Last adaptation to the version: Portal v1.30 (09.2024) / UTM v12.5.2 (10.2023)
- Layout slightly adapted
- It is possible to memorise the PIN for the current session
- 06.2025
- Arrangement of the web session adapted
- All versions older than v12.5.1 are classified as significantly outdated. 02.2025
- Note on VPN configurations with an upcoming portal version 02.2025
Requirements
USC after update
The Unified Security Console must be enabled in the UTM
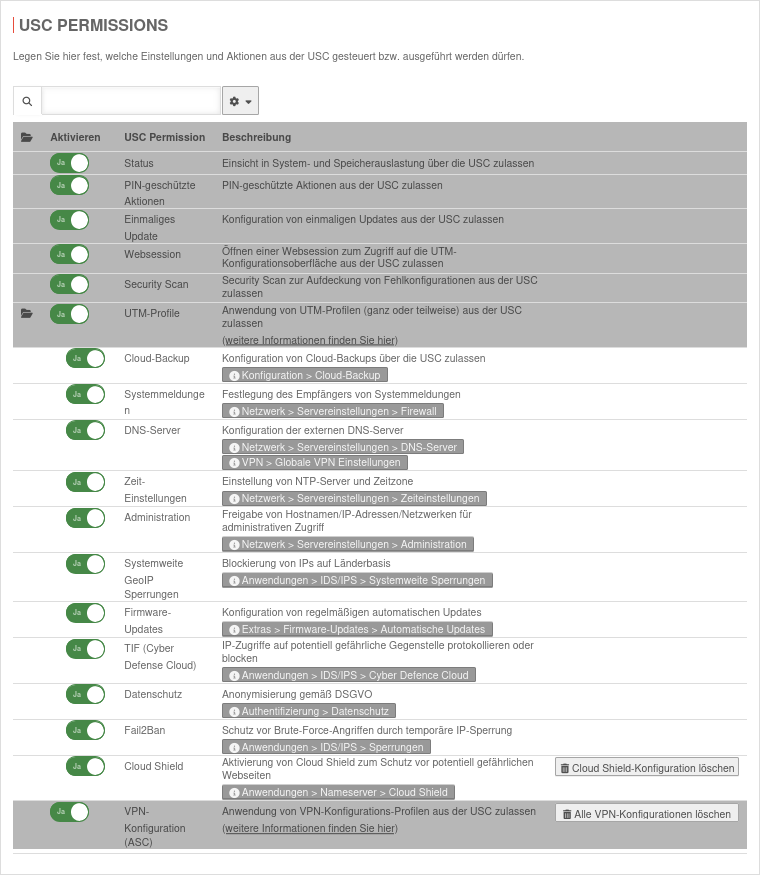
UTM Settings and permissions for the Unified Security Report
| The Unified Security Report provides a good overview of battery devices directly on the Unified Security Portal. For a UTM to be included there, the function must be activated on the UTM. To activate the Unified Security Report on a UTM, the USR must first be activated for the selected license. More information can be found in the Article on the Unified Security Reporting | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdn 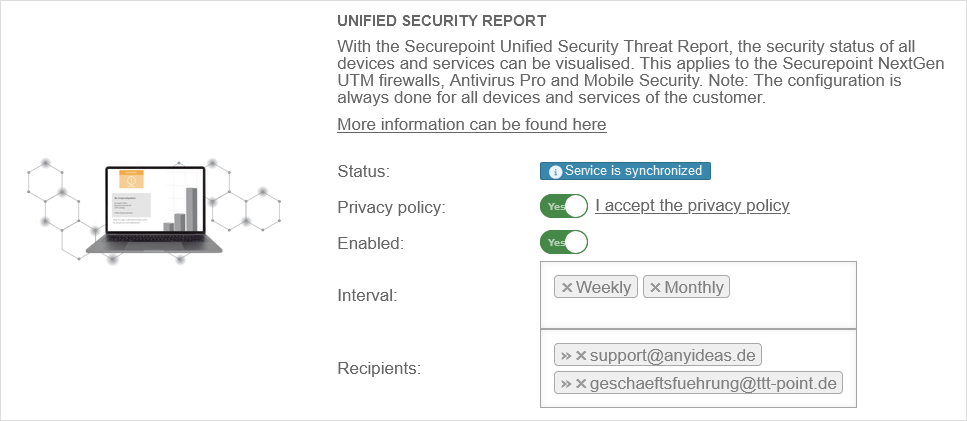
|
|---|---|---|---|
| Status: | Service is synchronized | Synchronization status with the Unified Security Portal | |
| Privacy policy: | Yes | Consent to the privacy policy of Unified Security Reports | |
| Activated: | Yes | Activating the connection to the Unified Security Portal | |
| Interval: | WeeklyMonthly | Interval at which emails are sent in the report and thus also the reporting period in each case | |
| Recipient: | »support@anyideas.de»geschaeftsfuehrung@ttt-point.de | Email address for reports | |
Settings and authorizations of the UTM for the Unified Security Console
|
notempty Note for cluster licenses In order for both cluster members to be assigned to each other, special new licenses must be registered on both devices. Menu Button To do this, two licenses must be downloaded from the reseller portal. If no license is marked as xynnnnn-SPARE in the reseller portal (matching licenses have an identical color marking on the left side of the table), please send an email to lizenzen@securepoint.de with customer name, customer number and the serial numbers of the devices or, in the case of VMs, with the license ID. Access by then Unified Security Console must first be enabled in the UTM itself in the menu . Attention: It usually takes a few minutes, in unfavorable cases up to an hour, before the menu is displayed for the first time. The process can be shortened by executing the command on the CLI after a few minutes of runtime (the UTM must have had the opportunity to report to the license server!). system restrictions update |
UTMuser@firewall.name.fqdn 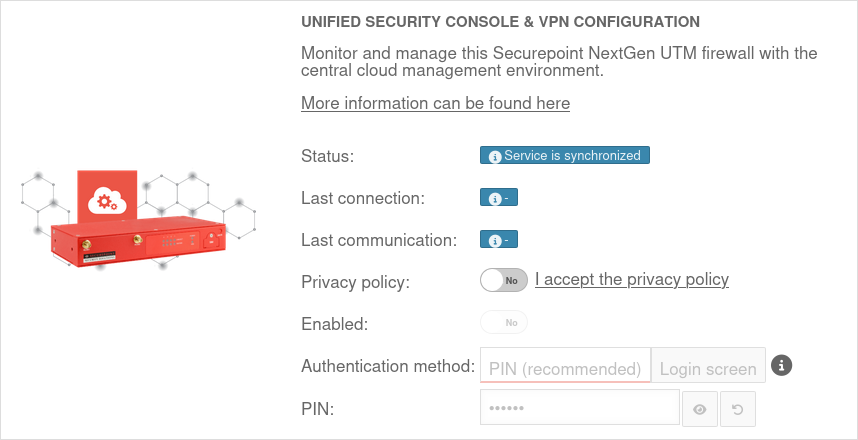
| ||
| Caption | Value | Description | 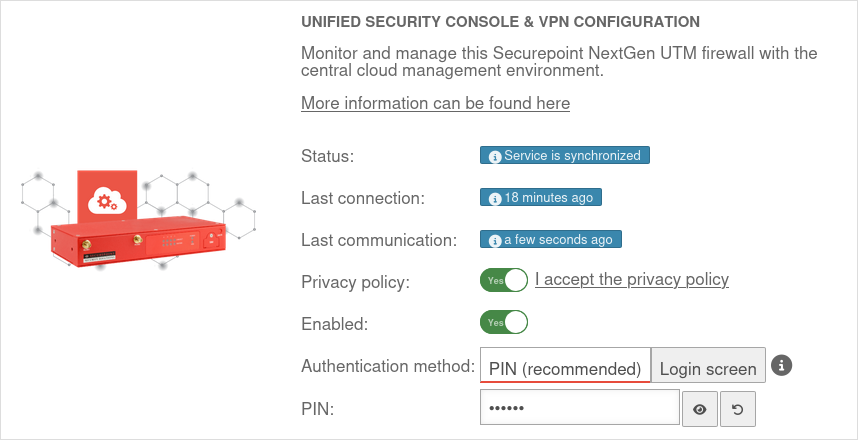 |
|---|---|---|---|
| Privacy Policy: | Yes | The privacy policy must be accepted | |
| Activated: | Yes | This activates the Unified Security Console - and thus the display, configuration and access via the Securepoint Unified Security portal. | |
| Authentication method: | Authentication method for a web session | ||
| PIN: | •••••••• | As authentication for a web session, a 6-digit PIN can be selected instead of the login mask with access data.
| |
| Displays the Websession PIN | |||
| Creates a new PIN | |||
| The entered PIN is incorrect | After 5 (default value value can be changed in the CLI with the extc variable SESSIONAUTH_MAXRETRY extc value set application ‘spcloudpuppet’ variable ‘SESSIONAUTH_MAXRETRY’ value ‘5’ The PIN can be unblocked again when logging in to the UTM itself. | ||
Actions that can only be executed with a PIN:
| |||
Detailed authorizations
IP address
- UTM up to v.12.2.2.8: Update required
The UTM uses an older procedure for the Websession, which is only available until 30.11.2023- The UTM is directly accessible via a local network
- Access data (user name and password) are required
or - The UTM has a public IP If no public IPv4 is available because the UTM is behind a NAT router, a public IPv6 can be assigned via IPv6 prefix delegation.
- UTM up to v12.4.4.1 An update to the latest version is recommended
- The UTM is directly accessible via a local network
- Access data (user name and password) are required
or - The UTM has a public IP If no public IPv4 is available because the UTM is behind a NAT router, a public IPv6 can be assigned via IPv6 prefix delegation.
- UTM v12.5.0
- The UTM is directly accessible via a local network
- Access data (user name and password) are required
or - The UTM has a public IP If no public IPv4 is available because the UTM is behind a NAT router, a public IPv6 can be assigned via IPv6 prefix delegation.
- A PIN is additionally required Deposited on the UTM in the menu USC / box Unified Security Console
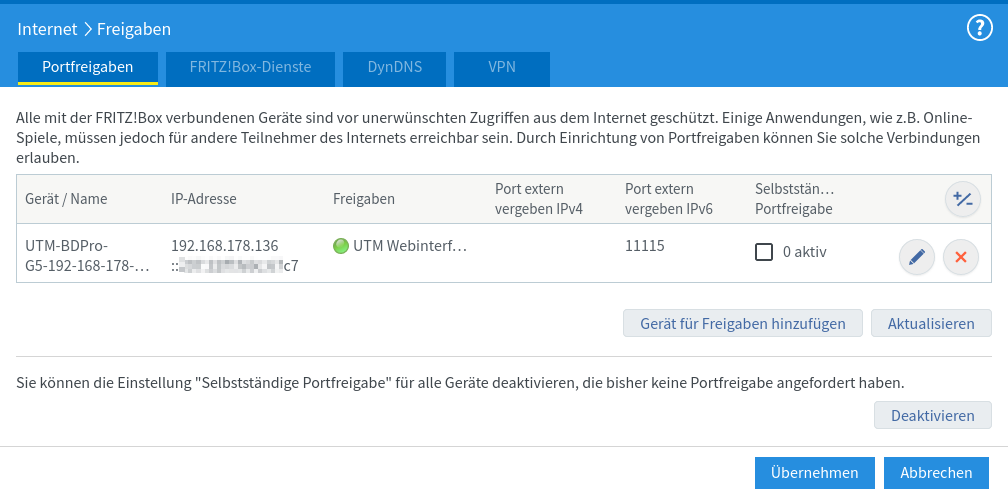
Example configuration with a Fritzbox
This section includes descriptions of third-party software and is based on the status at the time this page was created.
Changes to the user interface on the part of the manufacturer are possible at any time and must be taken into account accordingly in the implementation.
All information without warranty.
- Login to the configuration interface (in the default settings at https://192.168.178.1)
- In the network settings for IPv6, the option Enable DHCPv6 server in FRITZ!Box for home network must be selected
- Select suboption Assign DNS server, prefix (IA_PD) and IPv6 address (IA_NA)
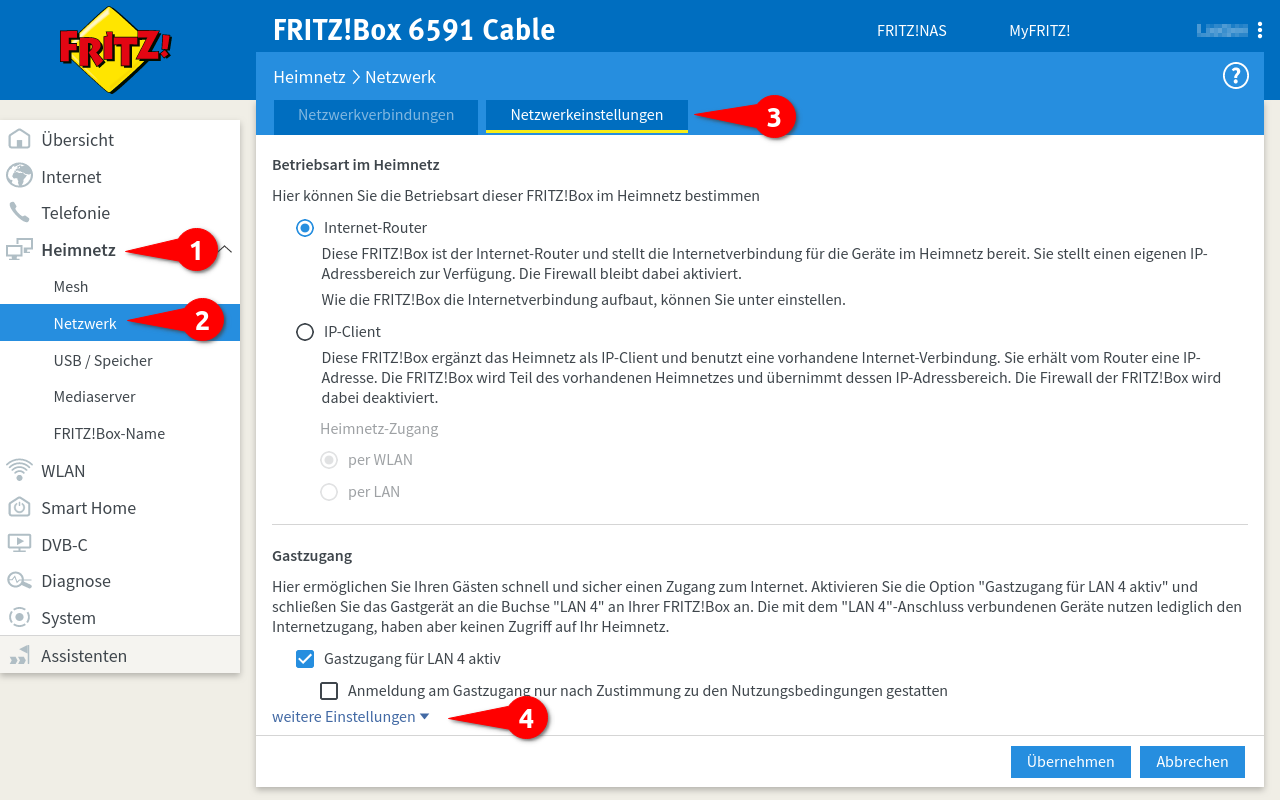
- Menu Home network ➊ / Network ➋ / Tab Network settings ➍
- at the bottom of the page dropdown menu: More Settings ➍
- Section IP addresses / Button IPv6 settings ➎ (not in picture)
or also IPv6 configuration
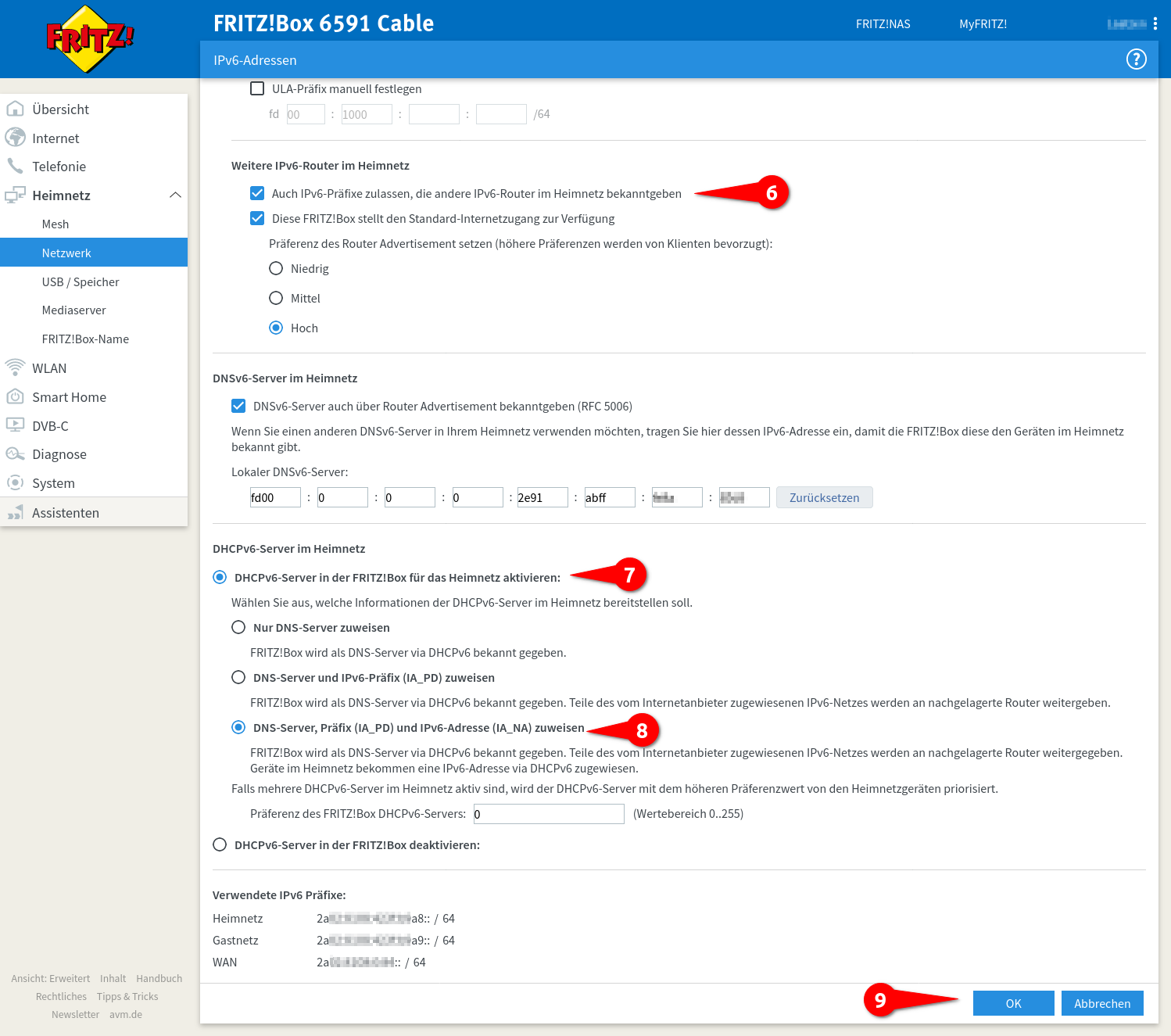
Also allow IPv6 prefixes to be advertised by other IPv6 routers on the home network ➏
Enable DHCPv6 server in FRITZ!Box for the home network: ➐
- Activate Assign DNS server, prefix (IA_PD) and IPv6 address (IA_NA). ➑
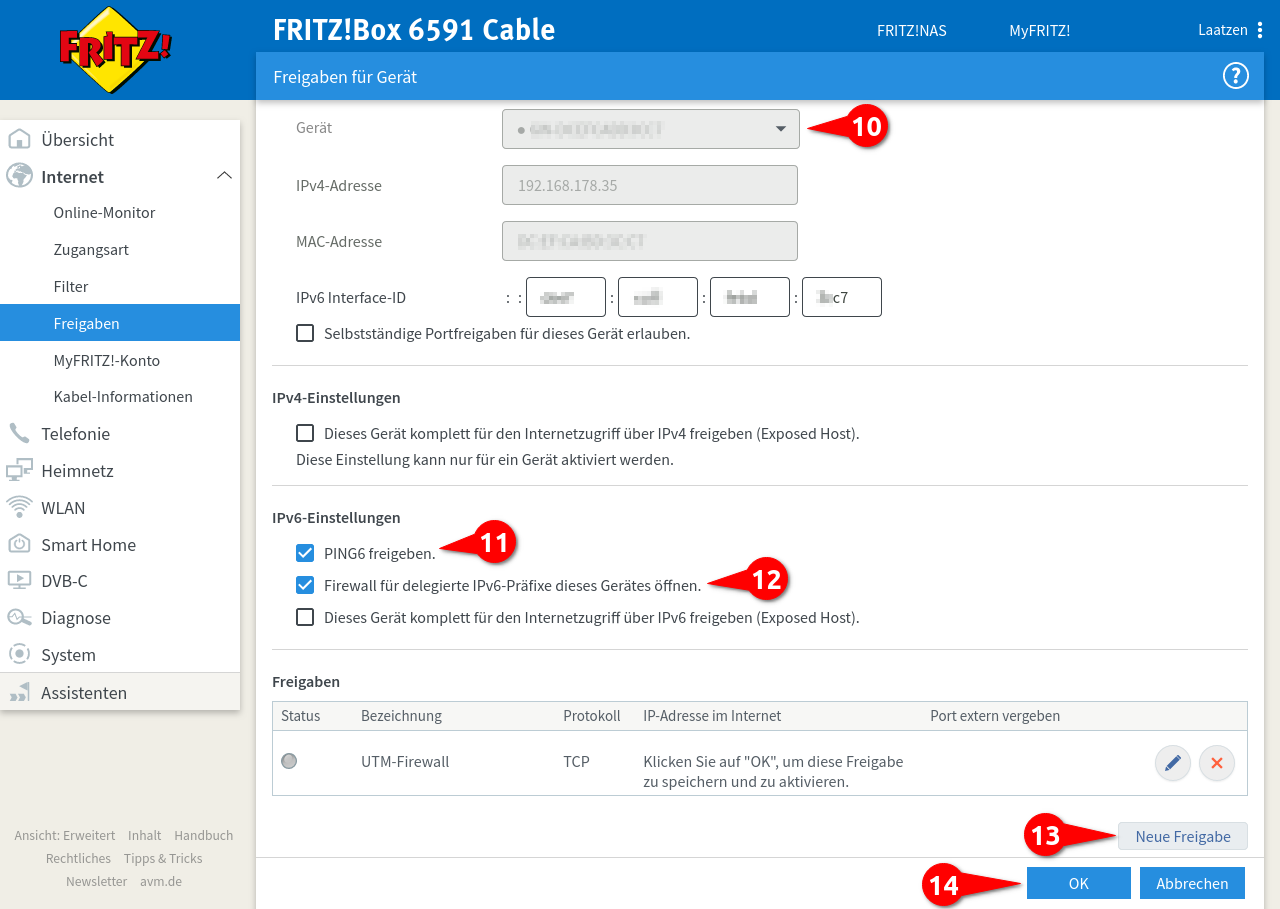
Menu
Select 'Enter IP address manually' if it is not assigned via DHCP
Another dialog opens
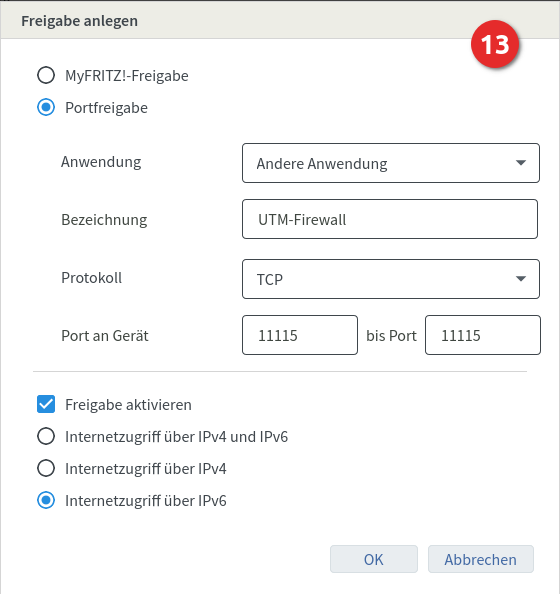
Adjust port if necessary under Area Server Settings section web server Administration Web Interface Port: a different port has been configured.
Internet access via IPv6 option
Configuration on the UTM:
Edit interfaces
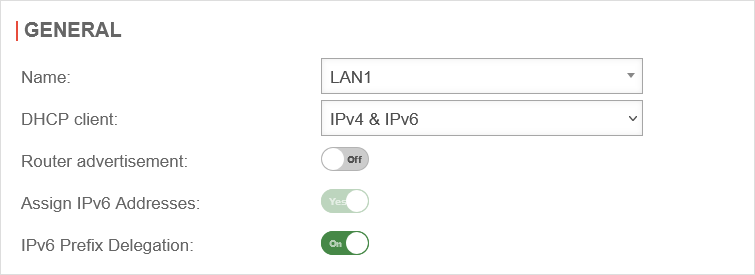
connected to the Internet via NAT router
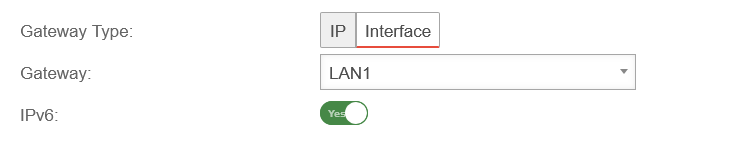
Menu Area Network Interfaces / Edit External Interface / Tab General
DHCP Client
Router Advertisement: Off
IPv6 Prefix Delegation On
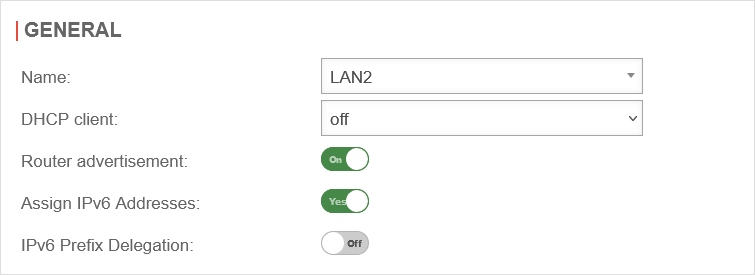
(must be configured for all internal interfaces that are to distribute a public IPv6 address to clients (and thus also receive one themselves).
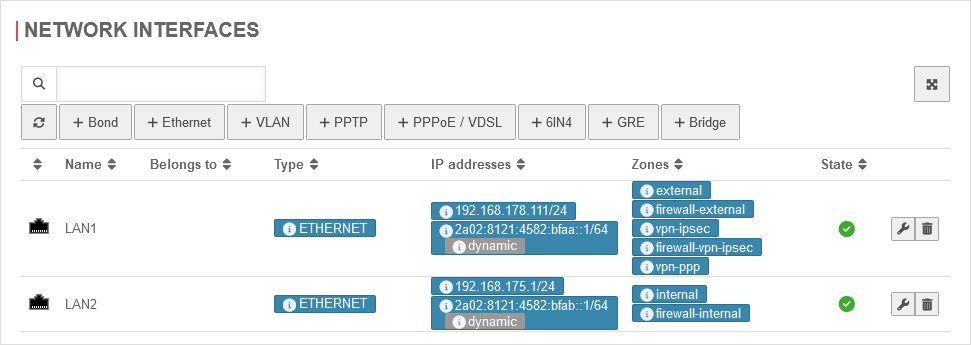
Menu Area Network Interfaces / Edit Internal Interface / Tab General
DHCP Client
Router Advertisement: On
IPv6-Adressen vergeben: Ja
IPv6 Prefix Delegation: Off
Create network objects and packet filter rules
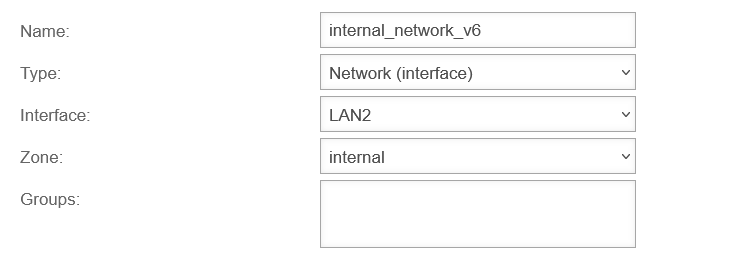
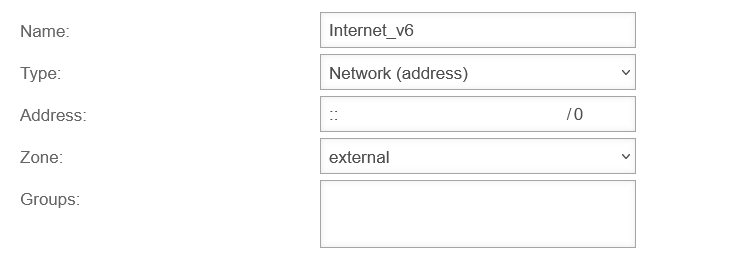
Name: internal_network_v6
Type:
Adresse:
Zone:
After a few minutes, this address is displayed in the selection box for IP addresses in the USC.
- UTM from v.12.5.1:
- The UTM is directly accessible via a local network
- Access data (user name and password) are required
or - A Websession from remote networks is also possible if the UTM does not have a public IP
- The connection is established via the interface on which the default route of the UTM is set up.
- Login with PIN or access data possible Deposited on the UTM in the menu USC / box Unified Security Console
Websession
| Action: | Description | 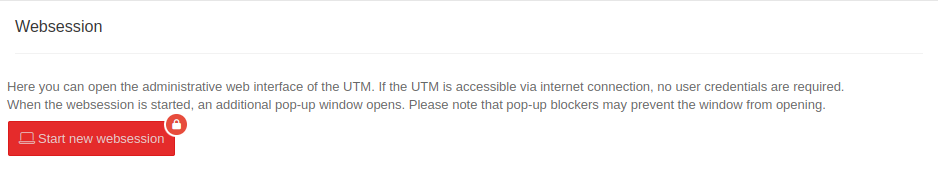
| |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
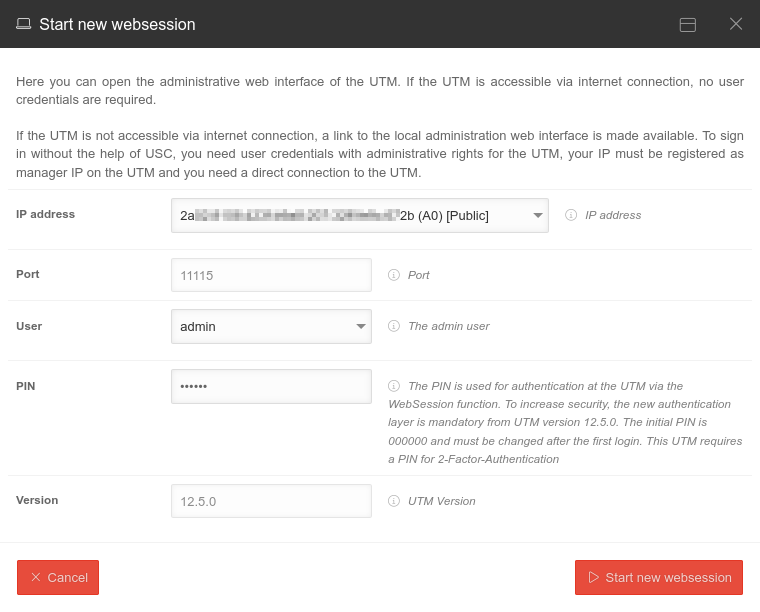
| Start new websession | Opens the dialog to start the administrative web interface of the UTM | ||||||||||||||
Websession with PINnotemptyWebsession with PIN (UTM from v12.5.1) | |||||||||||||||
| admin | If there is no user with the name admin, a user with admin rights can be selected here with whom the Websession connection is to be started. | 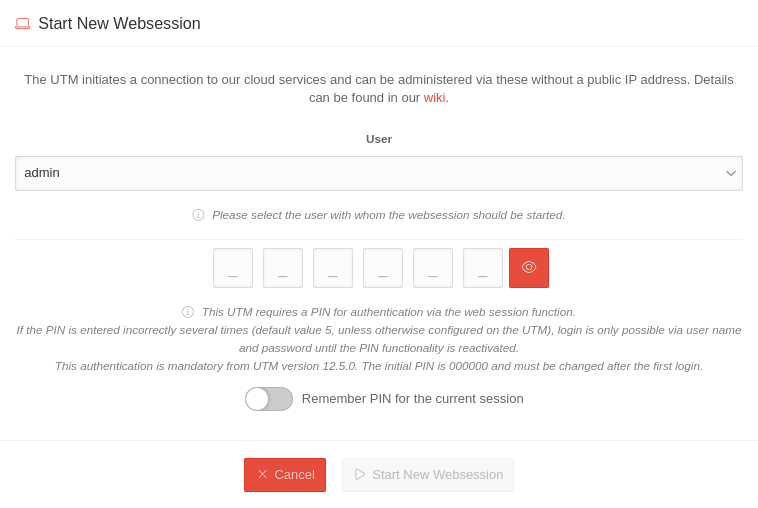 | |||||||||||||
| _ _ _ _ _ _ | Websession PIN (Configured on the UTM in the menu in the Unified Security Console section After entering the PIN, the Websession can be started directly using ↵ Enter. | ||||||||||||||
| notempty New as of: 1.27 | |||||||||||||||
| Remember PIN for the current session notempty New as of 1.30 |
In this dialogue window it is possible to remember the PIN for this session. If this is activated , the PIN is automatically entered in other dialogues and the slider is no longer displayed. If the PIN is entered incorrectly, it will not be saved. | ||||||||||||||
| The entered PIN is incorrect | After 5 (default value value can be changed in the CLI with the extc variable SESSIONAUTH_MAXRETRY extc value set application ‘spcloudpuppet’ variable ‘SESSIONAUTH_MAXRETRY’ value ‘5’ The PIN can be unblocked again when logging in to the UTM itself. | ||||||||||||||
| Start new websession | Opens the admin interface of the UTM in a new tab of the used browser | ||||||||||||||
Websession with login screennotemptyWebsession with login screen (UTM from v12.5.1) | |||||||||||||||
| The connection is established via the interface on which the default route of the UTM is set up. | 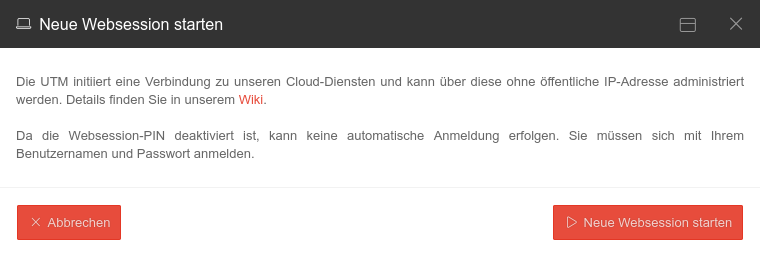 | ||||||||||||||
| As the Websession PIN is deactivated, no automatic login can take place. Access data (user name and password) are required. | |||||||||||||||
| Start new websession | Opens the admin interface of the UTM in a new tab of the used browser | ||||||||||||||
Websession with UTM up to v12.5.0notempty An update to the latest version is recommended
| |||||||||||||||