notempty
Last adaptation to the version: 12.6.2
- Updated to Redesign of the webinterface
- Automatic Updates can be configured on UTM if USC is activated.
- 04.2024 (Screenshot updated for available version)
Introduction
- In order for the UTM to receive updates, it must be able to reach the Internet and DNS resolution must work
- The UTM checks every 120 minutes whether a new update is available on the update servers
- Due to the high number of UTMs that want to download an update, they are distributed over a certain period of time
This distribution is carried out by the update servers - The update will then be downloaded automatically
- The UTM always downloads a complete firmware image for the corresponding version
- For cluster devices, please refer to the Cluster Management Wiki.
Planning update
notempty
Update detection
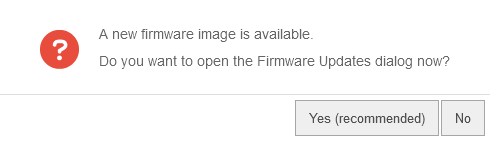
If the UTM has detected a new version on the update servers and has been completely downloaded, a message is displayed on the administration interface with the next login. If the message is confirmed with , a forwarding to the menu takes place.
Firmware Update
| Caption | Value | Description | UTMuser@firewall.name.fqdnExtras 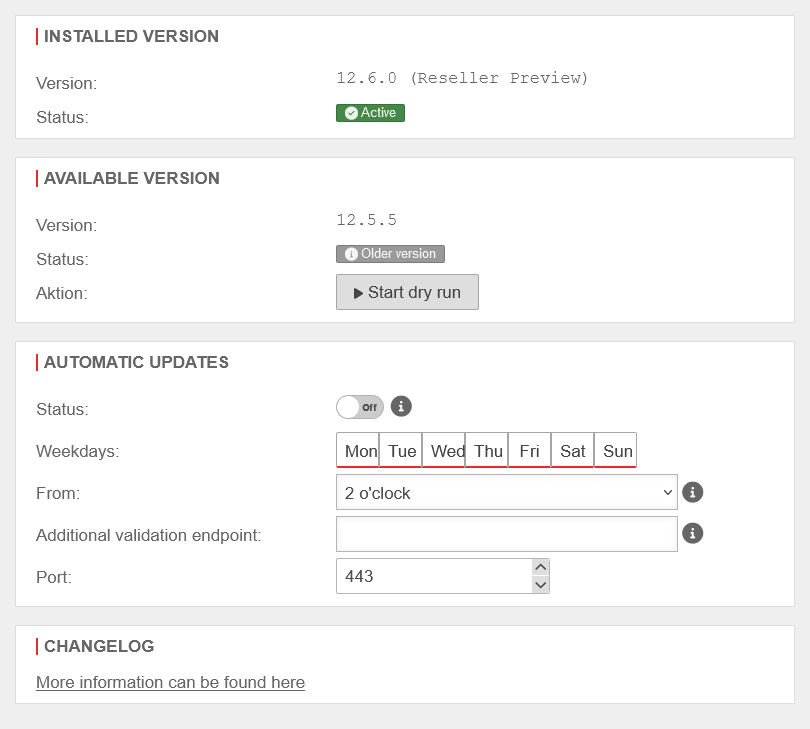
|
|---|---|---|---|
Installed version
| |||
| Version: | The currently running version | ||
| Status: | Active | ||
| Disabled for dry run | |||
Available version
| |||
| Version: | Installable version | ||
| Status: | Newer version | ||
| Older versions | For rollback | ||
| Aktiv dry run | notempty Do not perform a factory reset during the dry run! | ||
| Start update process
| |||
| The previously installed version is reactivated. The UTM restarts in the process. | |||
| The version is set as the future boot version. | |||
Automatic updates
| |||
| Status: | Off | When activated, updates are automatically installed, started and finalised.
| |
| Week days: | The days of the week on which the updates are to be installed and started automatically. | ||
| From: | The time from which the updates should be automatically installed and started. | ||
| Additional audit endpoint: |
Additional endpoint of a server (host name or IP address) whose accessibility should also be tested before finalisation. Before a dry run is started, i.e. even after an update has been installed and started (before it is finalised), the appliance will test whether the Securepoint update server can be reached. If a test fails, no firmware update is performed and, if necessary, a rollback to the previous version is carried out. | ||
| Port: | 443 | The port to the additional test endpoint | |
| Updates the display of the version available on the UTM. | |||
| Manual download of the latest firmware, even if this UTM is not yet scheduled in the normal distribution.
| |||
| Save | Saves the settings | ||
CLI code to activate the feature
extc value set { application spupdater variable AUTO_UPDATE_ENABLE value [ "1" ] }
By default, the feature is "Off". When activated without further configuration, daily updates are enabled from 2 a.m.
If the Securepoint Update Server is not reached after the update, a reboot with the previous firmware is performed.
CLI code for configuring the auto-update function:
extc valuelist set [ { application "spupdater" values [ { variable "AUTO_UPDATE_ENABLE" value [ "1" ] } { variable "AUTO_UPDATE_TIME" value [ "3 MON,FRI,SUN" ] } { variable "AUTO_UPDATE_HOST_CHECK" value [ "pruefpunkt.local" ] } { variable "AUTO_UPDATE_HOST_PORT_CHECK" value [ "443" ] } ] } ]
For better readability with line breaks:
extc valuelist set [ { application "spupdater"
values [ { variable "AUTO_UPDATE_ENABLE" value [ "1" ] }
{ variable "AUTO_UPDATE_TIME" value [ "3 MON,SAT,SUN" ] }
{ variable "AUTO_UPDATE_HOST_CHECK" value [ "pruefpunkt.local" ] }
{ variable "AUTO_UPDATE_HOST_PORT_CHECK" value [ "443" ] }
] } ](Not copy-paste capable)
| Variable | Value | Description |
|---|---|---|
| AUTO_UPDATE_ENABLE | 1 | Enables the feature: value [ "1" ] or disables it: value [ "0" ] |
| AUTO_UPDATE_TIME | h d,d,d | Time for the update: hour followed by a space and a list of weekdays (comma-separated, without spaces) For example: 15 MON,SAT,SUN or 2 * MON - Monday TUE - Tuesday WED - Wednesday THU - Thursday FRI - Friday SAT - Saturday SUN - Sunday * - Every weekday |
| AUTO_UPDATE_HOST_CHECK | pruefpunkt.local | Endpoint of a server whose reachability should also be tested before finalizing, in addition to the Securepoint Update Server
|
| AUTO_UPDATE_HOST_PORT_CHECK | 443 | The port for the additional check endpoint |
UTMuser@firewall.name.fqdn 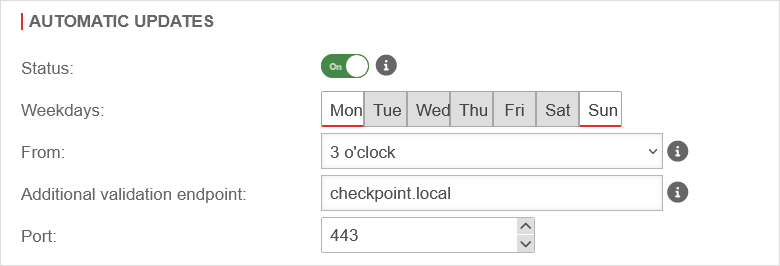 Display of values under Area Automatic Updates
Display of values under Area Automatic Updates
Display of values in the CLI
extc value get { application "spupdater" } application|variable |value -----------+---------------------------+----- spupdater |AUTO_UPDATE_ENABLE |1 |AUTO_UPDATE_HOST_CHECK |pruefpunkt.local |AUTO_UPDATE_HOST_PORT_CHECK|443 |AUTO_UPDATE_POST_CHECK |0 |AUTO_UPDATE_RUN |0 |AUTO_UPDATE_TIME |3 MON,SAT,SUN
Complete update
Acceptance of License Agreement and Privacy PolicyAcceptance of License Agreement and Privacy Policy | |
| After the update and a re-login to the administration web interface, the license agreement is displayed. This must be signed . If you decline the previous version will be reactivated. The privacy policy is displayed. This must be signed . If you decline the previous version will be reactivated. |
|
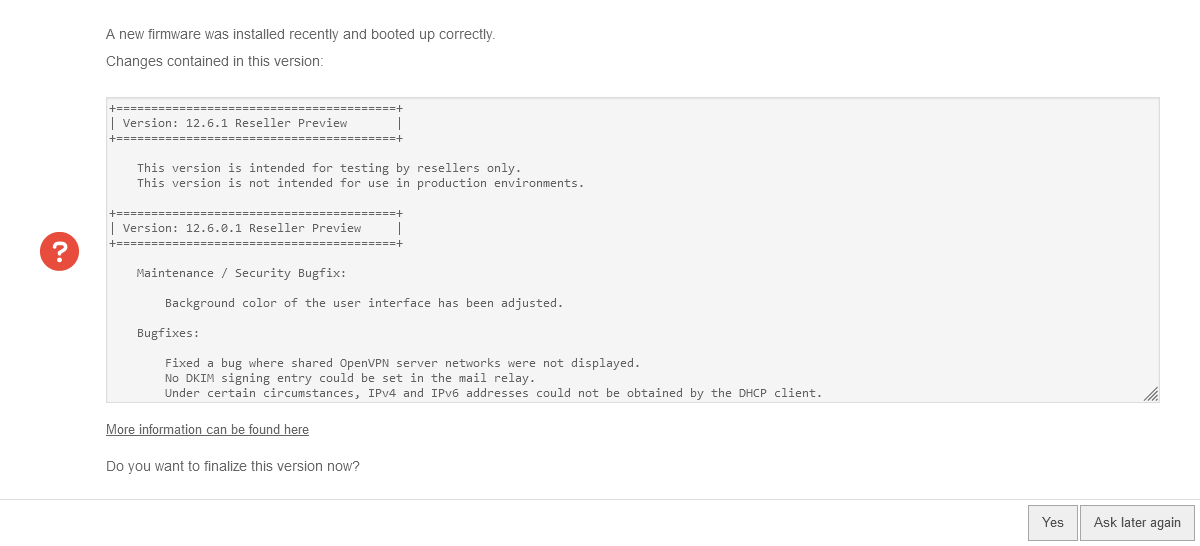
Changelog
| The changelog with the most important changes is displayed.
With , it can already be specified that this version will be used during the next startup. |
 | |
Dry runDry run | ||
|
UTMuser@firewall.name.fqdnExtras 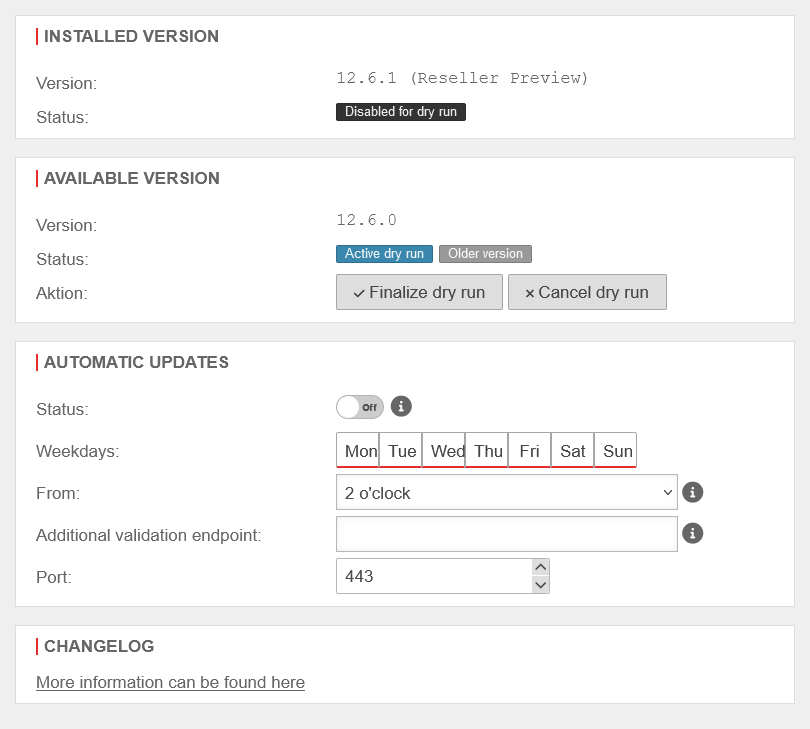 Finalize dry run Finalize dry run
| |
RollbackRollback | ||
A rollback sets the firmware to the last installed version.
|
UTMuser@firewall.name.fqdnExtras 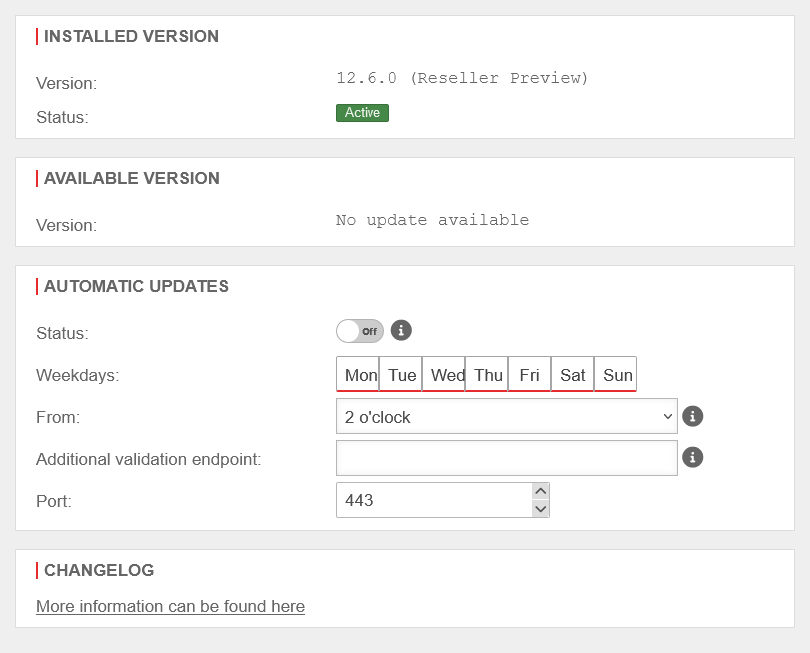 Rollback Rollback
| |
Troubleshooting
The system does not boot with the new firmware version
If the system does not boot properly after a restart, a reboot can re-enable the previous version.
The reboot can be done via the CLI (system reboot), the web interface (if accessible under or by pressing the power switch at the back of the case.
Certain features do not behave as desired after the update
If the UTM does not work as desired after the update, a rollback can be performed.
If proper operation has not yet been confirmed, proceed as described above.
Otherwise under in the section
notempty
A new version is not downloaded automatically
- A valid license is required.
- The time of the system must not deviate too much.
- The update server is not accessible. e.g. due to a too large packet size (MTU), this must be adjusted if necessary.
- The automatic update process is distributed over a certain period of time for load distribution (see Changelog): Planned rollout period.
- Update does not load and the following error message can be seen in the log:
2023-01-09T09:51:17.302+01:00|spupdater|22223|downloading do-update.sh: failed
Additionally, the configuration cannot be saved or a new configuration cannot be created.
Solution:- Check storage space
- Check the writability of the partition/hard disk.
Check availability of the support server
The following command can be executed from the root shell
root@fw:~# curl update-001.v12.utm.spnoc.de
| Result | Description |
|---|---|
| curl: (6) Could not resolve host: update-001.v12.utm.spnoc.de | DNS problem |
| curl: (7) Error | Failed to connect() to host or proxy TCP Verbindung schlägt Fehl. Falsche Route, Verbindung wird durch eine andere Firewall blockiert o.ä. |