Configure Azure Apps with OAuth for the Securepoint UMA
Last adaption: 03.2023
New:
- Screenshots and terms updated
This article refers to a Beta version
-
Preliminary note
This article includes descriptions of third-party software and is based on the status at the time this page was created.
Changes to the user interface on the part of the manufacturer are possible at any time and must be taken into account accordingly in the implementation.
All information without warranty.
- Tenant ID
- Client ID
- Client secret
- Launch Azure Active Directory admin center
- Note down/Copy Tenant ID from the Azure Active Directory menu
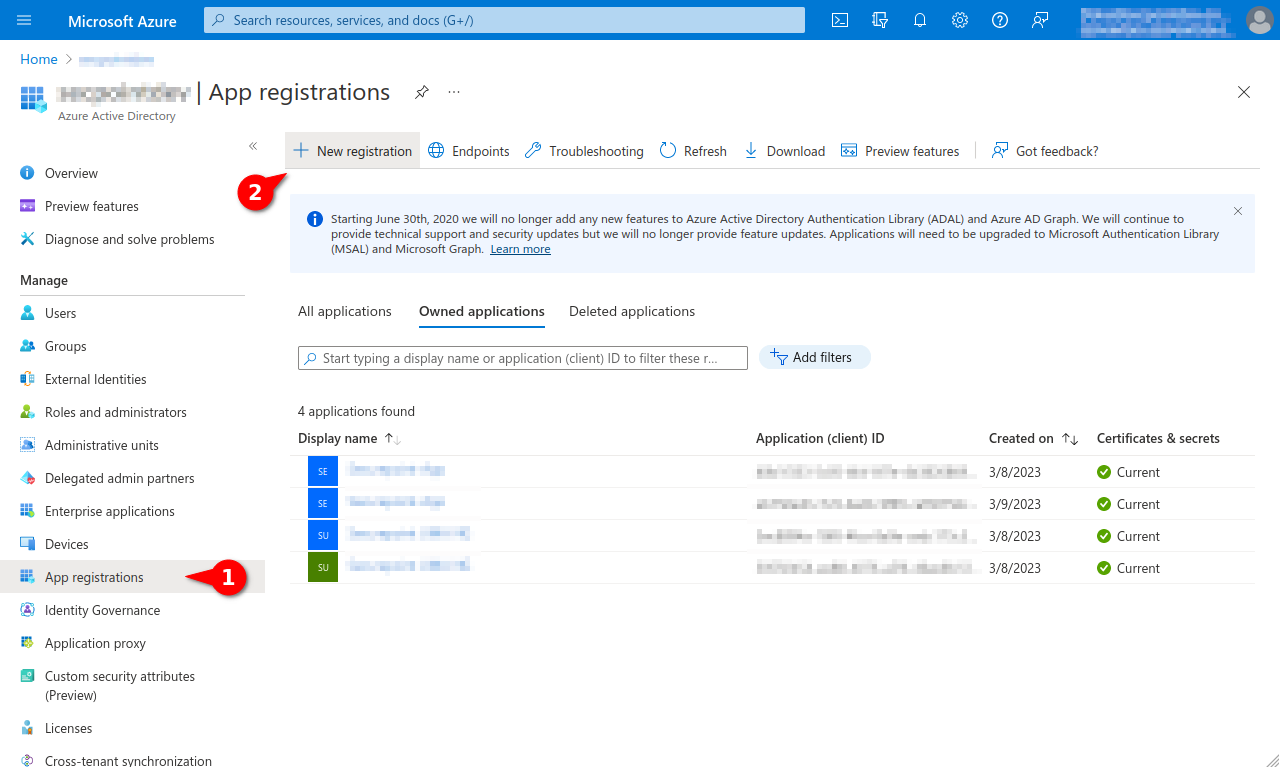
- Register new app under theApp registration menu under the New registration button
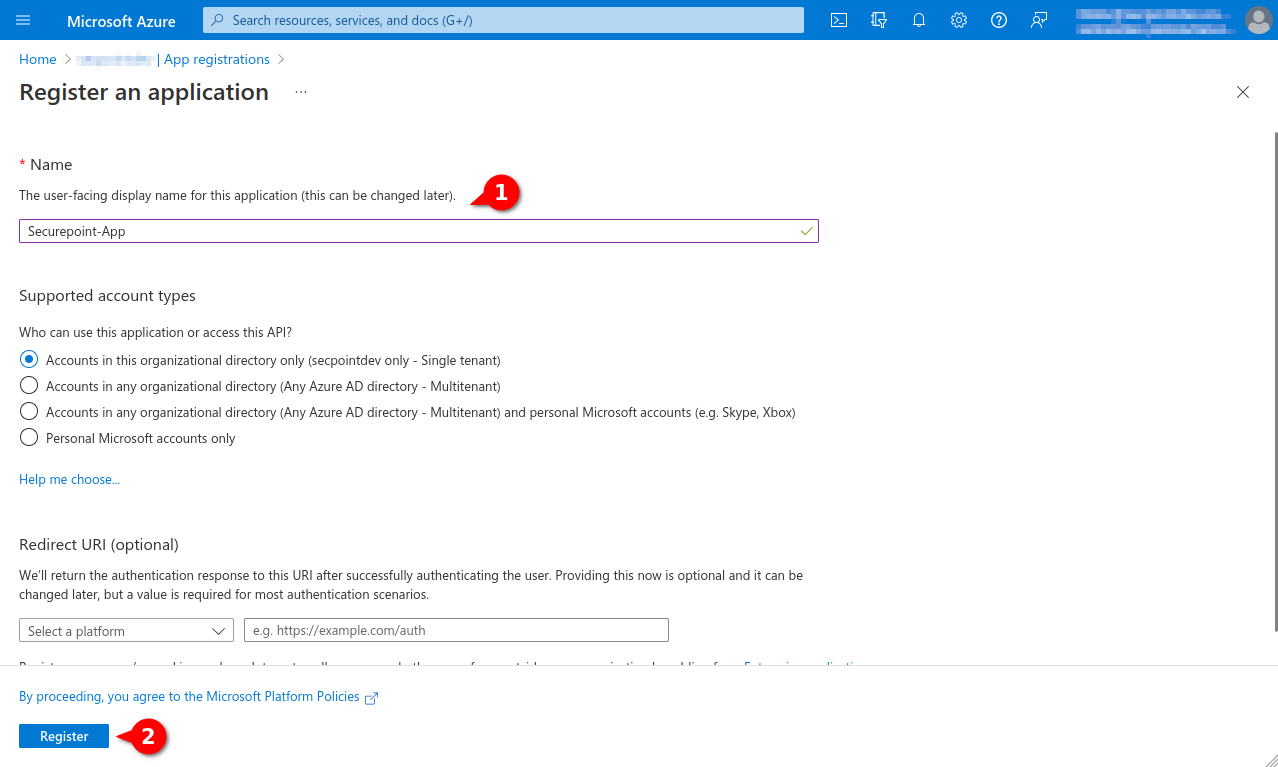
- Assign a unique name and click the register button
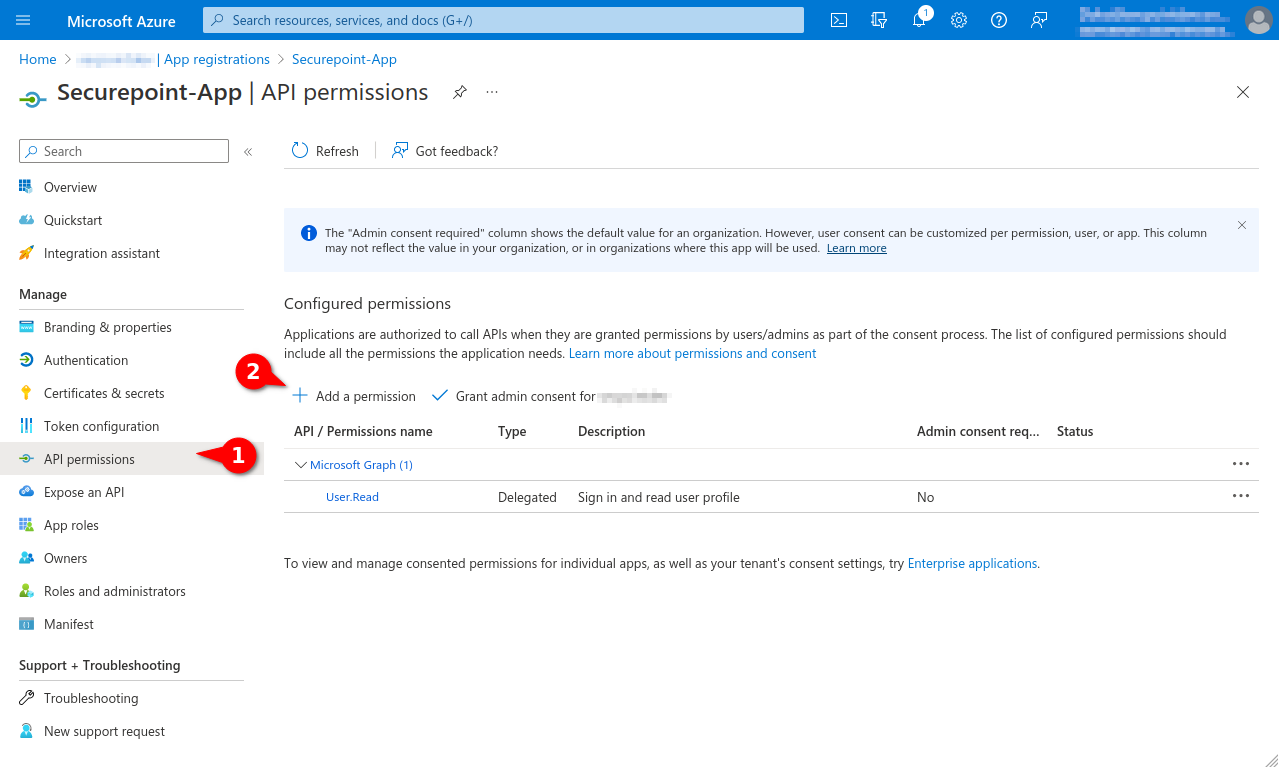
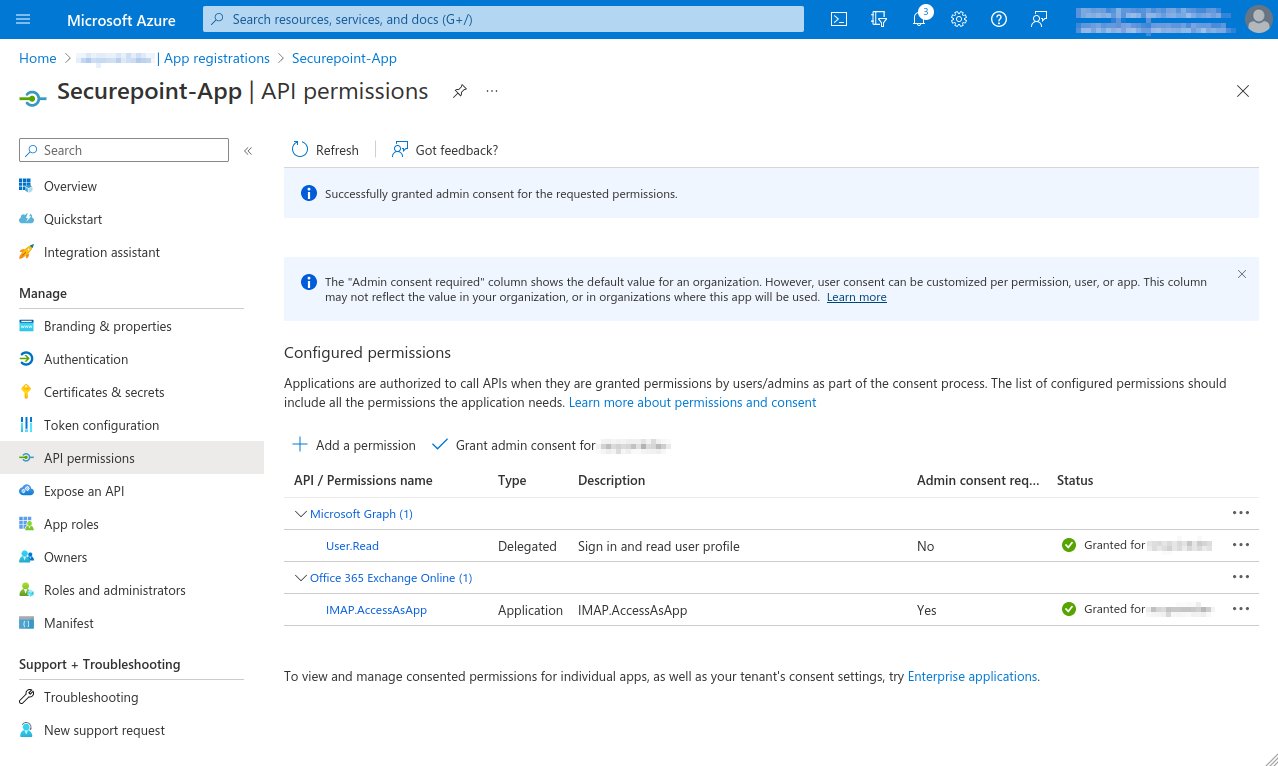
- In the API permissions menu, click the Add a permission button.
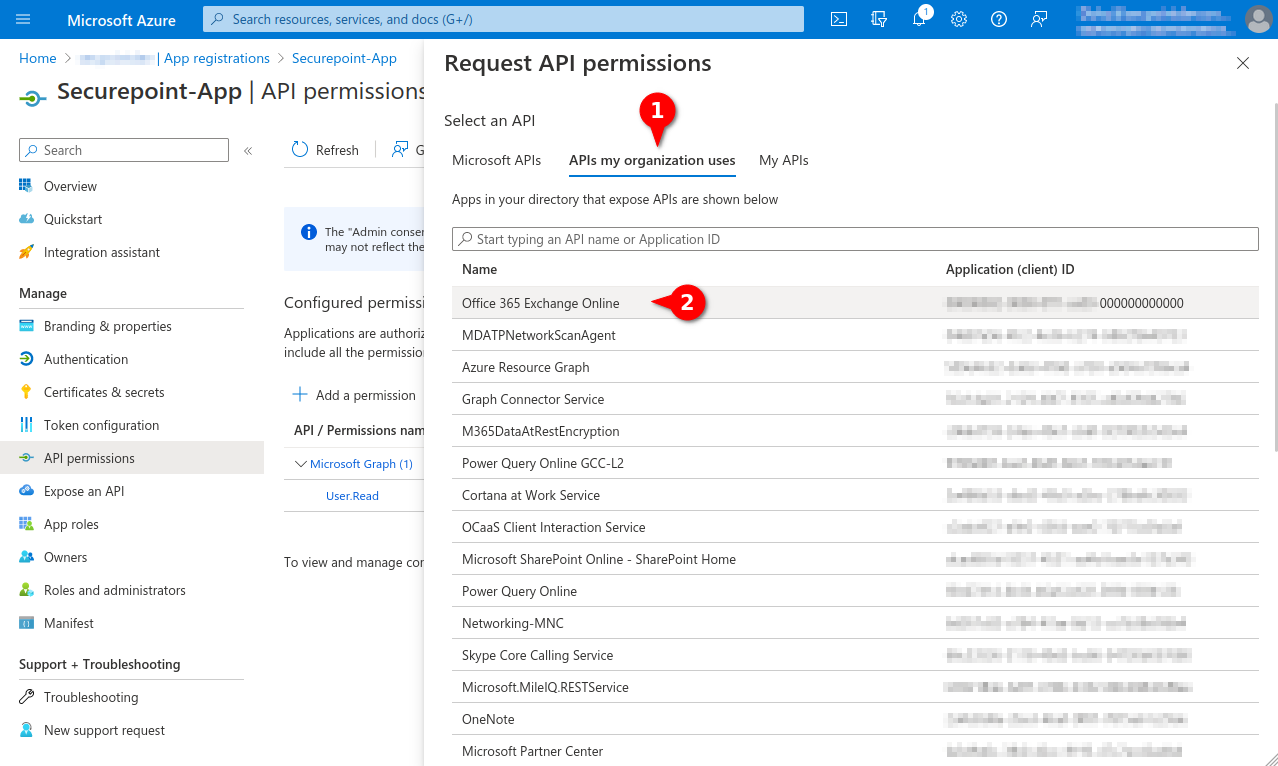
- Select permission for Office 365 Exchange Online in the APIs my organization uses tab
- Add IMAP.AccessAsApp permission for Office 365 Exchange Online
- In the menu API permissions activate the entry Grant admin consent for [...].
- Create a Client secret in the Certificates & secrets menu
- Note down Value, is entered as Client secret for Remote e-mail accounts and Import single mailboxes
- Open menu Enterprise Applications and select app
- Note down from the app properties Application ID and Object ID.
- Open Powershell on Windows Client Administrator, import ExchangeOnlineManagement and connect to tenant
- Select the recipient mailbox in the Exchange admin center and choose Read and manage (Full Access) as delegation.
- Add member for Mailbox Delegation
- This completes the configuration in Microsoft Azure.
Further configuration is done in the UMA in the
System settings Tab Email accounts section Azure AD menu, in the setup wizard or when importing mailboxes. - The Microsoft servers may take up to 30 minutes before access works
| 1. | 2. | 3. |
| Abb.1 | Abb.2 | Abb.3 |
| Abbildungen | ||
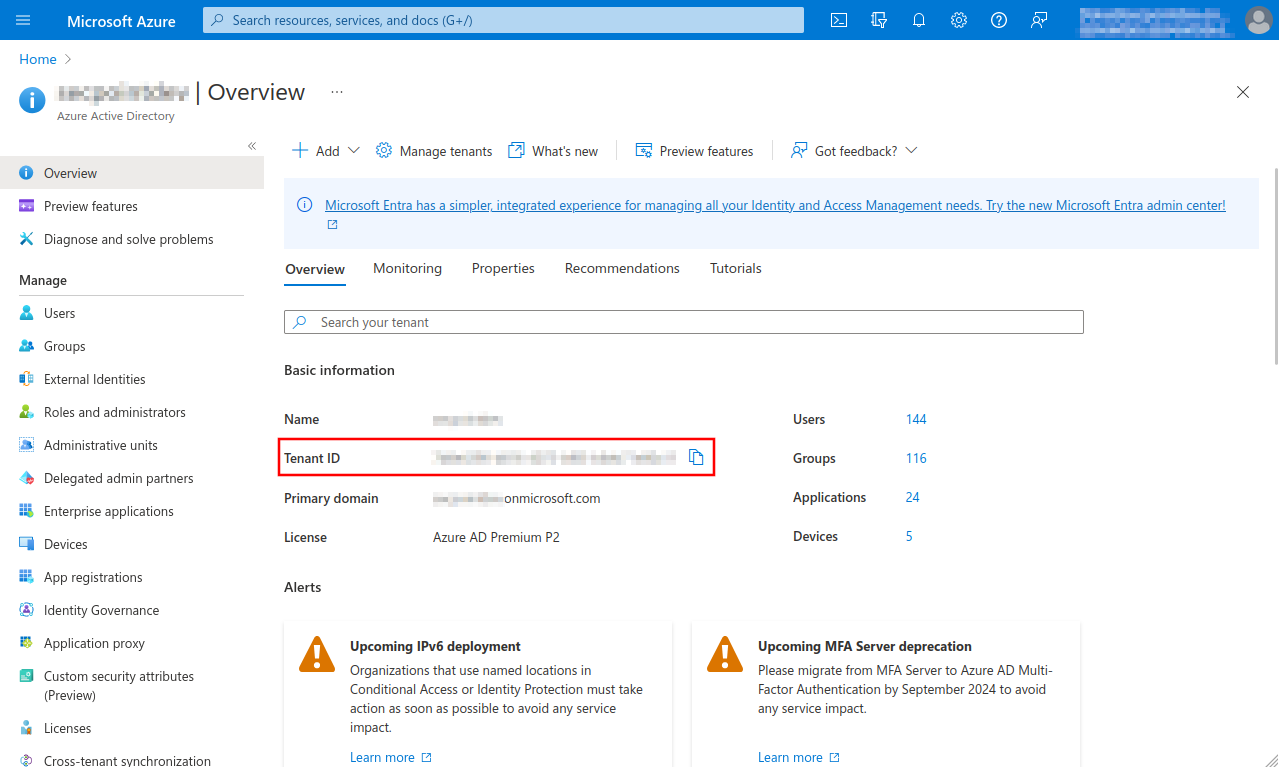
Fig.1
- Select Azure Active Directory menu
- Note down or copy Tenant ID, is entered for remote e-mail accounts and for importing single mailboxes
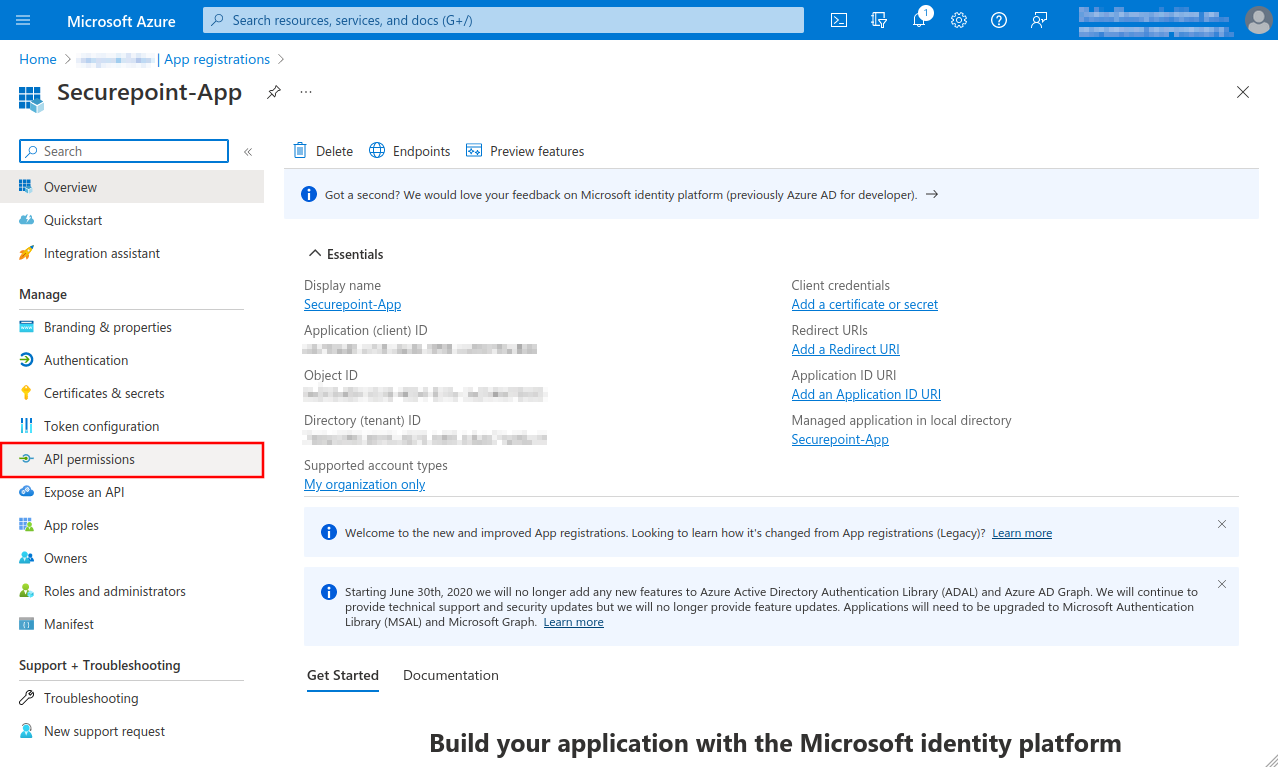
Fig.4
A summary of the newly registered app is displayed
The Object ID displayed here does not belong to the app and is not needed!
Select API permissions menu
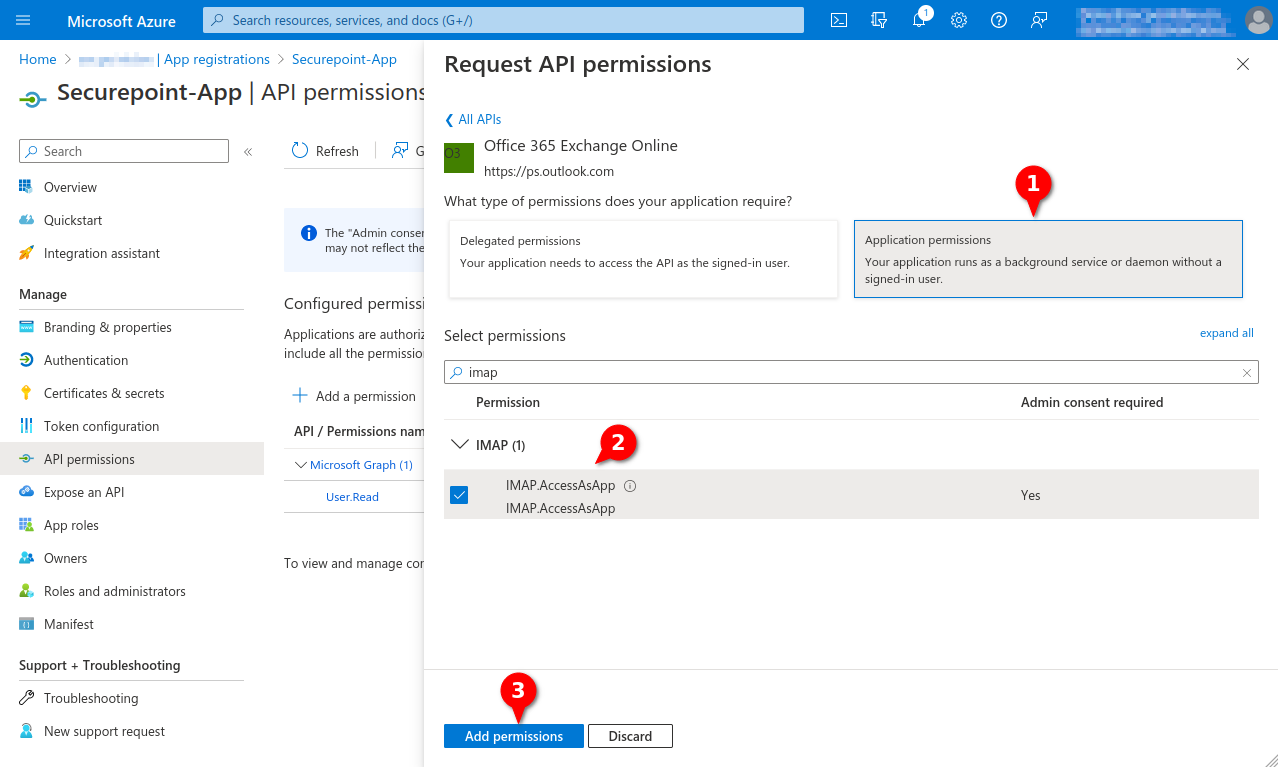
Fig.7
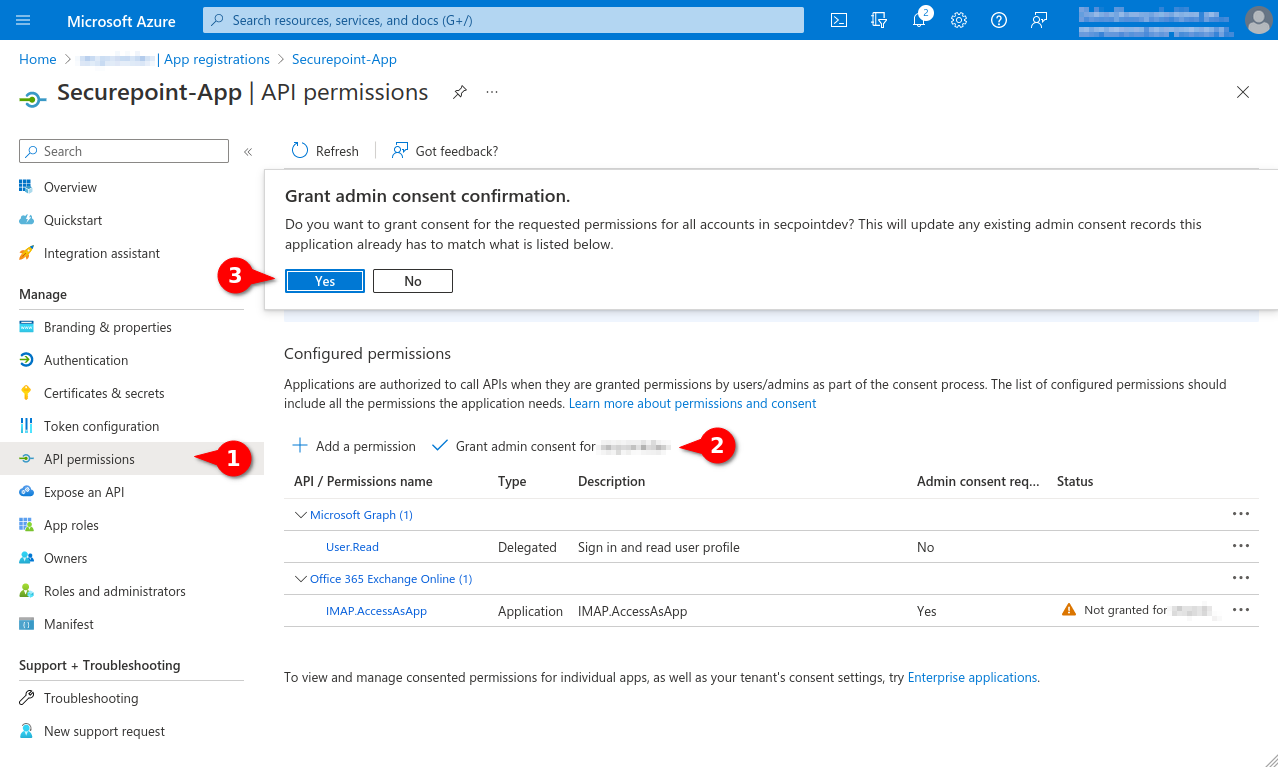
Fig.8
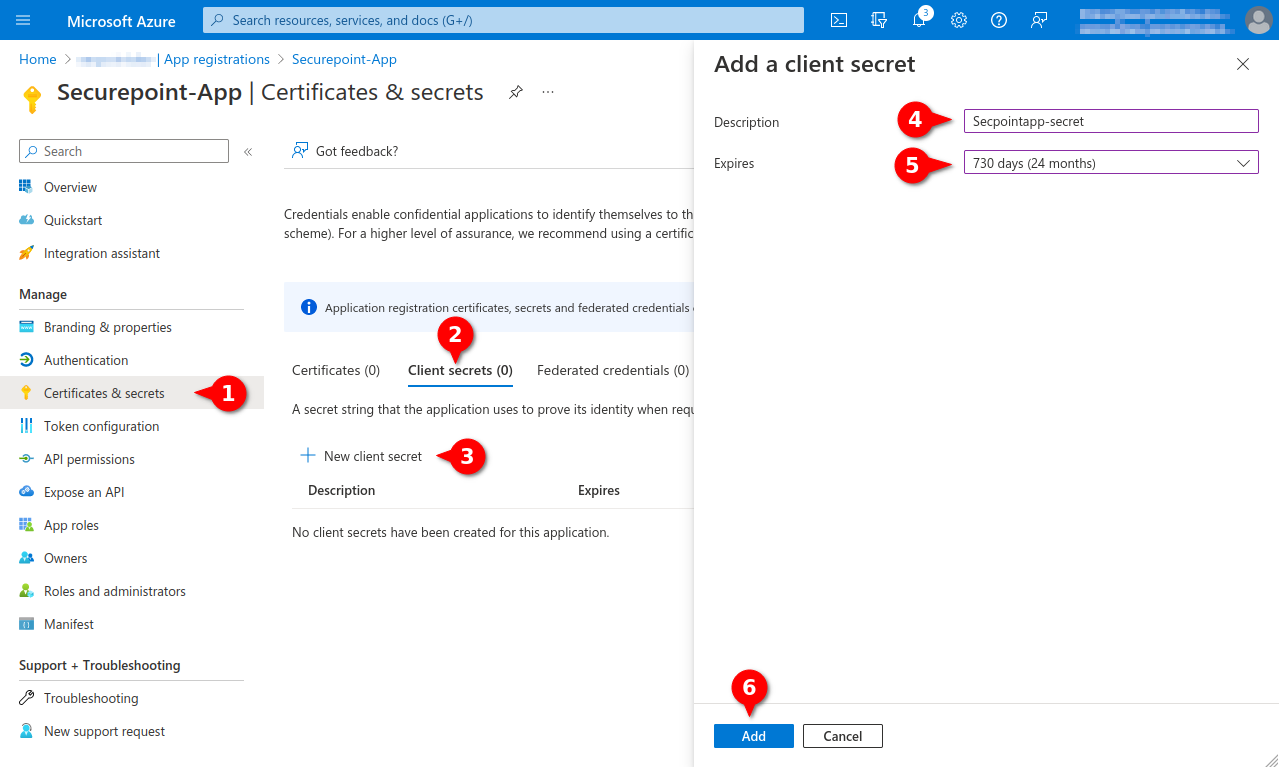
Fig.10
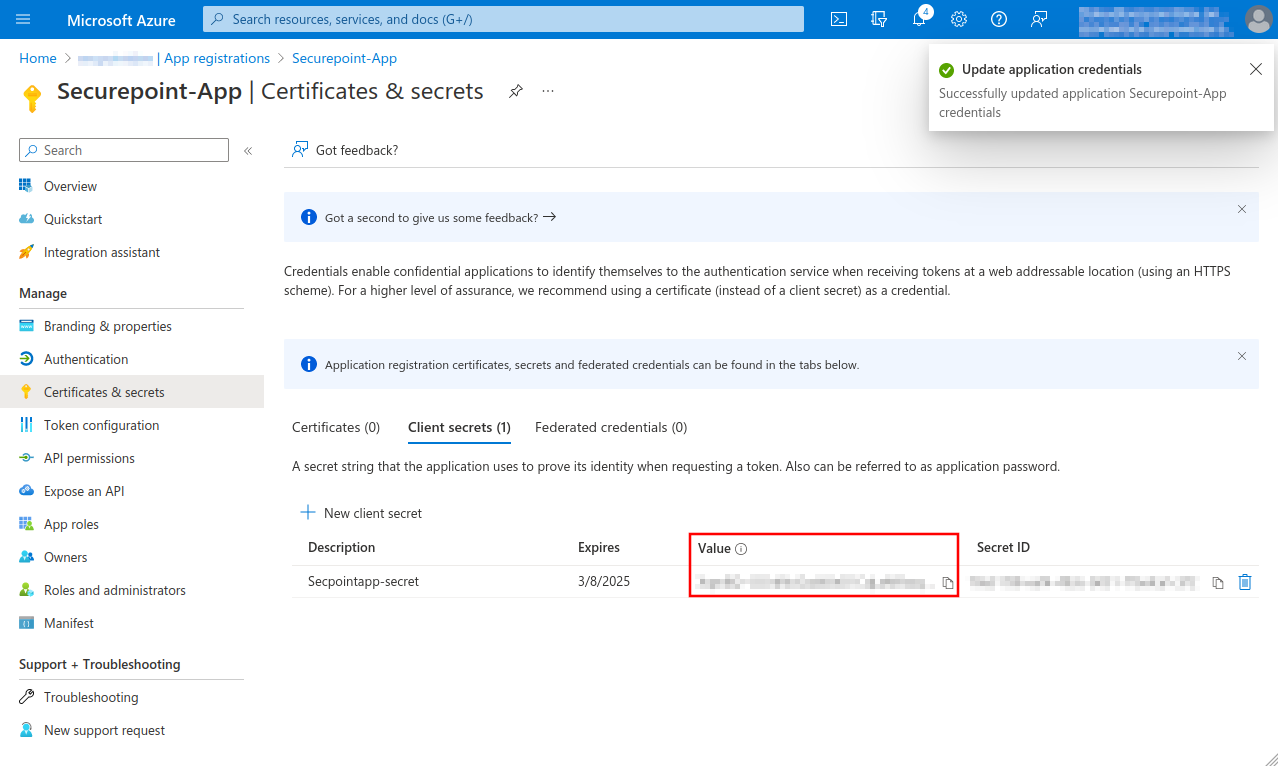
Fig.11
Note down Value, is entered as Client secret for Remote e-mail accounts and Import single mailboxes
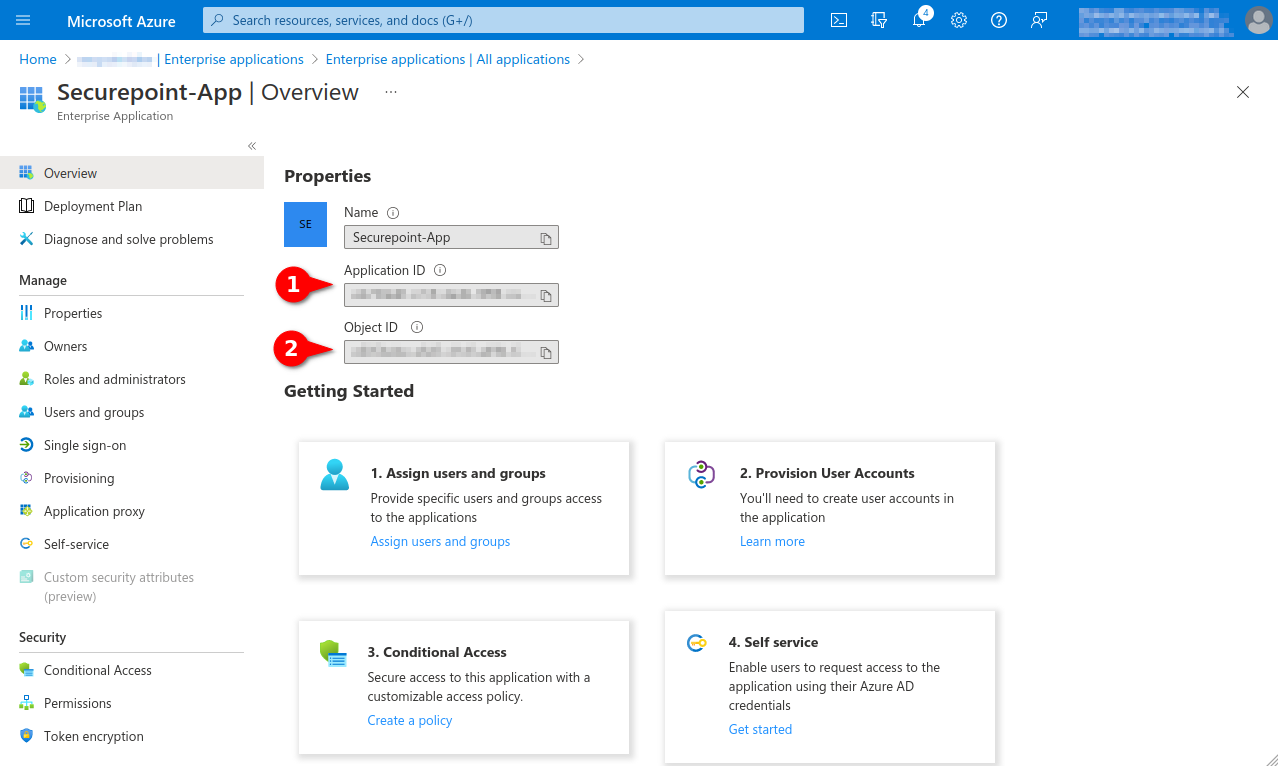
Fig.14
Note down from the app properties:
Application ID, is entered as Application (Client) ID for Remote E-mail Accounts and Import Individual Mailboxes
Object ID, is required for the granting of the authorisation via Powershell
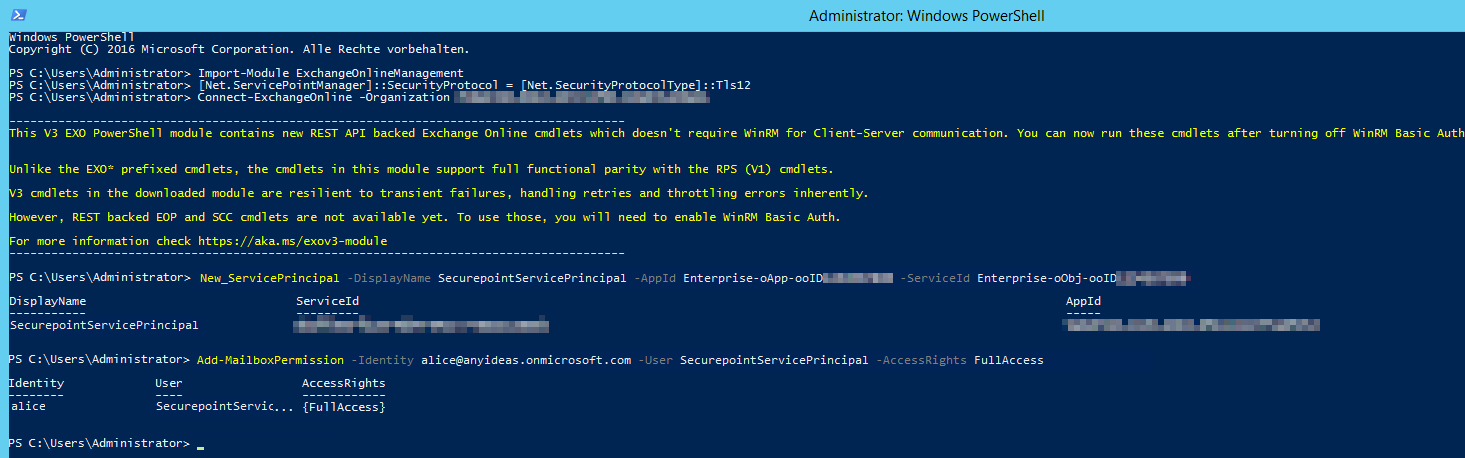
Fig.15
If there are problems installing the module or connecting, you may need to configure Powershell to TLS 1.2:
>[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
>[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
- > Install-Module -Name ExchangeOnlineManagement -allowprerelease
- > Import-module ExchangeOnlineManagement
- > Connect-ExchangeOnline -Organization Tenant ID (See Fig.1)
- > New-ServicePrincipal -DisplayName SecurepointServicePrincipal -AppId Enterprise-oApp-ooID-oooo-oooooooo -ServiceId Enterprise-oObj-ooID-oooo-oooooooo
- For Enterprise-oApp-ooID-oooo-oooooooo enter the Application ID and for Enterprise-oObj-ooID-oooo-oooooooo enter the Object ID (see Fig. 14)
- > Add-MailboxPermission -Identity alice@anyideas.onmicrosoft.com -User SecurepointServicePrincipal -AccessRights FullAccess
The Microsoft servers may take up to 30 minutes before access works