Last adaptation to the version: 14.0.0 (11.2024)
- Automatic generation of OTP codes has been optimized
notemptyThis article refers to a Beta version
Preliminary remarks
If the OTP method is activated, login is only possible by entering a correct OTP.
notemptyIf the OTP method is active for the admin web interface and SSH console, each administrator must have this token to access the device. Exception on user basis is not possible!
SSL-VPN:
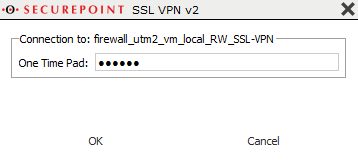
Since SSL VPN re-authenticates every hour, a new OTP must also be entered every hour.
Renegotiation can be increased or completely disabled in the menu in the settings of a connection in the General tab under Renegotiation.
Of course, disabling is not recommended. A change is transmitted by the UTM to the SSL VPN clients.
Saving the password in the SSL VPN client is not possible because the password that is passed is composed of the static user password and the OTP.
In case of malfunction of the OTP generator (smartphone or hardware token), the OTP can only be generated if there is access to the QR code or the secret code.
This can be found under .
notemptyIf the OTP generator for administrator access fails, a printed version of the QR code is required.
If this is not available, access to the UTM is only possible with physical access directly at the device (keyboard and monitor at the UTM).
Printout of this code for the administrators as described in OTP Secret. File in the documentation.
The time of the UTM system can be checked in three ways:
- Using the CLI with the command system date get
- Using the root console with the command date
The system time can then be set using the following options:
- Using the administration web interface in the menu Area Time settings
- Using the CLI with the command system date set date then seperated with spaces the current date and time in the format YYYY-MM-DD hh:mm:ss
OTP - One-Time-Password
The one-time password is an additional authentication mechanism that provides extra security when a user logs in. The UTM uses the time-based method (TOTP: Time-based One Time Password). This calculates a new OTP every 30 seconds from the shared secret code and the current time. There are several ways to generate this six-digit password:
- Smartphone app: A smartphone app can be used to calculate the password. For example, Google Authenticator, which is available for authenticator2 Android and iOS, or other apps such as FreeOTP+ for Android, which may even offer a wider range of features such as token export, better hash algorithms, etc.
- Password manager for PC: A password manager for PC that can generate OTPs can be used, e.g., KeepassXC.
- Hardware tokens: There are hardware tokens that are solely responsible for generating OTPs.
Set up OTP
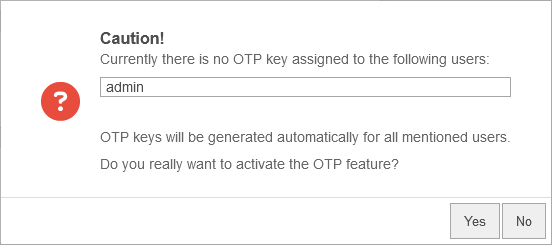
Activation procedure
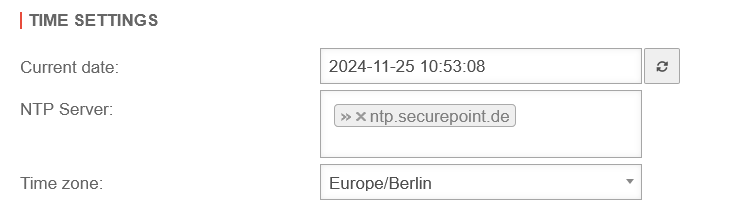
- Ensure that the time of the UTM and the token are synchronized The exact time of the UTM is displayed under Area Server Settings section
Time Settings {{{2}}}
Configure OTP User
First, the users are created under as usual.
See also User management.
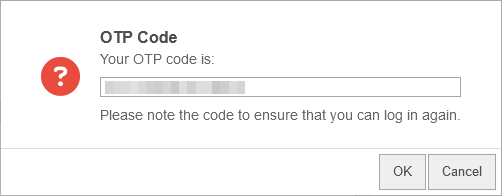
The OTP code for this user can only be displayed after the user's entries have been saved.
Display or change by clicking on the edit button in the user row in the tab OTP on the right side.
The code can be created automatically by the Securepoint UTM and is available in two formats.
On the one hand as a QR code, which can simply be photographed with the smartphone app, and on the other hand in text form to be entered using the keyboard.
OTP Configuration
| |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnAuthenticationUser 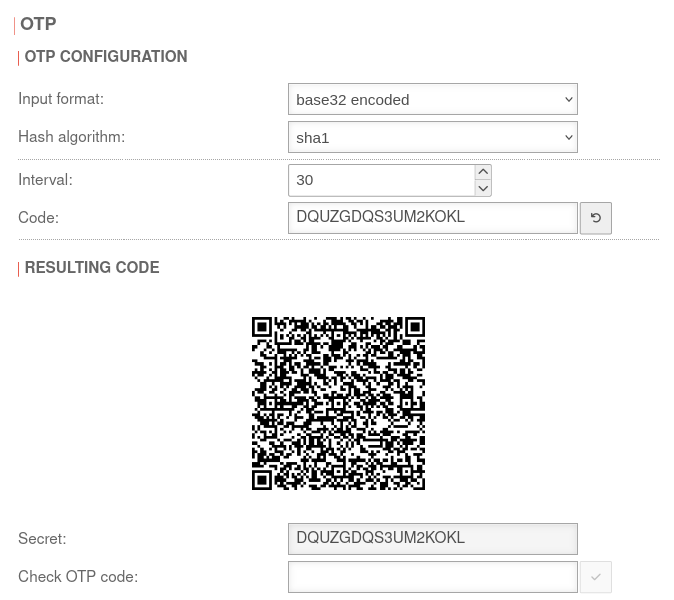 OTP user OTP user
|
|---|---|---|---|
| Input format: | Default setting, base32 encoded, 16 characters length Codes less than 26 characters in length may be flagged as insecure by OTP apps | ||
| base64 encoded, length 16 - 168 characters (in blocks of 4), manual input | |||
| HEX coded, valid characters: A-F, a-f and 0-9 / length 10-128 pairs, manual input | |||
| Hash algorithm: | Default |
The hash algorithm can be selected | |
| notemptyNot every authenticator app supports every hash algorithm! Some of these apps do not support sha256, or sha512. When using these apps, the default value may have to be retained. | |||
| Interval: | 30 | The interval should be set to 30 seconds If a hardware token is used, its value must be adopted. OTP apps are often optimized to update the token every 30 seconds. | |
| Code: | DQUZGDQS3UM2KOKL | Gives the code in text form. It is also possible to enter a code manually, e.g. a hardware token. | |
| Creates a new code with the default settings (base32 coded, interval 30 seconds) | |||
Resulting Code
| |||
| Secret: | Gives the code in text format | ||
| Check OTP code: | An OTP code generated with a corresponding OTP generator can be entered here to check whether the OTP generator has been set up correctly. | ||
OTP Secret
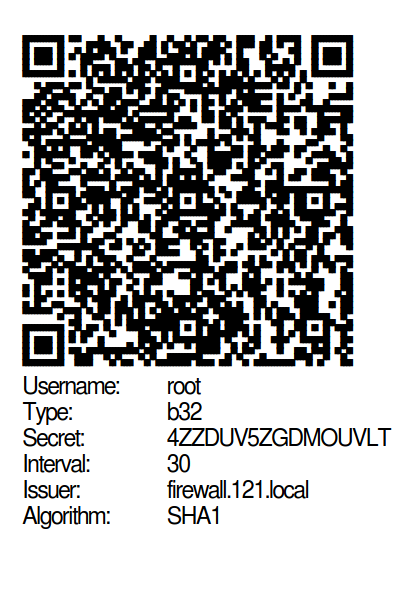
For distribution to the users there is a possibility to print the created codes.
A document in PDF format will then be generated as follows:
Setting up an Authenticator
Use of a hardware token
The use of a hardware token is also possible.
This should be a RFC 6238 compatible password generator.
Securepoint currently supports the Feitian OTP c200.
A download link for the HEX code is sent by the supplier for this purpose, which must be registered with the user as described above.
The following parameters must be used:
- SHA algorithm: SHA1
- Time interval: 30 seconds
- Optional: SEED programming Background on SEED programming: In case the token happens to be created in in non-trustworthy countries and you want to make sure that it does not already contain malicious code or is otherwise compromised upon delivery, i.e. Mtrix will reprogram it for a small amount.
notemptyBe sure to enter the token key and not the token ID.
The ID is a serial number of the token and the key is a 32 to 40 character code.
notemptyAttention: The OTP seed can be read by LDAP if it is stored in the user attributes in AD.
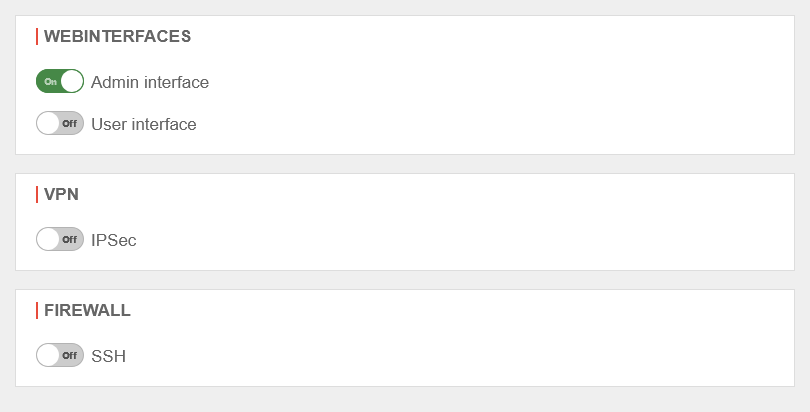
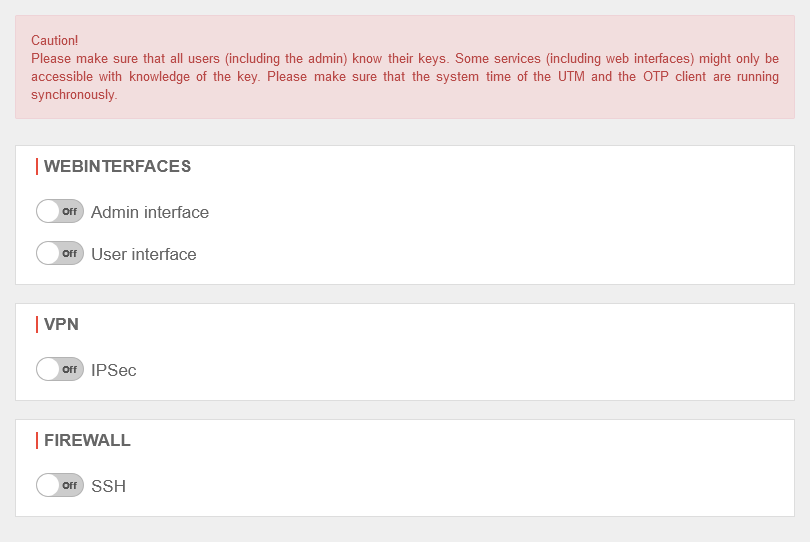
Assign OTP to applications
Under one can select for which applications the users should additionally authenticate themselves with the one-time password.
Use OTP
Webinterface
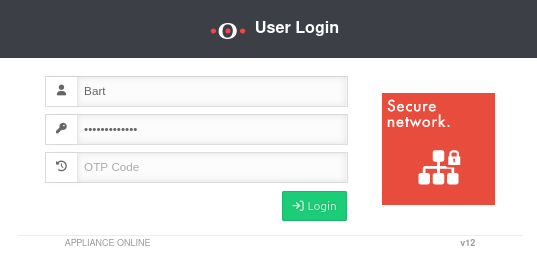
When logging in to the administration or user web interface, there is now an additional authentication field for the OT code.
Here, in addition to the user name and password, the generated code is entered.
VPN
In the SSL-VPN Client, you can set whether the OTP code is to be requested separately. A more detailed explanation can be found
here.
If the remote terminal allows a separate transmission of the OTP password, the following procedure can be followed:
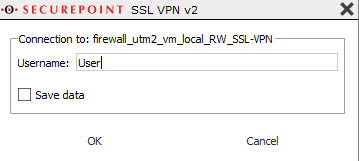
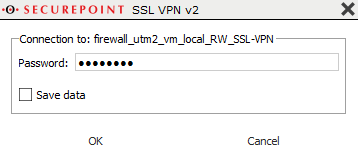
Start the SSL VPN connection on the client (on Windows: double-click the lock icon in the taskbar).
Establish the connection by clicking on ![]() The connection is established in three steps:
The connection is established in three steps:
notemptyScenario: Remote terminal does not allow separate transmission of the OTP code:
Example:
| Password: | insecure | Saving the password in the SSL VPN client is not possible because the password that is passed is composed of the static user password and the alwys changing OTP. |
| OTP: | 123456 | |
| password: | insecure123456 |
SSH connection
If access is used with an SSH console and OTP, the OTP code is requested in a separate row Pin.
notemptyVPN with UTM if the remote station does not allow separate transmission of the OTP password:
When accessing with an SSH console and OTP, and the counterpart does not allow separate transmission of the OTP code, the OTP code is entered without spaces directly after the user password.
Example
| Password in UTM: | insecure |
| OTP: | 123456 |
| Password: | insecure123456 |