Last adaptation to the version: 2.12 (12.2025)
- Überprüfung auf eine VPP-Lizenz beim Hinzufügen von iOS-Profilen als Roadwarrior
Prerequisite
Introduction
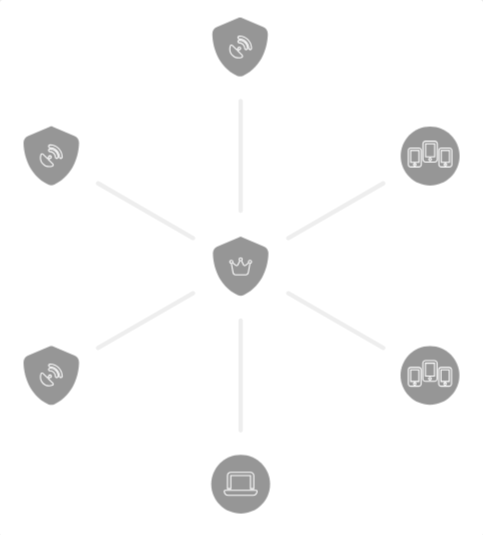
- The VPN configuration enables simple networking of UTMs via a star-shaped network topology
- At the center is a core UTM, which acts as a central node.
From here, several locations can be securely connected to each other via satellite UTMs. - In addition, groups of mobile end devices can be connected as road warriors
First configuration steps:
- Selection of the company headquarters as the core UTM.
It forms the center of the star topology. - Connection of further UTMs from other locations as satellites
- Configuration of the Roadwarrior for mobile devices
Configuration of the Core-UTM
Add Core UTM
| Add Core now Opens the dialog for adding a core UTM. |  | |||||||||||||||
| It is possible to have several core UTMs. Each core UTM is assigned to a topology Topology 1 Default designation and it is numbered consecutively
If a further Core-UTM and thus a further topology is to be added, this is done with the button Add topology | ||||||||||||||||
| Caption | Value | Description | 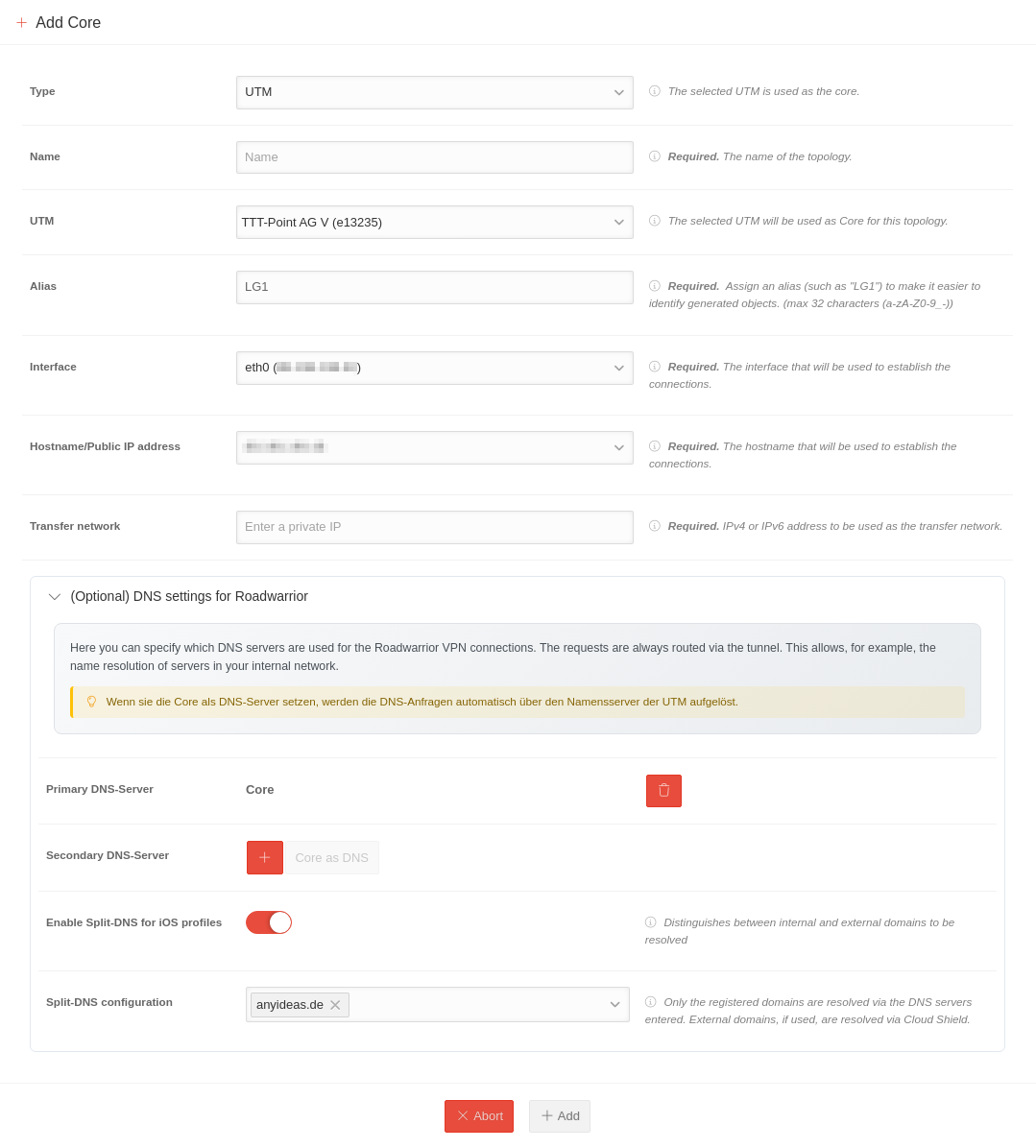 | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Typ | UTM | Als Typ UTM auswählen | ||||||||||||||
| Name Mandatory field |
Name | Name of the topology
Dialog box for adding a core UTM | ||||||||||||||
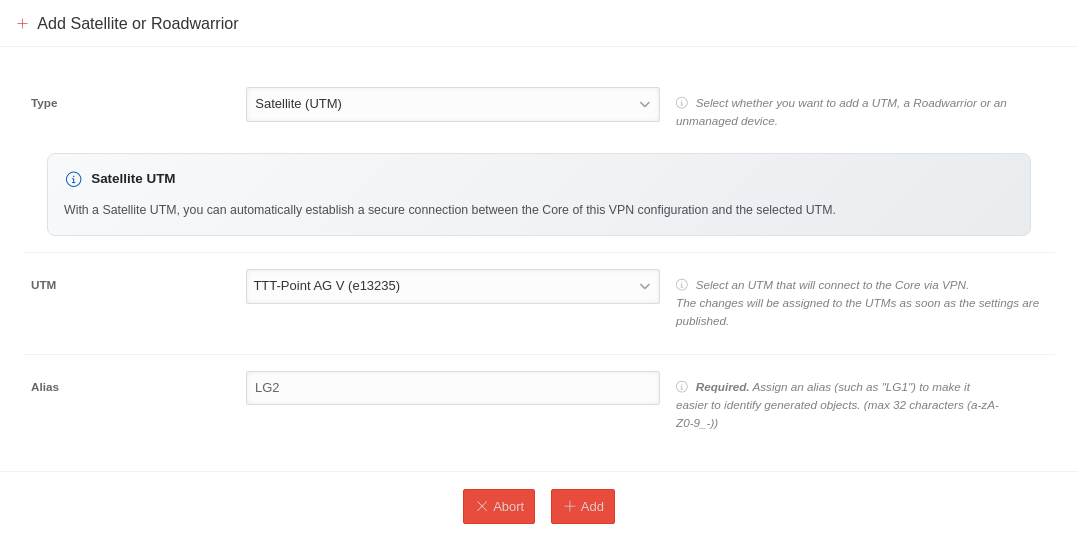
| UTM | TTT-Point AG V | List of available UTMs that can be selected as core UTMs. Only UTMs that have a public IP address, are connected to the portal and are online are available for selection. UTMs that are connected to the portal but are offline, or whose version is not compatible, are listed in the not available list section. The next steps are only displayed after a UTM has been selected. | ||||||||||||||
| Alias Mandatory field |
LG1 | An alias must be assigned for the core UTM in order to be able to assign generated objects to this UTM. | ||||||||||||||
| Interface Mandatory field |
eth0 (203.113.0.113) | The interface of the core UTM to be used for establishing the connection. ‘’'By default'‘’ the first interface that is connected to the Internet is used. | ||||||||||||||
| Hostname/ public IP address Mandatory field |
203.113.0.113 | The host name, or the public IP address, which is used to establish the connection. ‘’'By default'‘’ the public IP address of the Internet interface of the UTM is used. | ||||||||||||||
| Transfer network Mandatory field |
192.168.20.0/24 | Private IPv4 or IPv6 address to be used as the transfer network. | ||||||||||||||
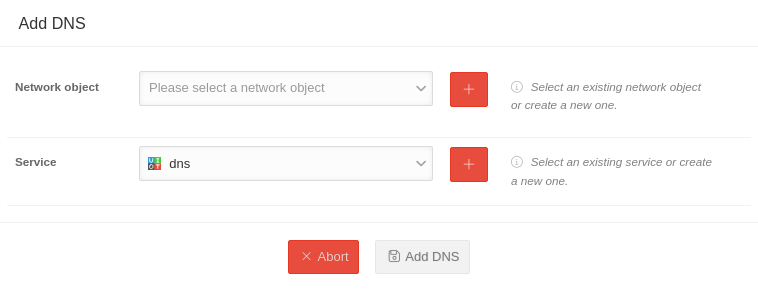
| (Optional) DNS-Einstellungen für Roadwarrior | ||||||||||||||||
| Hier kann festgelegt werden, welche DNS-Server für die Roadwarrior VPN-Verbindungen verwendet werden sollen. Die Anfragen werden grundsätzlich über den Tunnel geleitet. Dadurch kann beispielsweise die Namensauflösung von Servern im verwendeten internen Netzwerk ermöglicht werden. | ||||||||||||||||
| Primary DNS server (optional) | Add DNS Server | DNS servers in the network of the core UTM can be selected here so that the name resolution works for the Roadwarrior clients. Rules are automatically created in the Roadwarrior pools. | ||||||||||||||
| Core as DNS | The core UTM is used as the DNS server notempty Wenn die Core-UTM als DNS-Server gesetzt wird, werden die DNS-Anfragen automatisch über den Namensserver der UTM aufgelöst. | |||||||||||||||
| Network object Nicht bei Core als DNS |
Please select a Network object | Selection of a network object that is assigned to a DNS server. | ||||||||||||||
If no suitable network object is available, a new one can be created using the Add button .
| ||||||||||||||||
| Service Nicht bei Core als DNS |
Selection of the service or service group that makes DNS possible. | |||||||||||||||
If no suitable service is available, a new one can be created using the Add button .
| ||||||||||||||||
| Split-DNS für iOS Profile aktivieren Only appears when a DNS server has been selected notempty New as of: 2.8 |
Wenn aktiviert kann Split-DNS für iOS Profile verwendet werden.
Es wird zwischen internen und externen aufzulösenden Domains unterschieden. | |||||||||||||||
| Split DNS configuration Wird erst eingeblendet, wenn Split-DNS für iOS Profile aktiviert ist notempty New as of: 2.8 |
Add domains |
| ||||||||||||||
| The DNS server is added with the Add DNS button. | ||||||||||||||||
| Adds the UTM as a core UTM. The Add UTM button only becomes active once all entries have been completed | ||||||||||||||||
| This configuration must then be made usable with the Publish button. | ||||||||||||||||
Edit core UTM
| An active, connected core UTM can be edited via the wrench button . | ||||||||||||||||
| Caption | Value | Description | 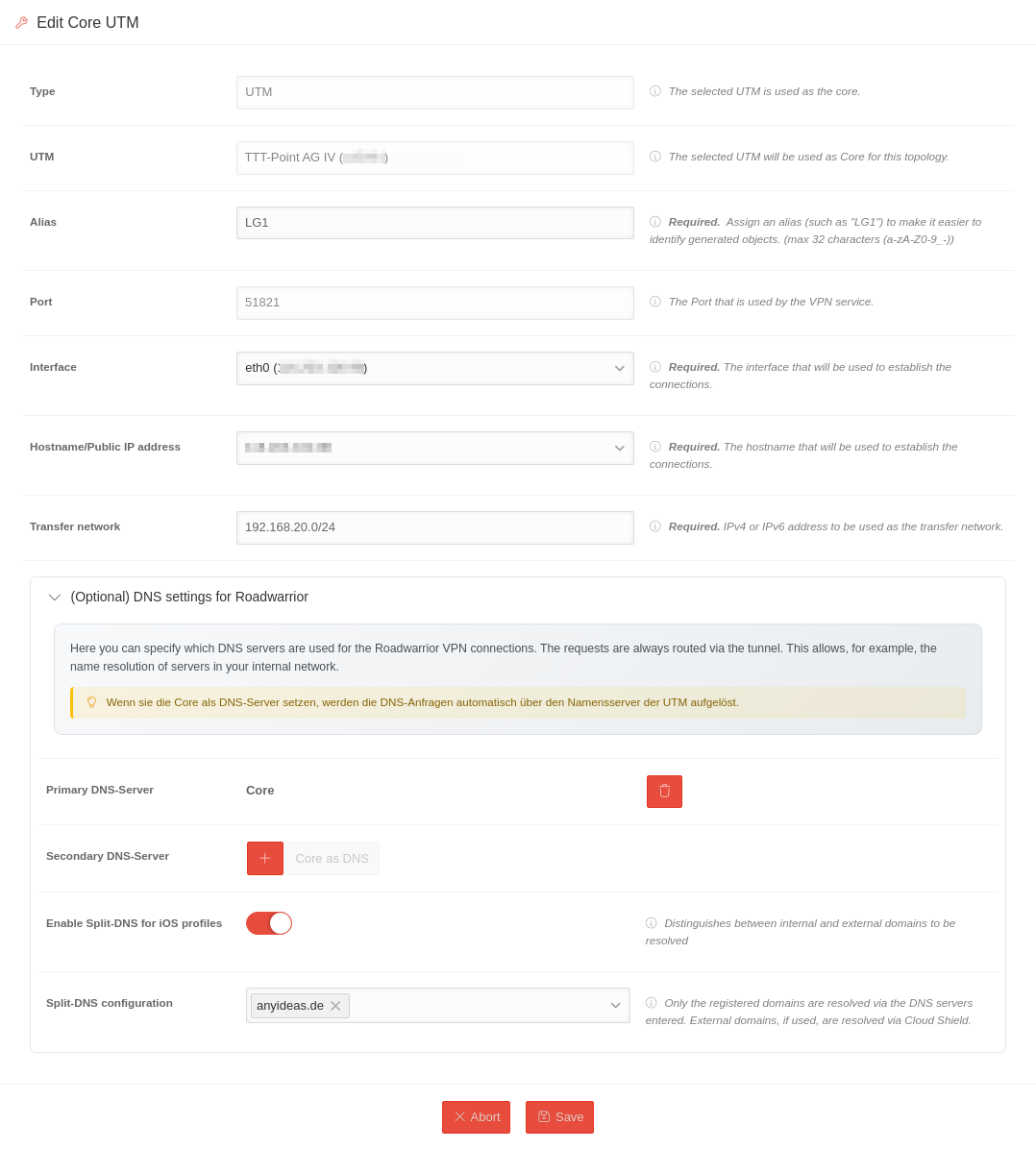 | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Name | Name | Name of the topology
Dialog box for adding a core UTM | ||||||||||||||
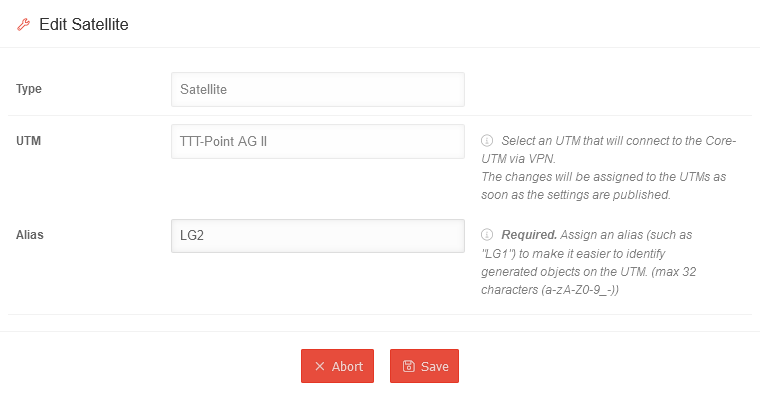
| UTM | TTT-Point AG IV | The UTM, which serves as the core UTM, cannot be changed retrospectively. | ||||||||||||||
| Alias Mandatory field |
LG1 | An alias must be assigned for the core UTM in order to be able to assign generated objects to this UTM. | ||||||||||||||
| Port | 51820 | Display of the port used by the VPN service. Cannot be changed. | ||||||||||||||
| Interface | eth0 (203.113.0.113) | The interface used to establish the connection. | ||||||||||||||
| Hostname/ public IP address | 203.113.0.113 | The host name or public IP address used to establish the connection. | ||||||||||||||
| Transfer network | 192.168.20.0/24 | IPv4 or IPv6 address to be used as the transfer network. | ||||||||||||||
| (Optional) DNS-Einstellungen für Roadwarrior | ||||||||||||||||
| Hier kann festgelegt werden, welche DNS-Server für die Roadwarrior VPN-Verbindungen verwendet werden sollen. Die Anfragen werden grundsätzlich über den Tunnel geleitet. Dadurch kann beispielsweise die Namensauflösung von Servern im verwendeten internen Netzwerk ermöglicht werden. | ||||||||||||||||
| Primary DNS server (optional) | Add DNS Server | DNS servers in the network of the core UTM can be selected here so that the name resolution works for the Roadwarrior clients. Rules are automatically created in the Roadwarrior pools. | ||||||||||||||
| Core as DNS | The core UTM is used as the DNS server notempty Wenn die Core-UTM als DNS-Server gesetzt wird, werden die DNS-Anfragen automatisch über den Namensserver der UTM aufgelöst. | |||||||||||||||
| Network object Nicht bei Core als DNS |
Please select a Network object | Selection of a network object that is assigned to a DNS server. | ||||||||||||||
If no suitable network object is available, a new one can be created using the Add button .
| ||||||||||||||||
| Service Nicht bei Core als DNS |
Selection of the service or service group that makes DNS possible. | |||||||||||||||
If no suitable service is available, a new one can be created using the Add button .
| ||||||||||||||||
| Split-DNS für iOS Profile aktivieren Only appears when a DNS server has been selected notempty New as of: 2.8 |
Wenn aktiviert kann Split-DNS für iOS Profile verwendet werden.
Es wird zwischen internen und externen aufzulösenden Domains unterschieden. | |||||||||||||||
| Split DNS configuration Wird erst eingeblendet, wenn Split-DNS für iOS Profile aktiviert ist notempty New as of: 2.8 |
Add domains |
| ||||||||||||||
| This configuration must then be made usable with the Publish button. | ||||||||||||||||
Configuration of the satellite UTMs
Add Satellite-UTM
Edit Satellite-UTM
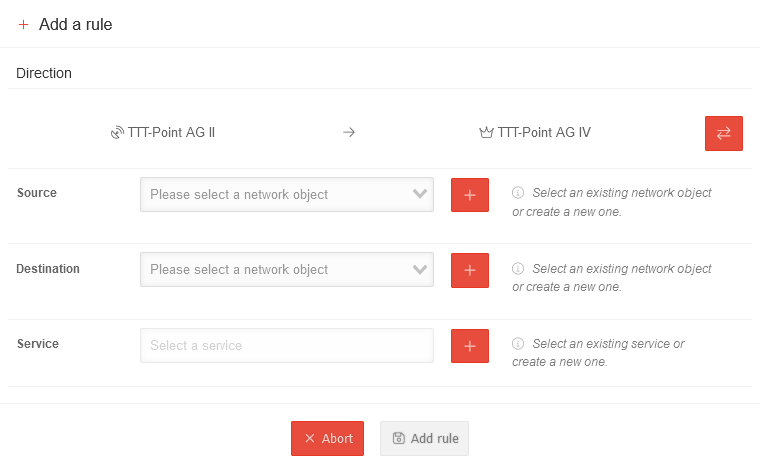
Add Satellite-UTM rule
Configuration of the Roadwarrior
Add Roadwarrior
| To add a Roadwarrior, click the Satellit / Roadwarrior button on an active, connected core UTM. A dialog window will open where the new Roadwarrior can be configured | |||
| Caption | Value | Description | 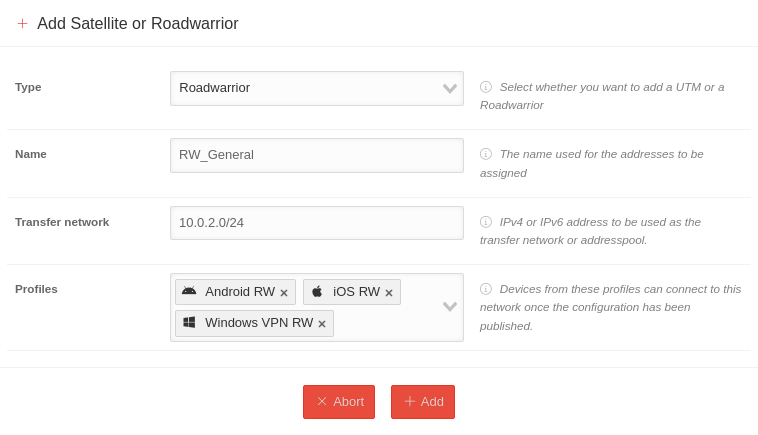 |
|---|---|---|---|
| Type | Roadwarrior | Select Roadwarrior as the type | |
| Name | RW_General | The name to be used for this Roadwarrior | |
| Transfer network | 10.0.2.0/24 | Enter a private IPv4 or IPv6 address to be used as the transfer network. | |
| Profile |
Android RW iOS RW Windows VPN RW | Profile selection. Possible options are
Devices from these profiles can be connected to this network after the configuration is published. | |
| Only when all fields are filled in does the Add button become active, and the Roadwarrior can then be added using it. | |||
| Finally, this configuration must be applied using the Publish button. | |||
Edit Roadwarrior
| A Roadwarrior can be edited via the button | |||
| Caption | Value | Description | 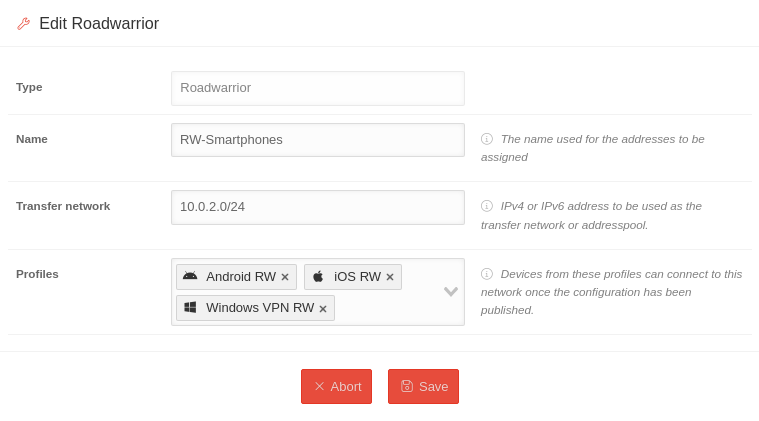 |
|---|---|---|---|
| Type | Roadwarrior | The type of a Roadwarrior cannot be changed | |
| Name | RW-Smartphones | The Name used for this Roadwarrior. | |
| Transfer network | 10.0.2.0/24 | IPv4- or IPv6 address, to be used as the transfer network | |
| Profile |
Android RW iOS RW Windows VPN RW | Profile selection. Possible options are
Devices from these profiles can be connected to this network after the configuration is published. | |
| Finally, this configuration must be applied using the Publish button. | |||
Add Roadwarrior rule
| Caption | Value | Description | 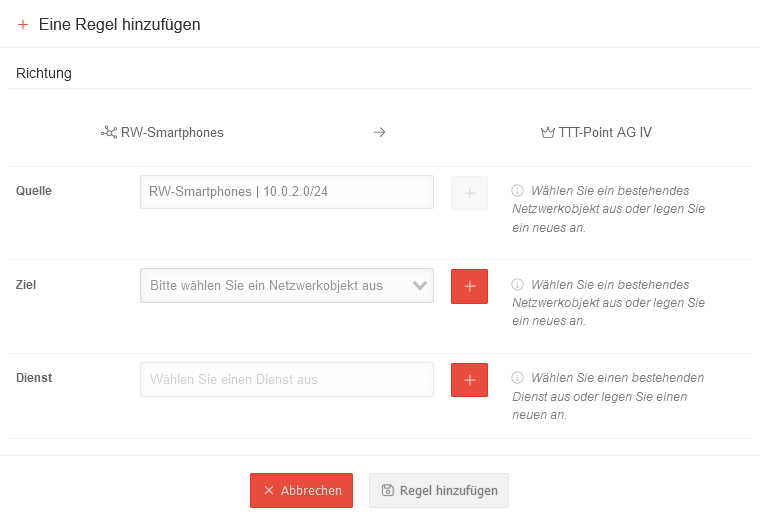 | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Direction | Roadwarrior Core-UTM | Indicates the direction of the packet filter rule (Source → Destination) | ||||||||||||||
| Source | Roadwarrior | 10.0.2.0/24 | The source of the packet filter rule is always the address pool of the transfer network in which the Roadwarriors are located. (Cannot be changed) | ||||||||||||||
| Destination | Please select a network object | Selection of an existing network object. Existing network groups and network objects are listed. | ||||||||||||||
If no suitable network object is available, a new one can be created via the button.
| ||||||||||||||||
| Service | Select a service | Selection of an existing service. Existing service groups and services are listed. | ||||||||||||||
| ||||||||||||||||
Overview
General options
| Button | Description |  | |
|---|---|---|---|
| Topology 1 | The number of Core-UTMs and their topologies. With Add topology another Core-UTM can be added. Further information in section Add Core-UTM. | ||
| Discard changes | Changes that have not yet been published can be undone again | ||
| Publish | Changes made and new configurations are published and thus activated and made usable | ||
Configuration options
The existing configurations are displayed: The core UTMs and their associated satellite UTMs and roadwarriors.
These are displayed with their respective associated information.
Different actions are available depending on the object.
| Actions | Description | 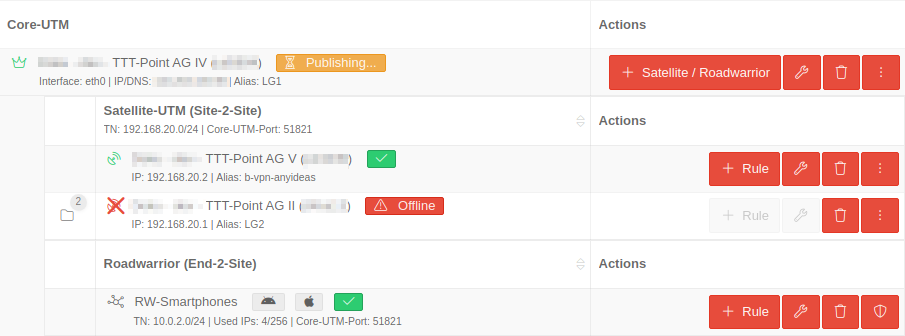 This overview is only visible once a core UTM has been added. | |
|---|---|---|---|
| Edit | Opens the dialog to edit the object | ||
| Delete | Deletes the respective object and all subordinate objects When the core UTM is deleted, all satellite UTMs and road warriors are also deleted | ||
| Open menu Core or Satellite |
UTM details | Opens the detailed display for this UTM in the menu | |
| Exchange UTM | Replaces the core or satellite UTM of the existing VPN configuration. Further information on this can be found in the section Exchange UTM. | ||
| Update | Updates the view of the stored information | ||
| Websession | Opens the dialog to start the administrative web interface of the UTM. Further information can be found in the following | ||
| Satellite / Roadwarrior Core-UTM |
Adds a new Satellite UTM or a new Roadwarrior. For more information, see the sections Add Satellite UTM and Add Road Warrior. | ||
| Rule Satellite or Roadwarrior |
Adds a new packet filter rule. For more information, see Add satellite UTM rule. | ||
| Adds a new packet filter rule. For more information, see Add roadwarrior rule. | |||
| Profiles Roadwarrior |
Displays the Roadwarrior profiles that are connected to the Core-UTM. Click on the profile to edit it. | ||
Show status | |||
| Different status displays are shown depending on the object. If you hover over the status display, further information is displayed. | |||
| Status display | Description | ||
| Not published | Indicates that the object has been added but has not yet been published | ||
| Not published | Indicates that there have been changes to the object that have not yet been published | ||
| Not published | Indicates that the object has been deleted but not yet published | ||
| Publish... | Indicates that the configuration is in the process of being published. This process may take some time. | ||
| Indicates that the core UTM is connected | |||
| Offline | Indicates that the core UTM is not connected | ||
| Indicates that the Satellite UTM is connected | |||
| Offline | Indicates that the Satellite UTM is not connected | ||
| This address pool is linked and there are no changes to be published | |||
| ✕ | This address pool is not connected | ||
| Shows which profile type (Android or iOS) this address pool belongs to. If you hover over the status label, the name of the profile is displayed. | |||
Exchange UTM | |||
| This function offers the option of replacing the core and satellite UTM in an existing VPN configuration without losing settings or even having to create a new VPN configuration.
This makes it possible, for example, to replace a faulty UTM in a VPN configuration so that this configuration works again. It is irrelevant whether the UTM to be replaced is online or not.It is not possible to exchange a satellite UTM directly with a core UTM and vice versa. This requires another third UTM as a ‘'placeholder UTM’'. | |||
| notempty Before the new UTM can be exchanged, strongly recommends to create a new backup of the old UTM! It is irrelevant whether it is a manual backup (further information in this Wiki article), or a Cloudbackup. | |||
Procedure for replacing a UTM:
Further information can be found in the Wiki article Exchange core/satellite UTMs | |||
Display on the UTM
General rules
In general, several rules are automatically generated on the relevant UTMs. These rules are marked in the ‘'Models’' column, the rules overview on the UTM, so that it is clear where they come from. In addition, these rules can only be edited, deleted or copied using the portal and not on the UTM itself.
Outgoing data traffic is automatically permitted. Incoming packets on the core UTM that do not correspond to the configured service/port are discarded.
It should also be noted that services are always newly created in order to avoid possible interference with existing services, which may then be changed.
Presentation of the satellite rules
| Pos. | # | Source | Destination | Service | NAT | Logging | Action | Cloud | Active | ||
| Generated rules of the Core-UTM for an example rule from a satellite UTM to the core UTM: | |||||||||||
| LG2-rules | 2 | On | |||||||||
| ACCEPT | On | ||||||||||
| ACCEPT | On | ||||||||||
| Generated rules of the Satellite-UTM for an example rule from a satellite UTM to the core UTM: | |||||||||||
| LG1-rules | 1 | On | |||||||||
| ACCEPT | On | ||||||||||
| When generating a rule between a satellite UTM and the core UTM, a total of three packet filter rules are generated. Two on the destination UTM and one on the source UTM.
On the target UTM (here Core-UTM), this includes an inbound rule with the selected service and an Any rule for outbound data to the source UTM (here Satellite-UTM). | |||||||||||
Presentation of the Roadwarrior rules | |||||||||||
| Generated rules on the Core-UTM for a Roadwarrior rule: | |||||||||||
| RW-Smartphones-rules-2 | 2 | On | |||||||||
| ACCEPT | On | ||||||||||
| ACCEPT | On | ||||||||||
| When creating a rule between a Roadwarrior network and the Core-UTM, two packet filter rules are generated on the Core-UTM.
These include an inbound rule with the corresponding service and an outbound rule, i.e. an ‘'Any’' rule. | |||||||||||
Display of network objects
| There are two different types of network objects that are created by the VPN configuration. On the one hand, there are those that refer to another object in the configuration and are generated completely automatically when a rule is created (here, for example, LG2-any-network-v4). On the other hand, there are those that are created on the UTM itself by the user using the button (here, for example, vpn-network). | UTMuser@firewall.name.fqdnFirewall 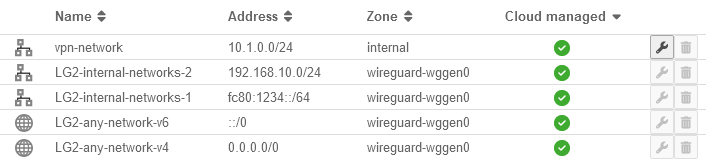 Generated network objects on the Core-UTM Generated network objects on the Core-UTM
|