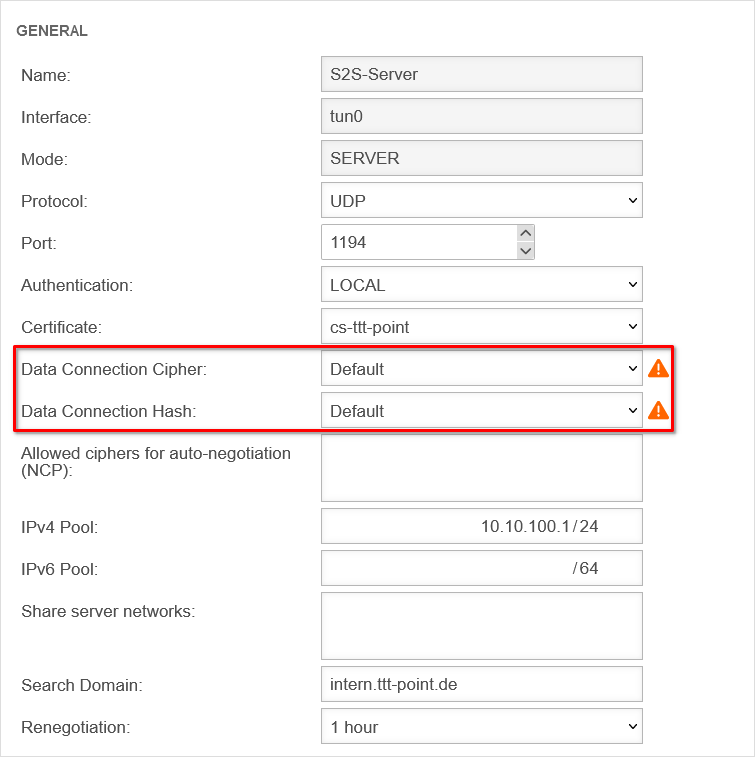
Encryption
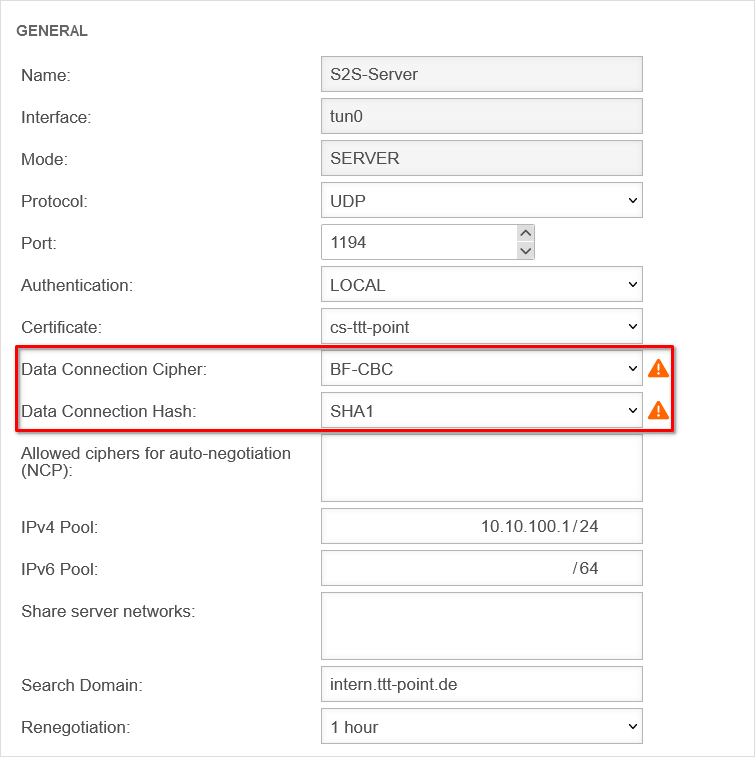
By default, an AES128-CBC method is used. The encryption method can be customized in the server or/and client profile.
notempty
If the client uses this cipher and is not able to handle NCP, with which the cipher is negotiated automatically, no connection is established. The cipher must be adjusted.
It is strongly recommended to stop using the BF-CBC cipher because it is considered not secure.
If the BF-CBC cipher is to be used anyway, it can be selected explicitly.
Adjustment on the UTM with the button of the respective connection in the General tab in the Cipher for data connection field.
notempty
Hash method
By default, a SHA256 hash method is used. The hash method can be customized in the server or/and client profile.
QoS
For the VPN connection, the TOS fields for automatic QoS can be set in the packets. This setting can be enabled in the VPN connection settings under "Advanced".
Note on upstream routers/modems
There are always problems with the stability of the connection if a router/modem in front of the appliance also has an active firewall. Please do not use any firewall functionality on these devices.
IPv6 for incoming connections
In the settings of the roadwarrior server , the protocol or for IPv6 can be activated under General / Protocol.
Use multiple IP addresses differently
For this purpose, the reverse proxy rule must explicitly specify that the external-interface of the specific IP should be used as the destination. For the other use, the traffic is redirected using DestNAT, i.e. the traffic arrives on port 443, but is then redirected to another port (e.g. 1194 for VPN) using a packet filter rule.
Troubleshooting
For advice on troubleshooting SSL-VPN, see the Troubleshooting Guide SSL-VPN (pdf document).
Connection Rate Limit
Throttling of access from certain source IPs to recurring ports
notempty
The function can initially only be configured via the CLI
SSL-VPN accesses can be protected against aggressive scans or login attempts, for example.
From v12.6.2, the UTM can limit the number of TCP and/or UDP connections from an external IP address to one port.
The following conditions apply:
- Only incoming connections for which a default route exists are monitored
- The connections from an IP address to a port of the UTM are counted within one minute
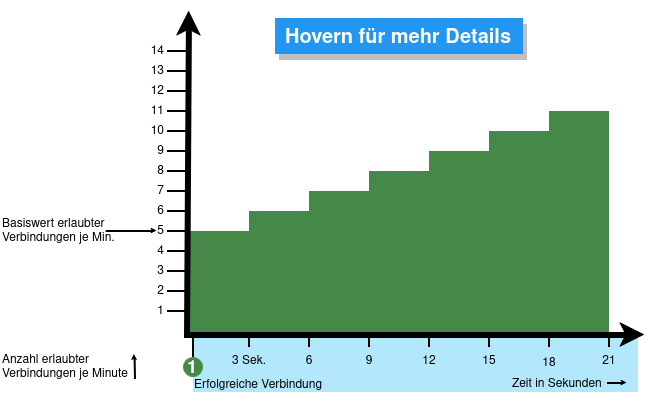
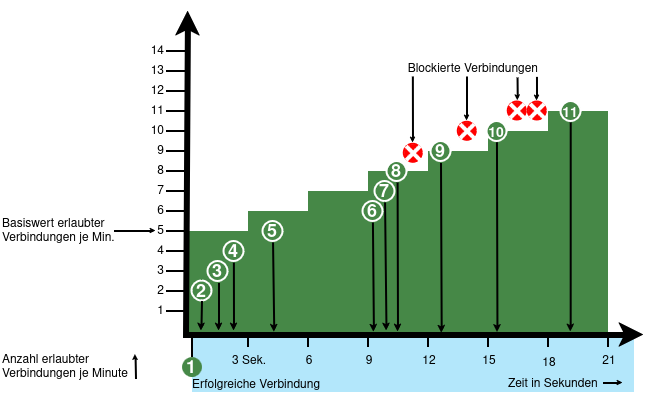
- When activated, 5 connections / connection attempts per minute are permitted.
The connections are then limited:- The additionally permitted connections are distributed evenly within 60 seconds of the first connection.
- With a CONNECTION_RATE_LIMIT value of 20, an additional connection is added every 3 seconds.
- 10 seconds after the first login, 3 further connections could be established (each from the same IP address to the same destination port)
- Blocking an IP address only affects access to the port that has been used too often.
Other ports can still be accessed.
- The function is activated by default for new installations on 20 UDP connections / minute on all ports
- For Updates the function must be manually activated
| extc-Variable | Default | Description |
|---|---|---|
| CONNECTION_RATE_LIMIT_TCP | 0 | Number of permitted TCP connections of an IP address per port 0 = Function deactivated, no blocking is performed |
| CONNECTION_RATE_LIMIT_TCP_PORTS | Ports to be monitored. Empty by default=all ports would be monitored (if activated). Individual ports are separated by spaces: [ 1194 1195 ] | |
| CONNECTION_RATE_LIMIT_UDP | 20 / 0 Default setting for new installations from v12.6.2: 20 For update installations the value is 0, so the function is deactivated. |
Number of permitted UDP connections of an IP address per port |
| CONNECTION_RATE_LIMIT_UDP_PORTS | Ports to be monitored. Empty by default=all ports are monitored (only for new installations!). Individual ports are separated by spaces: [ 1194 1195 ] |
Configuration with CLI commands
| CLI command | Function |
|---|---|
| extc value get application securepoint_firewall Alternatively as root user: spcli extc value get application securepoint_firewall | grep RATE |
Lists all variables of the securepoint_firewall application. The variables beginning with CONNECTION_RATE_LIMIT_ are responsible for the connection limit. application |variable |value --------------------+-------------------------------+----- securepoint_firewall |… |… |CONNECTION_RATE_LIMIT_TCP |0 |CONNECTION_RATE_LIMIT_TCP_PORTS| |CONNECTION_RATE_LIMIT_UDP |20 |CONNECTION_RATE_LIMIT_UDP_PORTS| |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 20 system update rule |
Limits the allowed number of TCP connections from a single IP address to a specific port to 20 per minute
A change is made directly by a rule update. The value must not be set to 0 first! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 0 system update rule |
Deactivates the monitoring of TCP connections |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP_PORTS value [ 443 11115 ] system update rule |
Restricts the monitoring of TCP connections to ports 443 and 11115 There must be spaces before and after the square brackets [ ]! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP_PORTS value [ ] system update rule |
There must be spaces before and after the square brackets [ ]! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP value 20 system update rule |
Limits the allowed number of UDP connections from a single IP address to a specific port to 20 per minute Default setting for new installations from v12.6.2: 20 For update installations the value is 0, so the function is deactivated. The value must not be set to 0 first! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP value 0 system update rule |
Deactivates the monitoring of UDP connections |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP_PORTS value [ 1194 1195 ] system update rule |
Restricts the monitoring of UDP connections to ports 1194 and 1195. (Example for 2 created SSL-VPN tunnels). There must be spaces before and after the square brackets [ ]! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP_PORTS value [ ] system update rule |
There must be spaces before and after the square brackets [ ]! |
extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 20 notempty Finally, the CLI command system update rule must be entered so that the values in the rules are applied. |
For example, to allow a maximum of 20 connections per minute per IP address and port. For TCP, monitoring is restricted to ports 443 and 11115. All ports are monitored for UDP connections. |