Last adaptation to the version: 14.0.1 (01.2025)
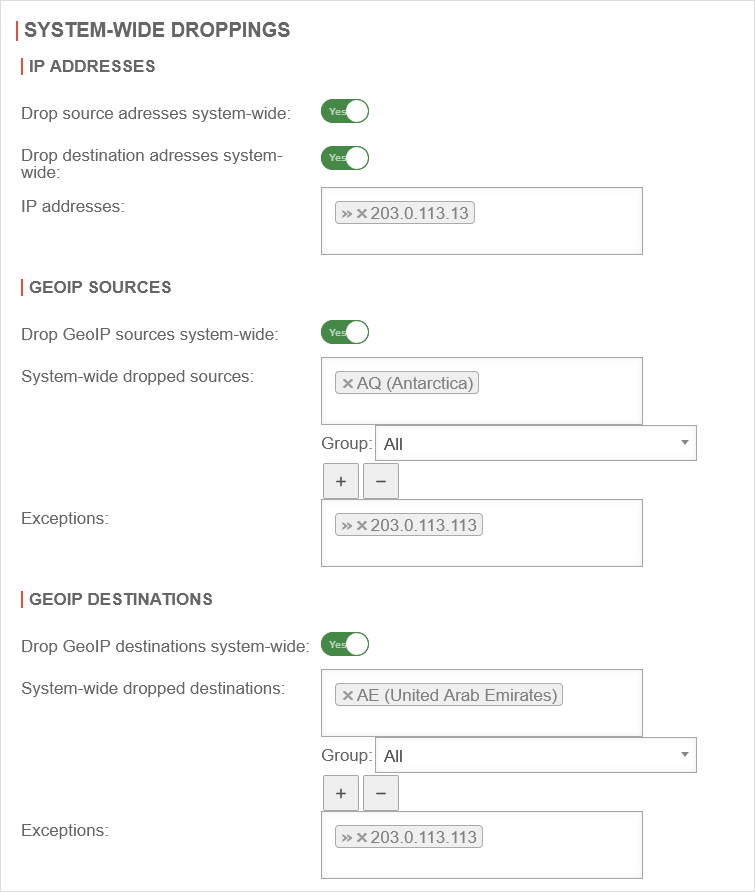
- System-wide blocks for IP addresses
- The GeoIP settings were moved to this area by the implicit rules
Preamble
IDS (Intrusion Detection System) and IPS (Intrusion Prevention System) can detect and prevent attacks from the Internet or a network.
These features are useful for stopping the server from flooding with malicious connection attempts.
Firewall monitoring
Activation of monitoring
The activation / deactivation of the monitoring is done in the menu in the group 'BlockChain'.
| On | BlockChain The monitoring for these accesses can be switched off. | ||
| Default | Rule | Description | |
|---|---|---|---|
| On | FailToBan_ssh | Access by ssh | |
| On | FailToBan_http_admin | Access via the Admin interface | |
| On | FailToBan_http_user | Access via the user interface | |
| On | FailToBan_smtp | Access via the mail gateway | |
Bans
Access to the firewall can be blocked after a certain number of incorrect login attempts.
The settings are configured in the menu.
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplication 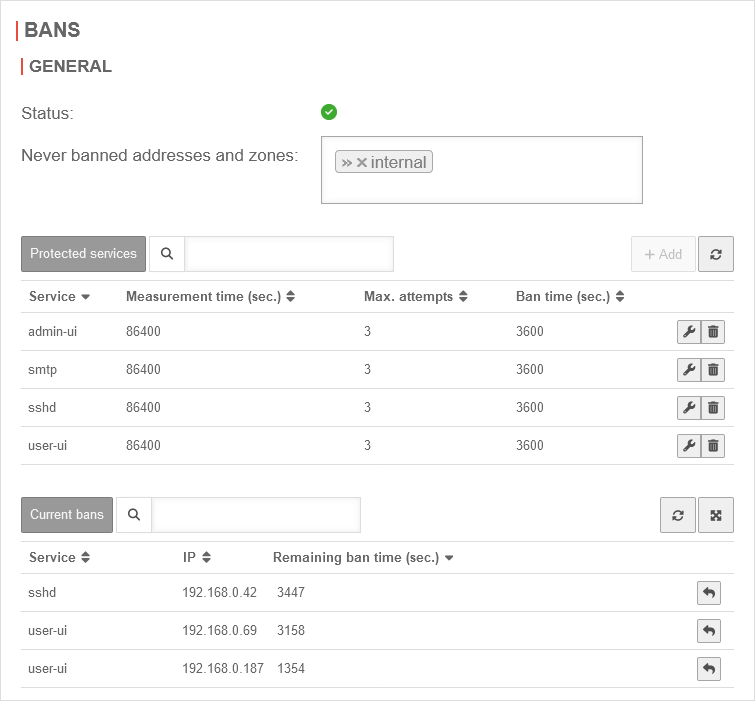 Tab IDS/IPS - Bans Tab IDS/IPS - Bans
|
|---|---|---|---|
| Status | The "IPS Locks" application is enabled. | ||
| The "IPS Locks" application is disabled. | |||
| Never blocked addresses and zones: | »internal | These IP addresses and zones, are not blocked by IDS/IPS. Examples: »internal »external_v6 »vpn-ipsec »192.0.2.192 | |
| Protected Services The following values can be configured : | |||
| Service | Service to be protected | ||
| Authentication via the admin interface. (default login port for administrators under 192.168.175.1:11115) | |||
| Authentication via the mail gateway | |||
| Authentication via ssh protocol (e.g. PuTTY) | |||
| Authentication via the user interface. Default login port for users under: 192.168.175.1:443 | |||
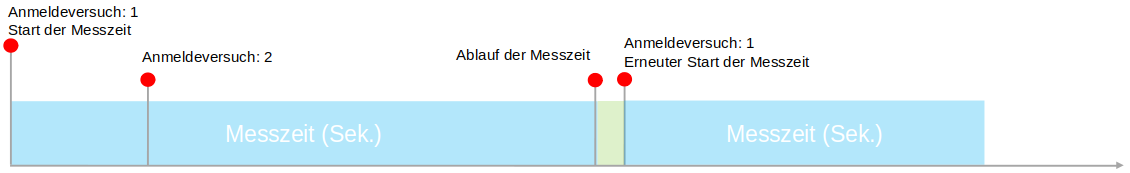
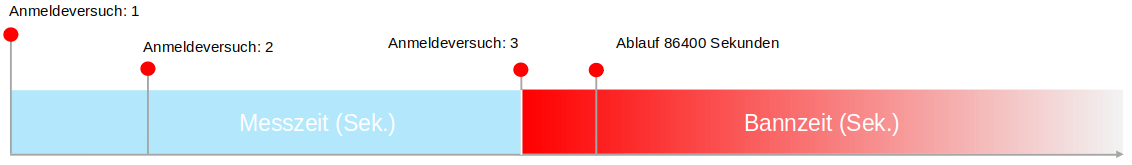
| measurement time | 86400 seconds | measurement time can be counted within the failed attempts. | |
| Max. attempts | 3 | Number of failed authentication attempts notempty Irrespective of this, after the 6th consecutive failed attempt, a flat-rate login throttling for the admin and user interface, as well as an error message in the respective web interface, takes effect New as of v12.7.0 | |
| Ban time | 3600 seconds | Period for which access to this authentication is blocked. | |
| Current ban The following blocks can be cancelled with . |
  | ||
| Service | The service for which the block is active | ||
| IP | The IP address that is blocked | ||
| Remaining ban time | The remaining time of the ban in seconds | ||
Releasing blocked accesses again
Under Current bans , blocked IP addresses can be released again for renewed access to a service before the ban time expires with the button .
Unlocking is also possible via the CLI:
utm.name.local> spf2bd ip remove service admin-ui ip 192.0.2.192
Here the ip {code
Notification of bans
In the Alerting Center you can set under IPS Lockouts whether and how you want to be notified about such lockouts.
Cyber Defence Cloud
| The Threat Intelligence Filter logs or blocks access to potentially dangerous remote peers based on the IP address, regardless of the protocol used. As soon as a connection is established to an IP address that is known, for example, as a control server for malware, the Threat Intelligence Filter detects this.
The filter updates itself automatically in the background via the Securepoint Cyber Defence Cloud. |
UTMuser@firewall.name.fqdnApplication  Cyber Defence Cloud Cyber Defence Cloud
|
| |
| notempty We strongly recommend to activate this option ! If a connection is blocked due to the Threat Intelligence Filter, a log entry is created. Notification of these log messages can be configured in Alerting Center. Default: Level 8 - Alarm → Message: Malicious connection detected. → Immediate Report & Regular Report | |
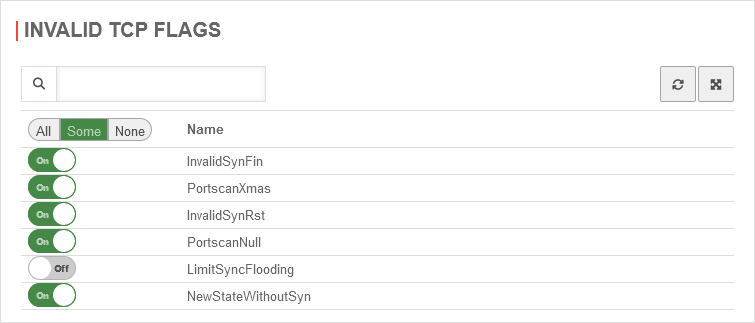
Invalid TCP Flags
Trojans
| To make it more difficult for trojans to penetrate and spread in the network, access to ports known to be used by some trojans can be blocked here. To do this, On closes all (header) or individual ports that are assigned to individual Trojans. In case of problems with other software that also uses such ports, only selected entries can be activated. notempty New as of v12.7.0 For comprehensive proactive protection, we recommend using the Thread Intelligence Filter, which blocks access based on known IP addresses. |
UTMuser@firewall.name.fqdnApplication  Trojans Trojans
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Blocked ports overview
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Connection Rate Limit
Throttling of access from certain source IPs to recurring ports
notempty
The function can initially only be configured via the CLI
SSL-VPN accesses can be protected against aggressive scans or login attempts, for example.
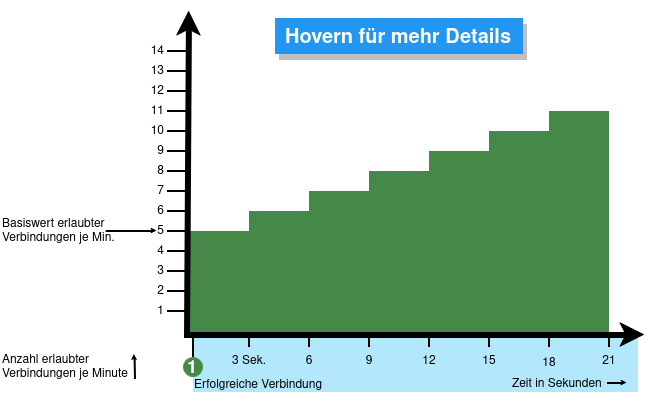
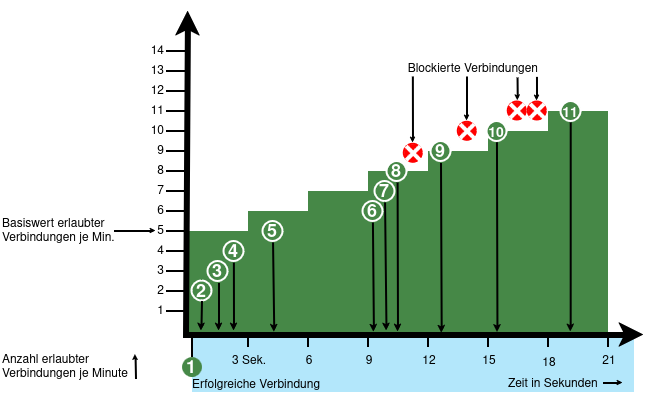
From v12.6.2, the UTM can limit the number of TCP and/or UDP connections from an external IP address to one port.
The following conditions apply:
- Only incoming connections for which a default route exists are monitored
- The connections from an IP address to a port of the UTM are counted within one minute
- When activated, 5 connections / connection attempts per minute are permitted.
The connections are then limited:- The additionally permitted connections are distributed evenly within 60 seconds of the first connection.
- With a CONNECTION_RATE_LIMIT value of 20, an additional connection is added every 3 seconds.
- 10 seconds after the first login, 3 further connections could be established (each from the same IP address to the same destination port)
- Blocking an IP address only affects access to the port that has been used too often.
Other ports can still be accessed.
- The function is activated by default for new installations on 20 UDP connections / minute on all ports
- For Updates the function must be manually activated
| extc-Variable | Default | Description |
|---|---|---|
| CONNECTION_RATE_LIMIT_TCP | 0 | Number of permitted TCP connections of an IP address per port 0 = Function deactivated, no blocking is performed |
| CONNECTION_RATE_LIMIT_TCP_PORTS | Ports to be monitored. Empty by default=all ports would be monitored (if activated). Individual ports are separated by spaces: [ 1194 1195 ] | |
| CONNECTION_RATE_LIMIT_UDP | 20 / 0 Default setting for new installations from v12.6.2: 20 For update installations the value is 0, so the function is deactivated. |
Number of permitted UDP connections of an IP address per port |
| CONNECTION_RATE_LIMIT_UDP_PORTS | Ports to be monitored. Empty by default=all ports are monitored (only for new installations!). Individual ports are separated by spaces: [ 1194 1195 ] |
Configuration with CLI commands
| CLI command | Function |
|---|---|
| extc value get application securepoint_firewall Alternatively as root user: spcli extc value get application securepoint_firewall | grep RATE |
Lists all variables of the securepoint_firewall application. The variables beginning with CONNECTION_RATE_LIMIT_ are responsible for the connection limit. application |variable |value --------------------+-------------------------------+----- securepoint_firewall |… |… |CONNECTION_RATE_LIMIT_TCP |0 |CONNECTION_RATE_LIMIT_TCP_PORTS| |CONNECTION_RATE_LIMIT_UDP |20 |CONNECTION_RATE_LIMIT_UDP_PORTS| |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 20 system update rule |
Limits the allowed number of TCP connections from a single IP address to a specific port to 20 per minute
A change is made directly by a rule update. The value must not be set to 0 first! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 0 system update rule |
Deactivates the monitoring of TCP connections |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP_PORTS value [ 443 11115 ] system update rule |
Restricts the monitoring of TCP connections to ports 443 and 11115 There must be spaces before and after the square brackets [ ]! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP_PORTS value [ ] system update rule |
There must be spaces before and after the square brackets [ ]! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP value 20 system update rule |
Limits the allowed number of UDP connections from a single IP address to a specific port to 20 per minute Default setting for new installations from v12.6.2: 20 For update installations the value is 0, so the function is deactivated. The value must not be set to 0 first! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP value 0 system update rule |
Deactivates the monitoring of UDP connections |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP_PORTS value [ 1194 1195 ] system update rule |
Restricts the monitoring of UDP connections to ports 1194 and 1195. (Example for 2 created SSL-VPN tunnels). There must be spaces before and after the square brackets [ ]! |
| extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_UDP_PORTS value [ ] system update rule |
There must be spaces before and after the square brackets [ ]! |
extc value set application securepoint_firewall variable CONNECTION_RATE_LIMIT_TCP value 20 notempty Finally, the CLI command system update rule must be entered so that the values in the rules are applied. |
For example, to allow a maximum of 20 connections per minute per IP address and port. For TCP, monitoring is restricted to ports 443 and 11115. All ports are monitored for UDP connections. |