notempty
12.6.2
- 12.7.1
1 -
| |||
| [[Datei: ]] 1 | |||
2 -
| |||
| Name: | IPSec Roadwarrior | [[Datei: ]] | |
| |||
– IKEv1 3 - - IKEv1
| |||
| Local Gateway ID: | [[Datei: ]] | ||
|
|
|||
| X.509 : ' |
|||
| Privater RSA-Schlüssel: | |||
| |||
– IKEv2 3 - - IKEv2
| |||
| Local Gateway ID: | [[Datei: ]] | ||
| ' | |||
| X.509 : ' |
|||
| |||
| |||
– IKEv1 4 - - IKEv1
| |||
' |
[[Datei: ]] | ||
| Remote Gateway ID: ' |
192.0.2.192 |
| |
' |
»192.168.22.35/24 | ||
' |
|||
' |
192.168.222.35 | ||
– IKEv2 4 - - IKEv2
| |||
' |
[[Datei: ]] | ||
| 192.168.22.35/24 | |||
' |
|||
| X.509 : ' |
|||
| |||
[[Datei: ]] [[Datei: ]] | |||
|
| |||
| [[Datei: ]] | |||
| Name: | ngrp-IPSec-Roadwarrior | ||
| |||
| |||
| Zone: | vpn-ipsec | ||
| |||
IKEv1
| 1. | 2. | 3. |
| Abb.1 | Abb.2 | Abb.3 |
| Abbildungen | ||
Phase 1 | ||||||
| | ||||||
| [[Datei: ]] | [[Datei: ]] | [[Datei: ]] | [[Datei: ]] | |||
| ||||||
| ||||||
| ||||||
| Dead Peer Detection: | ||||||
| DPD Timeout: | 30 | |||||
| ||||||
| Compression: | ||||||
IKE IKE | ||||||
| Default UTM | Default NCP Client | [[Datei: ]] |
[[Datei: ]] | |||
| »aes128 | AES 128 Bit | |||||
| »sha2_256 | Hash: SHA2 256 Bit | |||||
| »ecp521 | IKE DH-Gruppe: DH2 (modp1024) | |||||
| Aktuelle Kombinationen: | aes128-sha2_256-ecp521 | |||||
| IKE : | ||||||
| Strict: | ||||||
| 3 | ||||||
| IKE Rekeytime: | 2 | |||||
| notempty ike_lifetime = 2 ike_rekeytime = 0 ike_lifetime = 0 ike_rekeytime = 2 ---- ike_lifetime = 2 ike_rekeytime = 1 ike_lifetime =2 ike_rekeytime = 1 | ||||||
| Rekeying: | ||||||
Phase 2 | ||||||
|
| ||||||
| Default UTM | Default NCP Client | [[Datei: ]] / IKEv1 / Roadwarrior | [[Datei: ]] / IKEv2 / Roadwarrior | [[Datei: ]] / IKEv1 / S2S | [[Datei: ]] / IKEv2 / S2S | |
| »aes128 | AES 128 Bit | |||||
| »sha2_256 | SHA2 256 Bit | |||||
| »ecp521 | IKE DH-Gruppe: DH2 (modp1024) | |||||
| »ecp521 | IKE DH-Gruppe: DH2 (modp1024) | |||||
| Aktuelle Kombinationen: | aes128-sha2_256-ecp521 | |||||
| ||||||
| ||||||
| ||||||
| DHCP: | ||||||
| [[Datei: ]] | |||
| |||
| 192.168.22.35/24 | |||
| '
|
[[Datei: ]] | ||
| '
|
[[Datei: ]] | ||
Troubleshooting
IKEv2
| 1. | 2. | 3. |
| Abb.1 | Abb.2 | Abb.3 |
| Abbildungen | ||
Phase 1 | ||||||
| | ||||||
| [[Datei: ]] | [[Datei: ]] | [[Datei: ]] | [[Datei: ]] | |||
| ||||||
| ||||||
| ||||||
| Dead Peer Detection: | ||||||
| DPD Timeout: | 30 | |||||
| ||||||
| Compression: | ||||||
IKE IKE | ||||||
| Default UTM | Default NCP Client | [[Datei: ]] |
[[Datei: ]] | |||
| »aes128 | AES 128 Bit | |||||
| »sha2_256 | Hash: SHA2 256 Bit | |||||
| »ecp521 | IKE DH-Gruppe: DH2 (modp1024) | |||||
| Aktuelle Kombinationen: | aes128-sha2_256-ecp521 | |||||
| IKE : | ||||||
| Strict: | ||||||
| 3 | ||||||
| IKE Rekeytime: | 2 | |||||
| notempty ike_lifetime = 2 ike_rekeytime = 0 ike_lifetime = 0 ike_rekeytime = 2 ---- ike_lifetime = 2 ike_rekeytime = 1 ike_lifetime =2 ike_rekeytime = 1 | ||||||
| Rekeying: | ||||||
Phase 2 | ||||||
|
| ||||||
| Default UTM | Default NCP Client | [[Datei: ]] / IKEv1 / Roadwarrior | [[Datei: ]] / IKEv2 / Roadwarrior | [[Datei: ]] / IKEv1 / S2S | [[Datei: ]] / IKEv2 / S2S | |
| »aes128 | AES 128 Bit | |||||
| »sha2_256 | SHA2 256 Bit | |||||
| »ecp521 | IKE DH-Gruppe: DH2 (modp1024) | |||||
| »ecp521 | IKE DH-Gruppe: DH2 (modp1024) | |||||
| Aktuelle Kombinationen: | aes128-sha2_256-ecp521 | |||||
| ||||||
| ||||||
| ||||||
| DHCP: | ||||||
| [[Datei: ]] | |||
| |||
| 192.168.22.35/24 | |||
| '
|
[[Datei: ]] | ||
| '
|
[[Datei: ]] | ||
Troubleshooting
'
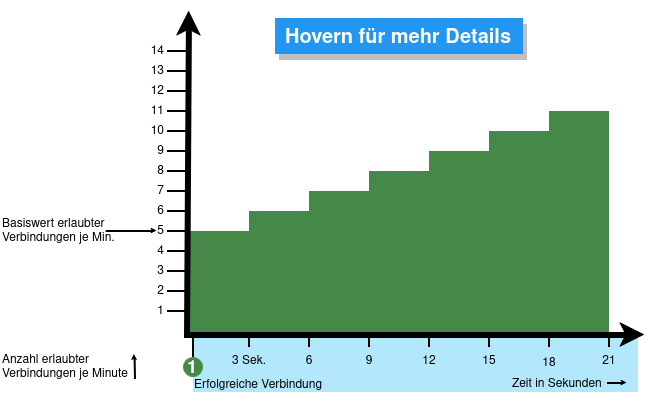
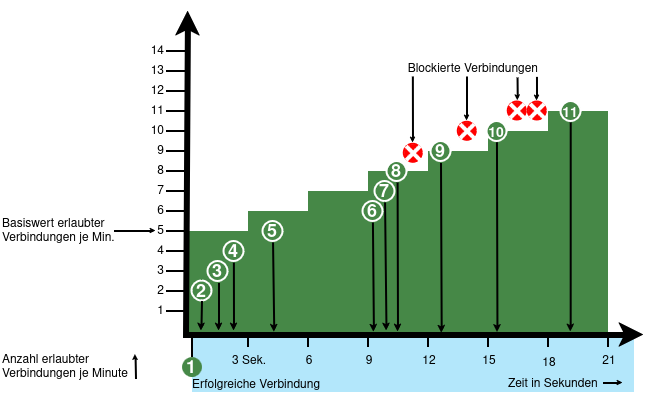
| extc-Variable | Default | |
|---|---|---|
| CONNECTION_RATE_LIMIT_TCP | 0 | |
| CONNECTION_RATE_LIMIT_TCP_PORTS | ||
| CONNECTION_RATE_LIMIT_UDP | 20 / 0 |
|
| CONNECTION_RATE_LIMIT_UDP_PORTS | [ 1194 1195 ] |
| extc value get application securepoint_firewall spcli extc value get application securepoint_firewall | grep RATE |
application |variable |value --------------------+-------------------------------+----- securepoint_firewall |… |… |CONNECTION_RATE_LIMIT_TCP |0 |CONNECTION_RATE_LIMIT_TCP_PORTS| |CONNECTION_RATE_LIMIT_UDP |20 |CONNECTION_RATE_LIMIT_UDP_PORTS| |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 20 system update rule |
|
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 0 system update rule |
|
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP_PORTS value [ 443 11115 ] system update rule |
|
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP_PORTS value [ ] system update rule |
|
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP value 20 system update rule |
|
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP value 0 system update rule |
|
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP_PORTS value [ 1194 1195 ] system update rule |
|
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP_PORTS value [ ] system update rule |
|
extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 20 |


